
Electronic communication and collaboration services[1] such as Outlook.com, Skype, Gmail, Slack, and OneDrive carry valuable private and confidential communications that need protection. But these same services also provide a means for attackers to steal information or seize control of users’ computers for nefarious purposes, via viruses, worms, spam, phishing attacks, and other forms of malware.
Preventing the theft of user information and the dissemination of malware is a core feature of electronic communication and collaboration services. This requires significant processing of users’ communications and data both in-transit and after delivery. This processing can and should be done without compromising the user’s privacy or the confidentiality of their communications[2].
Message processing data flow:
To protect against malware distributed via electronic communications and collaboration systems such as email servers[3], the content follows a conceptually simple flow.

Starting with “A” the message is received by the recipient’s email service. The message’s envelope, as well as the message contents and any attachments, are passed on to the anti-malware portion of the email service (“B”) which determines whether or not the message is malware. Based on what the anti-malware service determines, the message is delivered to the user as appropriate (“C”). Some messages are determined to be malware with near certainty and are never delivered to the user. Instead they are deleted as quickly as possible[4]. Some messages are likely to be spam, however the service is not always certain. So the message is delivered to the user’s mailbox but into their spam/junk-mail folder. The remaining valid messages are delivered to the user’s inbox. The service can never determine with absolute certainty whether or not a message is malicious; it is always a probabilistic assessment. If the service is wrong either way; i.e. the user is exposed to malware or the user indicates that a message originally thought to be spam is not, the message may be added to a database of messages (“E”) used to train the next version of the anti-malware logic (“F”), thus permitting the system to “learn” over time and become more effective.
Clearly this entire process entails considerable processing of the messages. The types of processing are diverse and done in two key phases: message processing (“A” – “D”) and model building (“E” – “F”).
Anti-malware is particularly important for in-transit messages because attacks most typically enter the service through communications being transmitted. It is, however, also performed against already received and processed messages. As new attacks are identified – usually after the attack has been launched and some infected content has evaded the filters and been delivered to users – the anti-malware service is updated to defend against those attacks, and the service is rerun against recently delivered message to retroactively remove instances of said attack.
Processing message:
The types of processing done on messages to determine whether or not they are malicious include simple rules (e.g. messages without senders are likely not valid), reputations systems (messages from a certain set of IP addresses or senders are likely not valid, such as lists managed by the Spamhaus project[5]), digital thumbprints (comparing the thumbprint of the message or attachment to the thumbprints of known bad messages), honey pots (email addresses with no user and thus mailboxes that could never get any valid messages – anything delivered to them is spam or malware), and complex machine-learned models which process the contents of the message or the attachment[6]. As new forms of attack are encountered, new forms of defense must be quickly developed to keep users safe.
This requires processing of the message envelope, body, and attachment. For example:
- Message envelopes indicate not only the message recipient but also the supposed sender, and the server path which the message followed to reach the recipient. This is critical, not only to determine the recipient (needed to ensure the message is delivered to the intended recipients), but also to determine how probable it is that the sender is who they claim to be. It is common for attackers to “spoof” a sender, i.e. pretend they are a certain sender even though they are not. Knowing the path taken by the message can help determine if it has been sent by a spoof sender. For example, if a message originates from a trusted sending service which verifies the identity of the sender, then passes through a series of trusted intermediate services to the destination, the probability that the sender has been spoofed is much lower.
- Message bodies are among the most critical elements of the message which need to be processed to determine if the message is likely spam or a phishing attack. For example, text about “great deals on pharmaceuticals” is often indicative of spam. Without processing the body of the message, it is impossible to determine this. Attackers know that defenders watch out for such phrases, so they often try to hide them as text within an image. To the reader this looks similar, but defenders must run the images through optical character recognition algorithms to convert the images into text that can then be compared against a set of suspicious phrases. For example:
Another example of message body analysis is comparing the text of hyper-links to the URL. If a hyperlink’s text says “Click here to reset your Facebook password” but the URL points to “http://12345.contoso.com“, it is likely a phishing attack because Facebook password reset links should never be any URL other a correct Facebook one. Because most users do not check the URL before clicking on the hyperlink, it is important to protect them from such attacks. Without processing the message body, this is impossible.
- It is equally important to analyze attachments; otherwise attackers use them to deliver malicious payloads or contents to users. Attachments can be executables that open a user’s computer to attacker control. They can also be phishing attacks with the mismatched hyperlink text and URL scenario we described above embedded into the attachment. Any attack in the body of a message can appear in an attachment, and attachments can include additional forms of attack.
Model building:
Model building is the portion of machine learning in which the logic that does the evaluation is updated. It is the “learning” part of the machine learning; where the evaluation algorithm is updated based on new data so that it produces the desired output, not only based on data and results it has previous seen and been trained on, but also based on any new data or results.
The entire computer science sub-discipline of machine learning is the science of learning algorithms, and of this training phase, so a full treatise is beyond the scope of this paper. Generally speaking however, learning algorithms for detecting malware can be developed that respect the privacy of recipients because what is necessary is an understanding of the attack and the pattern of the attack, not the victims of that attack.
Privacy: data protection and confidentiality implications
Protecting the personal data of both sender and recipients, and communications confidentiality, during message processing (“A” – “D” above) can be done without diminishing the efficacy of the anti-malware service because that service acts as a stateless function. The service process the message and creates new metadata indicating whether or not the message should be delivered, without retaining any knowledge of the contents of the message and without exposing the message to anyone except the intended recipients. The recipient’s communication service processes and accesses the content on behalf of the recipient; and it is the recipient’s expectation to be protected against spam and malicious communications.. Failing to process every user’s every message would expose the entire service, and all its users, to known infections, which would be irresponsible.
Protecting personal data and confidentiality during the model building phase (“E” – “F” above) is done by a selection of algorithms and approaches that preserve privacy and confidentiality, those in which personal data is not retained or exposed (for example, selection of privacy preserving machine learning feature vectors), by restricting the use of the communication to building anti-malware capabilities[7], or by building user-specific models which solely benefit that user. The first two techniques have been used historically, but the third is becoming increasingly common as users’ expectations of what qualifies as nuisance communications (i.e. spam) become more individualized[8].
Using communication data for model building in anti-malware capabilities is done without explicit user consent. Malware is an ongoing struggle between attackers and the people providing the communications safety service, with attackers trying to find ways to get messages past the safety service. As new attacks emerge the safety service must respond quickly[9], using as much information as is available (which often necessitates sharing information with the anti-malware elements of other services). Attackers are increasingly using machine learning to create and launch attacks[10], requiring defenders to respond in kind with increasingly advanced machine learning-based defenses. One way to do this is to automate the creation of new versions of the anti-malware model so the service quickly inoculates all users against new attacks. The effectiveness of anti-malware depends on knowing about, and inoculating all users against, these attacks. This data can be used without exposing personal data or compromising confidentiality. All users of a service, and the entire service itself, are at risk if we fail to constantly process content in order to detect new forms of infection for every user. Similar to failing to inoculate a few members of a large population against an infectious disease, failing to process all users against these attacks would be irresponsible and would ultimately put the entire population at risk.
For anti-malware it important to note that the sender is generally malicious, and unlikely to grant consent to build better defenses against their attack. Requiring consent from all parties will make it impossible for services to provide a safe, secure, and nuisance-free communications and collaboration environment for all.
[1] It is difficult to differentiate between communication and collaboration, or between messages and other collaboration artifacts. Consider a document jointly authored by many people, each of whom leaves comments in the document to express ideas and input. Those same comments could be transmitted as email, chats, or through voice rather than comments in a document. Rather than treat them as separate, we recognize collaboration and communication as linked and refer to them interchangeably.
[2] Privacy, protection of personal data and confidentiality are frequently treated as synonymous, but we draw a distinction. For the purposes of this paper we treat data protection as the act of protecting knowledge of who a piece of data is about, and confidentiality as protecting that information. For example, consider a piece of data that indicates Bob is interested in buying a car. Data protection can be achieved by removing any knowledge that the data is about Bob; knowing simply that someone is interested in buying a car protects Bob’s privacy. Protecting confidentiality is preventing Bob’s data from being exposed to anyone but him. In this specific instance, Bob may only be concerned with protecting his personal data. However, if the information related to Microsoft’s interest in buying LinkedIn, Microsoft would be very interested in protecting the confidentiality of that data.
[3] Henceforth in this paper we will refer to this as an email service, but it is understood that similar problems and solutions apply to other communication and collaboration services.
[4] A staggering 77.8% of all messages sent to an email service are spam, with 90.4% of them being identified as such with sufficient certainty to prevent them ever being delivered to users.
[5] https://www.spamhaus.org/
[6] Use of machine learning in anti-spam services is one of the oldest, most pervasive, and most useful applications of that technology, dating back to at least 1998 (http://robotics.stanford.edu/users/sahami/papers-dir/spam.pdf)
[7] Services like Office365 that provide subscription-funded productivity services to users are incentivized to preserve the confidentiality of user data; the user is the customer, not the product.
[8] To my daughter, communications about new Lego toys are not a nuisance, they are interesting and desirable. However to me they are an imposition.
[9] Today, a typical spam campaign lasts under an hour. Yet in that time it gets through often enough to make it worthwhile to the attacker.
[10] https://erpscan.com/press-center/blog/machine-learning-for-cybercriminals
– Jim Kleewein, Technical Fellow, Microsoft

Electronic communication and collaboration services[1] such as Outlook.com, Skype, Gmail, Slack, and OneDrive carry valuable private and confidential communications that need protection. But these same services also provide a means for attackers to steal information or seize control of users’ computers for nefarious purposes, via viruses, worms, spam, phishing attacks, and other forms of malware.
Preventing the theft of user information and the dissemination of malware is a core feature of electronic communication and collaboration services. This requires significant processing of users’ communications and data both in-transit and after delivery. This processing can and should be done without compromising the user’s privacy or the confidentiality of their communications[2].
Message processing data flow:
To protect against malware distributed via electronic communications and collaboration systems such as email servers[3], the content follows a conceptually simple flow.

Starting with “A” the message is received by the recipient’s email service. The message’s envelope, as well as the message contents and any attachments, are passed on to the anti-malware portion of the email service (“B”) which determines whether or not the message is malware. Based on what the anti-malware service determines, the message is delivered to the user as appropriate (“C”). Some messages are determined to be malware with near certainty and are never delivered to the user. Instead they are deleted as quickly as possible[4]. Some messages are likely to be spam, however the service is not always certain. So the message is delivered to the user’s mailbox but into their spam/junk-mail folder. The remaining valid messages are delivered to the user’s inbox. The service can never determine with absolute certainty whether or not a message is malicious; it is always a probabilistic assessment. If the service is wrong either way; i.e. the user is exposed to malware or the user indicates that a message originally thought to be spam is not, the message may be added to a database of messages (“E”) used to train the next version of the anti-malware logic (“F”), thus permitting the system to “learn” over time and become more effective.
Clearly this entire process entails considerable processing of the messages. The types of processing are diverse and done in two key phases: message processing (“A” – “D”) and model building (“E” – “F”).
Anti-malware is particularly important for in-transit messages because attacks most typically enter the service through communications being transmitted. It is, however, also performed against already received and processed messages. As new attacks are identified – usually after the attack has been launched and some infected content has evaded the filters and been delivered to users – the anti-malware service is updated to defend against those attacks, and the service is rerun against recently delivered message to retroactively remove instances of said attack.
Processing message:
The types of processing done on messages to determine whether or not they are malicious include simple rules (e.g. messages without senders are likely not valid), reputations systems (messages from a certain set of IP addresses or senders are likely not valid, such as lists managed by the Spamhaus project[5]), digital thumbprints (comparing the thumbprint of the message or attachment to the thumbprints of known bad messages), honey pots (email addresses with no user and thus mailboxes that could never get any valid messages – anything delivered to them is spam or malware), and complex machine-learned models which process the contents of the message or the attachment[6]. As new forms of attack are encountered, new forms of defense must be quickly developed to keep users safe.
This requires processing of the message envelope, body, and attachment. For example:
- Message envelopes indicate not only the message recipient but also the supposed sender, and the server path which the message followed to reach the recipient. This is critical, not only to determine the recipient (needed to ensure the message is delivered to the intended recipients), but also to determine how probable it is that the sender is who they claim to be. It is common for attackers to “spoof” a sender, i.e. pretend they are a certain sender even though they are not. Knowing the path taken by the message can help determine if it has been sent by a spoof sender. For example, if a message originates from a trusted sending service which verifies the identity of the sender, then passes through a series of trusted intermediate services to the destination, the probability that the sender has been spoofed is much lower.
- Message bodies are among the most critical elements of the message which need to be processed to determine if the message is likely spam or a phishing attack. For example, text about “great deals on pharmaceuticals” is often indicative of spam. Without processing the body of the message, it is impossible to determine this. Attackers know that defenders watch out for such phrases, so they often try to hide them as text within an image. To the reader this looks similar, but defenders must run the images through optical character recognition algorithms to convert the images into text that can then be compared against a set of suspicious phrases. For example:
Another example of message body analysis is comparing the text of hyper-links to the URL. If a hyperlink’s text says “Click here to reset your Facebook password” but the URL points to “http://12345.contoso.com“, it is likely a phishing attack because Facebook password reset links should never be any URL other a correct Facebook one. Because most users do not check the URL before clicking on the hyperlink, it is important to protect them from such attacks. Without processing the message body, this is impossible.
- It is equally important to analyze attachments; otherwise attackers use them to deliver malicious payloads or contents to users. Attachments can be executables that open a user’s computer to attacker control. They can also be phishing attacks with the mismatched hyperlink text and URL scenario we described above embedded into the attachment. Any attack in the body of a message can appear in an attachment, and attachments can include additional forms of attack.
Model building:
Model building is the portion of machine learning in which the logic that does the evaluation is updated. It is the “learning” part of the machine learning; where the evaluation algorithm is updated based on new data so that it produces the desired output, not only based on data and results it has previous seen and been trained on, but also based on any new data or results.
The entire computer science sub-discipline of machine learning is the science of learning algorithms, and of this training phase, so a full treatise is beyond the scope of this paper. Generally speaking however, learning algorithms for detecting malware can be developed that respect the privacy of recipients because what is necessary is an understanding of the attack and the pattern of the attack, not the victims of that attack.
Privacy: data protection and confidentiality implications
Protecting the personal data of both sender and recipients, and communications confidentiality, during message processing (“A” – “D” above) can be done without diminishing the efficacy of the anti-malware service because that service acts as a stateless function. The service process the message and creates new metadata indicating whether or not the message should be delivered, without retaining any knowledge of the contents of the message and without exposing the message to anyone except the intended recipients. The recipient’s communication service processes and accesses the content on behalf of the recipient; and it is the recipient’s expectation to be protected against spam and malicious communications.. Failing to process every user’s every message would expose the entire service, and all its users, to known infections, which would be irresponsible.
Protecting personal data and confidentiality during the model building phase (“E” – “F” above) is done by a selection of algorithms and approaches that preserve privacy and confidentiality, those in which personal data is not retained or exposed (for example, selection of privacy preserving machine learning feature vectors), by restricting the use of the communication to building anti-malware capabilities[7], or by building user-specific models which solely benefit that user. The first two techniques have been used historically, but the third is becoming increasingly common as users’ expectations of what qualifies as nuisance communications (i.e. spam) become more individualized[8].
Using communication data for model building in anti-malware capabilities is done without explicit user consent. Malware is an ongoing struggle between attackers and the people providing the communications safety service, with attackers trying to find ways to get messages past the safety service. As new attacks emerge the safety service must respond quickly[9], using as much information as is available (which often necessitates sharing information with the anti-malware elements of other services). Attackers are increasingly using machine learning to create and launch attacks[10], requiring defenders to respond in kind with increasingly advanced machine learning-based defenses. One way to do this is to automate the creation of new versions of the anti-malware model so the service quickly inoculates all users against new attacks. The effectiveness of anti-malware depends on knowing about, and inoculating all users against, these attacks. This data can be used without exposing personal data or compromising confidentiality. All users of a service, and the entire service itself, are at risk if we fail to constantly process content in order to detect new forms of infection for every user. Similar to failing to inoculate a few members of a large population against an infectious disease, failing to process all users against these attacks would be irresponsible and would ultimately put the entire population at risk.
For anti-malware it important to note that the sender is generally malicious, and unlikely to grant consent to build better defenses against their attack. Requiring consent from all parties will make it impossible for services to provide a safe, secure, and nuisance-free communications and collaboration environment for all.
[1] It is difficult to differentiate between communication and collaboration, or between messages and other collaboration artifacts. Consider a document jointly authored by many people, each of whom leaves comments in the document to express ideas and input. Those same comments could be transmitted as email, chats, or through voice rather than comments in a document. Rather than treat them as separate, we recognize collaboration and communication as linked and refer to them interchangeably.
[2] Privacy, protection of personal data and confidentiality are frequently treated as synonymous, but we draw a distinction. For the purposes of this paper we treat data protection as the act of protecting knowledge of who a piece of data is about, and confidentiality as protecting that information. For example, consider a piece of data that indicates Bob is interested in buying a car. Data protection can be achieved by removing any knowledge that the data is about Bob; knowing simply that someone is interested in buying a car protects Bob’s privacy. Protecting confidentiality is preventing Bob’s data from being exposed to anyone but him. In this specific instance, Bob may only be concerned with protecting his personal data. However, if the information related to Microsoft’s interest in buying LinkedIn, Microsoft would be very interested in protecting the confidentiality of that data.
[3] Henceforth in this paper we will refer to this as an email service, but it is understood that similar problems and solutions apply to other communication and collaboration services.
[4] A staggering 77.8% of all messages sent to an email service are spam, with 90.4% of them being identified as such with sufficient certainty to prevent them ever being delivered to users.
[5] https://www.spamhaus.org/
[6] Use of machine learning in anti-spam services is one of the oldest, most pervasive, and most useful applications of that technology, dating back to at least 1998 (http://robotics.stanford.edu/users/sahami/papers-dir/spam.pdf)
[7] Services like Office365 that provide subscription-funded productivity services to users are incentivized to preserve the confidentiality of user data; the user is the customer, not the product.
[8] To my daughter, communications about new Lego toys are not a nuisance, they are interesting and desirable. However to me they are an imposition.
[9] Today, a typical spam campaign lasts under an hour. Yet in that time it gets through often enough to make it worthwhile to the attacker.
[10] https://erpscan.com/press-center/blog/machine-learning-for-cybercriminals
– Jim Kleewein, Technical Fellow, Microsoft

Electronic communication and collaboration services[1] such as Outlook.com, Skype, Gmail, Slack, and OneDrive carry valuable private and confidential communications that need protection. But these same services also provide a means for attackers to steal information or seize control of users’ computers for nefarious purposes, via viruses, worms, spam, phishing attacks, and other forms of malware.
Preventing the theft of user information and the dissemination of malware is a core feature of electronic communication and collaboration services. This requires significant processing of users’ communications and data both in-transit and after delivery. This processing can and should be done without compromising the user’s privacy or the confidentiality of their communications[2].
Message processing data flow:
To protect against malware distributed via electronic communications and collaboration systems such as email servers[3], the content follows a conceptually simple flow.

Starting with “A” the message is received by the recipient’s email service. The message’s envelope, as well as the message contents and any attachments, are passed on to the anti-malware portion of the email service (“B”) which determines whether or not the message is malware. Based on what the anti-malware service determines, the message is delivered to the user as appropriate (“C”). Some messages are determined to be malware with near certainty and are never delivered to the user. Instead they are deleted as quickly as possible[4]. Some messages are likely to be spam, however the service is not always certain. So the message is delivered to the user’s mailbox but into their spam/junk-mail folder. The remaining valid messages are delivered to the user’s inbox. The service can never determine with absolute certainty whether or not a message is malicious; it is always a probabilistic assessment. If the service is wrong either way; i.e. the user is exposed to malware or the user indicates that a message originally thought to be spam is not, the message may be added to a database of messages (“E”) used to train the next version of the anti-malware logic (“F”), thus permitting the system to “learn” over time and become more effective.
Clearly this entire process entails considerable processing of the messages. The types of processing are diverse and done in two key phases: message processing (“A” – “D”) and model building (“E” – “F”).
Anti-malware is particularly important for in-transit messages because attacks most typically enter the service through communications being transmitted. It is, however, also performed against already received and processed messages. As new attacks are identified – usually after the attack has been launched and some infected content has evaded the filters and been delivered to users – the anti-malware service is updated to defend against those attacks, and the service is rerun against recently delivered message to retroactively remove instances of said attack.
Processing message:
The types of processing done on messages to determine whether or not they are malicious include simple rules (e.g. messages without senders are likely not valid), reputations systems (messages from a certain set of IP addresses or senders are likely not valid, such as lists managed by the Spamhaus project[5]), digital thumbprints (comparing the thumbprint of the message or attachment to the thumbprints of known bad messages), honey pots (email addresses with no user and thus mailboxes that could never get any valid messages – anything delivered to them is spam or malware), and complex machine-learned models which process the contents of the message or the attachment[6]. As new forms of attack are encountered, new forms of defense must be quickly developed to keep users safe.
This requires processing of the message envelope, body, and attachment. For example:
- Message envelopes indicate not only the message recipient but also the supposed sender, and the server path which the message followed to reach the recipient. This is critical, not only to determine the recipient (needed to ensure the message is delivered to the intended recipients), but also to determine how probable it is that the sender is who they claim to be. It is common for attackers to “spoof” a sender, i.e. pretend they are a certain sender even though they are not. Knowing the path taken by the message can help determine if it has been sent by a spoof sender. For example, if a message originates from a trusted sending service which verifies the identity of the sender, then passes through a series of trusted intermediate services to the destination, the probability that the sender has been spoofed is much lower.
- Message bodies are among the most critical elements of the message which need to be processed to determine if the message is likely spam or a phishing attack. For example, text about “great deals on pharmaceuticals” is often indicative of spam. Without processing the body of the message, it is impossible to determine this. Attackers know that defenders watch out for such phrases, so they often try to hide them as text within an image. To the reader this looks similar, but defenders must run the images through optical character recognition algorithms to convert the images into text that can then be compared against a set of suspicious phrases. For example:
Another example of message body analysis is comparing the text of hyper-links to the URL. If a hyperlink’s text says “Click here to reset your Facebook password” but the URL points to “http://12345.contoso.com“, it is likely a phishing attack because Facebook password reset links should never be any URL other a correct Facebook one. Because most users do not check the URL before clicking on the hyperlink, it is important to protect them from such attacks. Without processing the message body, this is impossible.
- It is equally important to analyze attachments; otherwise attackers use them to deliver malicious payloads or contents to users. Attachments can be executables that open a user’s computer to attacker control. They can also be phishing attacks with the mismatched hyperlink text and URL scenario we described above embedded into the attachment. Any attack in the body of a message can appear in an attachment, and attachments can include additional forms of attack.
Model building:
Model building is the portion of machine learning in which the logic that does the evaluation is updated. It is the “learning” part of the machine learning; where the evaluation algorithm is updated based on new data so that it produces the desired output, not only based on data and results it has previous seen and been trained on, but also based on any new data or results.
The entire computer science sub-discipline of machine learning is the science of learning algorithms, and of this training phase, so a full treatise is beyond the scope of this paper. Generally speaking however, learning algorithms for detecting malware can be developed that respect the privacy of recipients because what is necessary is an understanding of the attack and the pattern of the attack, not the victims of that attack.
Privacy: data protection and confidentiality implications
Protecting the personal data of both sender and recipients, and communications confidentiality, during message processing (“A” – “D” above) can be done without diminishing the efficacy of the anti-malware service because that service acts as a stateless function. The service process the message and creates new metadata indicating whether or not the message should be delivered, without retaining any knowledge of the contents of the message and without exposing the message to anyone except the intended recipients. The recipient’s communication service processes and accesses the content on behalf of the recipient; and it is the recipient’s expectation to be protected against spam and malicious communications.. Failing to process every user’s every message would expose the entire service, and all its users, to known infections, which would be irresponsible.
Protecting personal data and confidentiality during the model building phase (“E” – “F” above) is done by a selection of algorithms and approaches that preserve privacy and confidentiality, those in which personal data is not retained or exposed (for example, selection of privacy preserving machine learning feature vectors), by restricting the use of the communication to building anti-malware capabilities[7], or by building user-specific models which solely benefit that user. The first two techniques have been used historically, but the third is becoming increasingly common as users’ expectations of what qualifies as nuisance communications (i.e. spam) become more individualized[8].
Using communication data for model building in anti-malware capabilities is done without explicit user consent. Malware is an ongoing struggle between attackers and the people providing the communications safety service, with attackers trying to find ways to get messages past the safety service. As new attacks emerge the safety service must respond quickly[9], using as much information as is available (which often necessitates sharing information with the anti-malware elements of other services). Attackers are increasingly using machine learning to create and launch attacks[10], requiring defenders to respond in kind with increasingly advanced machine learning-based defenses. One way to do this is to automate the creation of new versions of the anti-malware model so the service quickly inoculates all users against new attacks. The effectiveness of anti-malware depends on knowing about, and inoculating all users against, these attacks. This data can be used without exposing personal data or compromising confidentiality. All users of a service, and the entire service itself, are at risk if we fail to constantly process content in order to detect new forms of infection for every user. Similar to failing to inoculate a few members of a large population against an infectious disease, failing to process all users against these attacks would be irresponsible and would ultimately put the entire population at risk.
For anti-malware it important to note that the sender is generally malicious, and unlikely to grant consent to build better defenses against their attack. Requiring consent from all parties will make it impossible for services to provide a safe, secure, and nuisance-free communications and collaboration environment for all.
[1] It is difficult to differentiate between communication and collaboration, or between messages and other collaboration artifacts. Consider a document jointly authored by many people, each of whom leaves comments in the document to express ideas and input. Those same comments could be transmitted as email, chats, or through voice rather than comments in a document. Rather than treat them as separate, we recognize collaboration and communication as linked and refer to them interchangeably.
[2] Privacy, protection of personal data and confidentiality are frequently treated as synonymous, but we draw a distinction. For the purposes of this paper we treat data protection as the act of protecting knowledge of who a piece of data is about, and confidentiality as protecting that information. For example, consider a piece of data that indicates Bob is interested in buying a car. Data protection can be achieved by removing any knowledge that the data is about Bob; knowing simply that someone is interested in buying a car protects Bob’s privacy. Protecting confidentiality is preventing Bob’s data from being exposed to anyone but him. In this specific instance, Bob may only be concerned with protecting his personal data. However, if the information related to Microsoft’s interest in buying LinkedIn, Microsoft would be very interested in protecting the confidentiality of that data.
[3] Henceforth in this paper we will refer to this as an email service, but it is understood that similar problems and solutions apply to other communication and collaboration services.
[4] A staggering 77.8% of all messages sent to an email service are spam, with 90.4% of them being identified as such with sufficient certainty to prevent them ever being delivered to users.
[5] https://www.spamhaus.org/
[6] Use of machine learning in anti-spam services is one of the oldest, most pervasive, and most useful applications of that technology, dating back to at least 1998 (http://robotics.stanford.edu/users/sahami/papers-dir/spam.pdf)
[7] Services like Office365 that provide subscription-funded productivity services to users are incentivized to preserve the confidentiality of user data; the user is the customer, not the product.
[8] To my daughter, communications about new Lego toys are not a nuisance, they are interesting and desirable. However to me they are an imposition.
[9] Today, a typical spam campaign lasts under an hour. Yet in that time it gets through often enough to make it worthwhile to the attacker.
[10] https://erpscan.com/press-center/blog/machine-learning-for-cybercriminals
– Jim Kleewein, Technical Fellow, Microsoft

The following is provided from Microsoft Security and Compliance blogs at TechCommunity:
Last September, we announced new capabilities in Office 365 Message Encryption that enable users to seamlessly collaborate on protected emails with anyone. This release included Do Not Forward an out-of-the-box policy that encrypts emails and Office attachments, and restricts the content and email from being forwarded, printed or copied.
Today, we are happy to share that we are releasing another out-of-the-box policy called encrypt only. With the encrypt-only policy, users can send encrypted email to any recipient, whether they are inside or outside the organization, and the protection follows the lifecycle of the email. That means recipients can copy, print and forward the email, and encryption will not be removed. This new policy provides more flexibility in the type of protection that can be applied to your sensitive emails.
This is valuable for organizations that want persistent encryption, but do not want to add additional restrictions. For example, a doctor looking to protect an email containing sensitive personal information, can apply the encrypt-only policy, and the patient receiving the email can easily consume the protected message regardless of their email provider, and forward that email to another trusted party.
With this new, flexible policy, users and admins can apply different levels of protection to best fit their data protection needs.
Read more to understand what the encrypt-only policy looks like and how to apply the policy.
How the encrypt-only policy works
The encrypt-only policy is an out-of-the box policy that can be used without additional configuration, and as the name suggests, only applies encryption to the email. You can apply the policy through end-user controls in Outlook or through automatic admin managed controls in the Exchange admin center. Users can apply this policy to individual emails through end-user controls in Outlook, and Admins can apply this policy automatically to any email that matches the set criteria through admin-managed controls in the Exchange admin center.
Customers that have enabled the new Office 365 Message Encryption capabilities will see the encrypt-only policy first through Outlook on the web and in the Exchange admin center under mail flow rules. Updates to Outlook for Windows and Outlook for Mac are planned for the coming months.
How to send an email with the encrypt-only policy in Outlook on the web
Users can apply protection with the encrypt-only policy by clicking on the protect button and changing the permissions to just encrypt. While the other options encrypt the message, the encrypt option will apply the encrypt-only policy to the message, therefore enabling recipients to forward, copy and print the message.
Applying this option will offer added flexibility for recipients to share the email with other trusted parties while encryption continues to persist and throughout the lifecycle of the email.
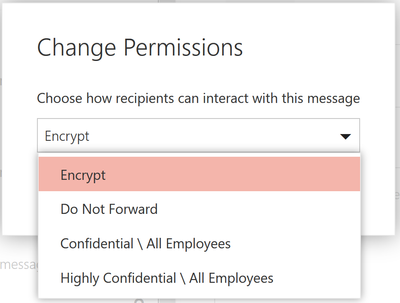 In Outlook on the web, users can click on the protect button to change the permissions of the email. Once a user clicks on protect, the users can click on encrypt, to only encrypt the email.
In Outlook on the web, users can click on the protect button to change the permissions of the email. Once a user clicks on protect, the users can click on encrypt, to only encrypt the email.  Once the encrypt-only policy is applied, the user will see a notification that encryption has been applied.
Once the encrypt-only policy is applied, the user will see a notification that encryption has been applied.
How to apply the encrypt-only policy through Exchange mail flow rules
As an administrator, you can apply the encrypt-only policy automatically to emails that meet certain conditions by creating a mail flow rule. When you do this, email affected by the encrypt-only policy is encrypted in transport by Office 365.
For instructions on creating a mail flow rule that employs the encrypt-only policy, see define mail flow rules to encrypt email messages in Office 365.
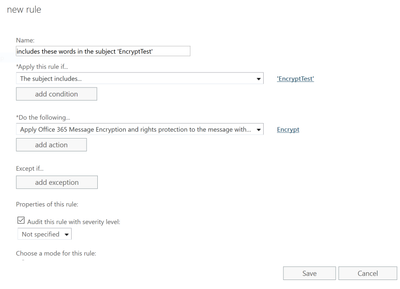 You as an administrator can create new mail flow rule to automatically apply the encrypt-only policy to emails.
You as an administrator can create new mail flow rule to automatically apply the encrypt-only policy to emails.
How to read encrypt-only email using Outlook on the web and Outlook mobile
Office 365 recipients can easily read and reply to emails that have been applied with the encrypt-only policy using Outlook on the web and Outlook mobile directly from the client.
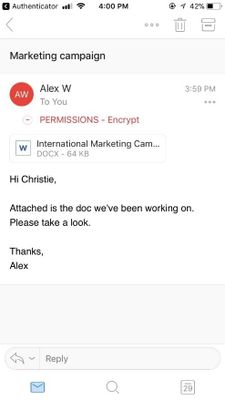 Users can read the encrypted message natively directly in Outlook on the web and Outlook mobile.
Users can read the encrypted message natively directly in Outlook on the web and Outlook mobile.
The inline reading experience for Outlook desktop (Windows and Mac) will be available in the coming months. In the meantime, Office 365 users using Outlook desktop will see the encrypted mail as an html mail with an rpmsg_v2 attachment.
How to read encrypt-only emails for non-Office 365 users (on-prem, Gmail, and Outlook.com users)
Non-Office 365 users, receive an html mail with an rpmsg_v4 attachment. Once they click Read Message they are redirected to the Office 365 Message Encryption portal where they can reply, forward, print, or take other allowed actions. More information can be found in this article.
Get started!
The new encrypt-only policy rolls out starting today as part of Office 365 Message Encryption.
Office 365 Message Encryption is offered in Office 365 E3 and E5, or as an add-on -you can find the full list of where Office 365 Message Encryption is offered here.
Please let us know what you think here or give us your feedback on uservoice!
The above was provided from Microsoft Security and Compliance blogs at TechCommunity

Last September, we announced new capabilities in Office 365 Message Encryption that enable users to seamlessly collaborate on protected emails with anyone. This release included Do Not Forward an out-of-the-box policy that encrypts emails and Office attachments, and restricts the content and email from being forwarded, printed or copied.
Today, we are happy to share that we are releasing another out-of-the-box policy called encrypt only. With the encrypt-only policy, users can send encrypted email to any recipient, whether they are inside or outside the organization, and the protection follows the lifecycle of the email. That means recipients can copy, print and forward the email, and encryption will not be removed. This new policy provides more flexibility in the type of protection that can be applied to your sensitive emails.
This is valuable for organizations that want persistent encryption, but do not want to add additional restrictions. For example, a doctor looking to protect an email containing sensitive personal information, can apply the encrypt-only policy, and the patient receiving the email can easily consume the protected message regardless of their email provider, and forward that email to another trusted party.
With this new, flexible policy, users and admins can apply different levels of protection to best fit their data protection needs.
Read more to understand what the encrypt-only policy looks like and how to apply the policy.
How the encrypt-only policy works
The encrypt-only policy is an out-of-the box policy that can be used without additional configuration, and as the name suggests, only applies encryption to the email. You can apply the policy through end-user controls in Outlook or through automatic admin managed controls in the Exchange admin center. Users can apply this policy to individual emails through end-user controls in Outlook, and Admins can apply this policy automatically to any email that matches the set criteria through admin-managed controls in the Exchange admin center.
Customers that have enabled the new Office 365 Message Encryption capabilities will see the encrypt-only policy first through Outlook on the web and in the Exchange admin center under mail flow rules. Updates to Outlook for Windows and Outlook for Mac are planned for the coming months.
How to send an email with the encrypt-only policy in Outlook on the web
Users can apply protection with the encrypt-only policy by clicking on the protect button and changing the permissions to just encrypt. While the other options encrypt the message, the encrypt option will apply the encrypt-only policy to the message, therefore enabling recipients to forward, copy and print the message.
Applying this option will offer added flexibility for recipients to share the email with other trusted parties while encryption continues to persist and throughout the lifecycle of the email.
 In Outlook on the web, users can click on the protect button to change the permissions of the email. Once a user clicks on protect, the users can click on encrypt, to only encrypt the email.
In Outlook on the web, users can click on the protect button to change the permissions of the email. Once a user clicks on protect, the users can click on encrypt, to only encrypt the email.  Once the encrypt-only policy is applied, the user will see a notification that encryption has been applied.
Once the encrypt-only policy is applied, the user will see a notification that encryption has been applied.
How to apply the encrypt-only policy through Exchange mail flow rules
As an administrator, you can apply the encrypt-only policy automatically to emails that meet certain conditions by creating a mail flow rule. When you do this, email affected by the encrypt-only policy is encrypted in transport by Office 365.
For instructions on creating a mail flow rule that employs the encrypt-only policy, see define mail flow rules to encrypt email messages in Office 365.
 You as an administrator can create new mail flow rule to automatically apply the encrypt-only policy to emails.
You as an administrator can create new mail flow rule to automatically apply the encrypt-only policy to emails.
How to read encrypt-only email using Outlook on the web and Outlook mobile
Office 365 recipients can easily read and reply to emails that have been applied with the encrypt-only policy using Outlook on the web and Outlook mobile directly from the client.
 Users can read the encrypted message natively directly in Outlook on the web and Outlook mobile.
Users can read the encrypted message natively directly in Outlook on the web and Outlook mobile.
The inline reading experience for Outlook desktop (Windows and Mac) will be available in the coming months. In the meantime, Office 365 users using Outlook desktop will see the encrypted mail as an html mail with an rpmsg_v2 attachment.
How to read encrypt-only emails for non-Office 365 users (on-prem, Gmail, and Outlook.com users)
Non-Office 365 users, receive an html mail with an rpmsg_v4 attachment. Once they click Read Message they are redirected to the Office 365 Message Encryption portal where they can reply, forward, print, or take other allowed actions. More information can be found in this article.
Get started!
The new encrypt-only policy rolls out starting today as part of Office 365 Message Encryption.
Office 365 Message Encryption is offered in Office 365 E3 and E5, or as an add-on -you can find the full list of where Office 365 Message Encryption is offered here.
Please let us know what you think here or give us your feedback on uservoice!

Last September, we announced new capabilities in Office 365 Message Encryption that enable users to seamlessly collaborate on protected emails with anyone. This release included Do Not Forward an out-of-the-box policy that encrypts emails and Office attachments, and restricts the content and email from being forwarded, printed or copied.
Today, we are happy to share that we are releasing another out-of-the-box policy called encrypt only. With the encrypt-only policy, users can send encrypted email to any recipient, whether they are inside or outside the organization, and the protection follows the lifecycle of the email. That means recipients can copy, print and forward the email, and encryption will not be removed. This new policy provides more flexibility in the type of protection that can be applied to your sensitive emails.
This is valuable for organizations that want persistent encryption, but do not want to add additional restrictions. For example, a doctor looking to protect an email containing sensitive personal information, can apply the encrypt-only policy, and the patient receiving the email can easily consume the protected message regardless of their email provider, and forward that email to another trusted party.
With this new, flexible policy, users and admins can apply different levels of protection to best fit their data protection needs.
Read more to understand what the encrypt-only policy looks like and how to apply the policy.
How the encrypt-only policy works
The encrypt-only policy is an out-of-the box policy that can be used without additional configuration, and as the name suggests, only applies encryption to the email. You can apply the policy through end-user controls in Outlook or through automatic admin managed controls in the Exchange admin center. Users can apply this policy to individual emails through end-user controls in Outlook, and Admins can apply this policy automatically to any email that matches the set criteria through admin-managed controls in the Exchange admin center.
Customers that have enabled the new Office 365 Message Encryption capabilities will see the encrypt-only policy first through Outlook on the web and in the Exchange admin center under mail flow rules. Updates to Outlook for Windows and Outlook for Mac are planned for the coming months.
How to send an email with the encrypt-only policy in Outlook on the web
Users can apply protection with the encrypt-only policy by clicking on the protect button and changing the permissions to just encrypt. While the other options encrypt the message, the encrypt option will apply the encrypt-only policy to the message, therefore enabling recipients to forward, copy and print the message.
Applying this option will offer added flexibility for recipients to share the email with other trusted parties while encryption continues to persist and throughout the lifecycle of the email.
 In Outlook on the web, users can click on the protect button to change the permissions of the email. Once a user clicks on protect, the users can click on encrypt, to only encrypt the email.
In Outlook on the web, users can click on the protect button to change the permissions of the email. Once a user clicks on protect, the users can click on encrypt, to only encrypt the email.  Once the encrypt-only policy is applied, the user will see a notification that encryption has been applied.
Once the encrypt-only policy is applied, the user will see a notification that encryption has been applied.
How to apply the encrypt-only policy through Exchange mail flow rules
As an administrator, you can apply the encrypt-only policy automatically to emails that meet certain conditions by creating a mail flow rule. When you do this, email affected by the encrypt-only policy is encrypted in transport by Office 365.
For instructions on creating a mail flow rule that employs the encrypt-only policy, see define mail flow rules to encrypt email messages in Office 365.
 You as an administrator can create new mail flow rule to automatically apply the encrypt-only policy to emails.
You as an administrator can create new mail flow rule to automatically apply the encrypt-only policy to emails.
How to read encrypt-only email using Outlook on the web and Outlook mobile
Office 365 recipients can easily read and reply to emails that have been applied with the encrypt-only policy using Outlook on the web and Outlook mobile directly from the client.
 Users can read the encrypted message natively directly in Outlook on the web and Outlook mobile.
Users can read the encrypted message natively directly in Outlook on the web and Outlook mobile.
The inline reading experience for Outlook desktop (Windows and Mac) will be available in the coming months. In the meantime, Office 365 users using Outlook desktop will see the encrypted mail as an html mail with an rpmsg_v2 attachment.
How to read encrypt-only emails for non-Office 365 users (on-prem, Gmail, and Outlook.com users)
Non-Office 365 users, receive an html mail with an rpmsg_v4 attachment. Once they click Read Message they are redirected to the Office 365 Message Encryption portal where they can reply, forward, print, or take other allowed actions. More information can be found in this article.
Get started!
The new encrypt-only policy rolls out starting today as part of Office 365 Message Encryption.
Office 365 Message Encryption is offered in Office 365 E3 and E5, or as an add-on -you can find the full list of where Office 365 Message Encryption is offered here.
Please let us know what you think here or give us your feedback on uservoice!

Last September, we announced new capabilities in Office 365 Message Encryption that enable users to seamlessly collaborate on protected emails with anyone. This release included Do Not Forward an out-of-the-box policy that encrypts emails and Office attachments, and restricts the content and email from being forwarded, printed or copied.
Today, we are happy to share that we are releasing another out-of-the-box policy called encrypt only. With the encrypt-only policy, users can send encrypted email to any recipient, whether they are inside or outside the organization, and the protection follows the lifecycle of the email. That means recipients can copy, print and forward the email, and encryption will not be removed. This new policy provides more flexibility in the type of protection that can be applied to your sensitive emails.
This is valuable for organizations that want persistent encryption, but do not want to add additional restrictions. For example, a doctor looking to protect an email containing sensitive personal information, can apply the encrypt-only policy, and the patient receiving the email can easily consume the protected message regardless of their email provider, and forward that email to another trusted party.
With this new, flexible policy, users and admins can apply different levels of protection to best fit their data protection needs.
Read more to understand what the encrypt-only policy looks like and how to apply the policy.
How the encrypt-only policy works
The encrypt-only policy is an out-of-the box policy that can be used without additional configuration, and as the name suggests, only applies encryption to the email. You can apply the policy through end-user controls in Outlook or through automatic admin managed controls in the Exchange admin center. Users can apply this policy to individual emails through end-user controls in Outlook, and Admins can apply this policy automatically to any email that matches the set criteria through admin-managed controls in the Exchange admin center.
Customers that have enabled the new Office 365 Message Encryption capabilities will see the encrypt-only policy first through Outlook on the web and in the Exchange admin center under mail flow rules. Updates to Outlook for Windows and Outlook for Mac are planned for the coming months.
How to send an email with the encrypt-only policy in Outlook on the web
Users can apply protection with the encrypt-only policy by clicking on the protect button and changing the permissions to just encrypt. While the other options encrypt the message, the encrypt option will apply the encrypt-only policy to the message, therefore enabling recipients to forward, copy and print the message.
Applying this option will offer added flexibility for recipients to share the email with other trusted parties while encryption continues to persist and throughout the lifecycle of the email.
 In Outlook on the web, users can click on the protect button to change the permissions of the email. Once a user clicks on protect, the users can click on encrypt, to only encrypt the email.
In Outlook on the web, users can click on the protect button to change the permissions of the email. Once a user clicks on protect, the users can click on encrypt, to only encrypt the email.  Once the encrypt-only policy is applied, the user will see a notification that encryption has been applied.
Once the encrypt-only policy is applied, the user will see a notification that encryption has been applied.
How to apply the encrypt-only policy through Exchange mail flow rules
As an administrator, you can apply the encrypt-only policy automatically to emails that meet certain conditions by creating a mail flow rule. When you do this, email affected by the encrypt-only policy is encrypted in transport by Office 365.
For instructions on creating a mail flow rule that employs the encrypt-only policy, see define mail flow rules to encrypt email messages in Office 365.
 You as an administrator can create new mail flow rule to automatically apply the encrypt-only policy to emails.
You as an administrator can create new mail flow rule to automatically apply the encrypt-only policy to emails.
How to read encrypt-only email using Outlook on the web and Outlook mobile
Office 365 recipients can easily read and reply to emails that have been applied with the encrypt-only policy using Outlook on the web and Outlook mobile directly from the client.
 Users can read the encrypted message natively directly in Outlook on the web and Outlook mobile.
Users can read the encrypted message natively directly in Outlook on the web and Outlook mobile.
The inline reading experience for Outlook desktop (Windows and Mac) will be available in the coming months. In the meantime, Office 365 users using Outlook desktop will see the encrypted mail as an html mail with an rpmsg_v2 attachment.
How to read encrypt-only emails for non-Office 365 users (on-prem, Gmail, and Outlook.com users)
Non-Office 365 users, receive an html mail with an rpmsg_v4 attachment. Once they click Read Message they are redirected to the Office 365 Message Encryption portal where they can reply, forward, print, or take other allowed actions. More information can be found in this article.
Get started!
The new encrypt-only policy rolls out starting today as part of Office 365 Message Encryption.
Office 365 Message Encryption is offered in Office 365 E3 and E5, or as an add-on -you can find the full list of where Office 365 Message Encryption is offered here.
Please let us know what you think here or give us your feedback on uservoice!

Last September, we announced new capabilities in Office 365 Message Encryption that enable users to seamlessly collaborate on protected emails with anyone. This release included Do Not Forward an out-of-the-box policy that encrypts emails and Office attachments, and restricts the content and email from being forwarded, printed or copied.
Today, we are happy to share that we are releasing another out-of-the-box policy called encrypt only. With the encrypt-only policy, users can send encrypted email to any recipient, whether they are inside or outside the organization, and the protection follows the lifecycle of the email. That means recipients can copy, print and forward the email, and encryption will not be removed. This new policy provides more flexibility in the type of protection that can be applied to your sensitive emails.
This is valuable for organizations that want persistent encryption, but do not want to add additional restrictions. For example, a doctor looking to protect an email containing sensitive personal information, can apply the encrypt-only policy, and the patient receiving the email can easily consume the protected message regardless of their email provider, and forward that email to another trusted party.
With this new, flexible policy, users and admins can apply different levels of protection to best fit their data protection needs.
Read more to understand what the encrypt-only policy looks like and how to apply the policy.
How the encrypt-only policy works
The encrypt-only policy is an out-of-the box policy that can be used without additional configuration, and as the name suggests, only applies encryption to the email. You can apply the policy through end-user controls in Outlook or through automatic admin managed controls in the Exchange admin center. Users can apply this policy to individual emails through end-user controls in Outlook, and Admins can apply this policy automatically to any email that matches the set criteria through admin-managed controls in the Exchange admin center.
Customers that have enabled the new Office 365 Message Encryption capabilities will see the encrypt-only policy first through Outlook on the web and in the Exchange admin center under mail flow rules. Updates to Outlook for Windows and Outlook for Mac are planned for the coming months.
How to send an email with the encrypt-only policy in Outlook on the web
Users can apply protection with the encrypt-only policy by clicking on the protect button and changing the permissions to just encrypt. While the other options encrypt the message, the encrypt option will apply the encrypt-only policy to the message, therefore enabling recipients to forward, copy and print the message.
Applying this option will offer added flexibility for recipients to share the email with other trusted parties while encryption continues to persist and throughout the lifecycle of the email.
 In Outlook on the web, users can click on the protect button to change the permissions of the email. Once a user clicks on protect, the users can click on encrypt, to only encrypt the email.
In Outlook on the web, users can click on the protect button to change the permissions of the email. Once a user clicks on protect, the users can click on encrypt, to only encrypt the email.  Once the encrypt-only policy is applied, the user will see a notification that encryption has been applied.
Once the encrypt-only policy is applied, the user will see a notification that encryption has been applied.
How to apply the encrypt-only policy through Exchange mail flow rules
As an administrator, you can apply the encrypt-only policy automatically to emails that meet certain conditions by creating a mail flow rule. When you do this, email affected by the encrypt-only policy is encrypted in transport by Office 365.
For instructions on creating a mail flow rule that employs the encrypt-only policy, see define mail flow rules to encrypt email messages in Office 365.
 You as an administrator can create new mail flow rule to automatically apply the encrypt-only policy to emails.
You as an administrator can create new mail flow rule to automatically apply the encrypt-only policy to emails.
How to read encrypt-only email using Outlook on the web and Outlook mobile
Office 365 recipients can easily read and reply to emails that have been applied with the encrypt-only policy using Outlook on the web and Outlook mobile directly from the client.
 Users can read the encrypted message natively directly in Outlook on the web and Outlook mobile.
Users can read the encrypted message natively directly in Outlook on the web and Outlook mobile.
The inline reading experience for Outlook desktop (Windows and Mac) will be available in the coming months. In the meantime, Office 365 users using Outlook desktop will see the encrypted mail as an html mail with an rpmsg_v2 attachment.
How to read encrypt-only emails for non-Office 365 users (on-prem, Gmail, and Outlook.com users)
Non-Office 365 users, receive an html mail with an rpmsg_v4 attachment. Once they click Read Message they are redirected to the Office 365 Message Encryption portal where they can reply, forward, print, or take other allowed actions. More information can be found in this article.
Get started!
The new encrypt-only policy rolls out starting today as part of Office 365 Message Encryption.
Office 365 Message Encryption is offered in Office 365 E3 and E5, or as an add-on -you can find the full list of where Office 365 Message Encryption is offered here.
Please let us know what you think here or give us your feedback on uservoice!

Microsoft has released a tool, called SARA, that can help diagnose issues with Office 365. Currently, its configured to help setting up Outlook with Office365.
SARA is the Support and Recovery Assistant for Office365, and can help diagnose issues from you entering the Office365 account, and then using the Support topic options to get help with. SARA is an on-demand application, so it only needs to be used when there is a problem indicated. Of course, access to the Office365 tenant will be required to use this tool! Its early days for SARA as I write this quick blog,, but, I guess it would be useful to keep an eye on this tool, as Microsoft continues to upgrade it to help support issues with other products in the Office365 suite.
Check the below video for more information, and download link is below the video.
When delivering an Office 365 service, you will need to ensure that the customer has access to resources to help them understand and get up to speed. As seen with SharePoint ‘getting the users on-board’, there is always a danger of ‘recreating’ adoption content, simply because information is non-centralised – that also means having to spend time gathering and crafting that content so that it is visually appealing (for example)..
(more…)

Introduction
If you run and/or own an Office365 tenant, you are guaranteed 99.9% uptime, you get a Service Health Dashboard, and you can see a Planned Maintenance Schedule.
Whilst these features are crucial to ensuring a resilient platform that gives visibility of status, it is important to recognise that there is another support plan which addresses compliance – particularly when it comes to who is responsible for the service, protection of connection and encryption.
Office 365 (enterprise version) offers enhanced versions of Microsoft Exchange Online, Microsoft SharePoint Online, and Microsoft Lync Online dedicated support plans that are designed to support the security, privacy, and regulatory compliance meeting the following:
• U.S. federal government agencies requiring certification under the Federal Information Security Management Act (FISMA) of 2002.
• Commercial entities subject to International Traffic in Arms Regulations (ITAR).
This document describes the advanced security and privacy features that are available in the ITAR-support plans from Office 365.
It also calls out any significant feature differences between Office 365 ITAR-support plan solutions and Office 365 dedicated plan solutions.
What is ITAR
Microsoft Office 365 ITAR-support plans are a variation of the Microsoft Office 365 dedicated plans. The primary difference is that ITAR-support plan solutions are designed to meet the security, privacy, and regulatory FISMA/FedRAMP compliance requirements for U.S. federal government agencies and support the regulatory needs of companies operating under ITAR.
These enhanced services are offered to customers under the Office 365 ITAR-support subscription plans (“ITAR-support plans”).
The ITAR dedicated support plan attempts to address frustrations of having to deal with generic (raise a support call into a ‘global queue’) helpdesk tickets regarding compliance and security. Another benefit of this support plan is the ability for those providing Office365 to help the customer build SLAs and at the same time provides more confidence in the use of online systems. Since ITAR is specific, the support resources applied will be closer to the relevant issues and will define solutions specific to those relevant issues.
Summary of ITAR
Data Protection
Encryption at Rest and Encryption in Transit
Encryption at Rest and Encryption in Transit is covered, describing that documents would be encrypted using AD RMS. Effectively, this means that users would access AD RMS documents using AD authentication. Note that Encryption at Rest only applies to Exchange and SharePoint Online. As for Encryption in Transit, there is a description concerning dedicated and Internet Connectivity.
Environment and Customer Isolation
Environment Isolation, which is the isolation of the Office 364 Environment. Per Customer Isolation – describes where data is held and how as an ITAR plan customer hardware is provisioned and segregated. Note that this segregation covers only Exchange, SharePoint and Lync online.
Connectivity Protection
Trusted Connection
Trusted Internet Connection. Very useful for thise customers who need support for TIC requirements, Office365 ITAR support plans provide a dedicated connection, rather than an direct internet connection to data centres. This service is provided to SharePoint, Exchange and Lync only.
Two Factor Authentication
Smart cards using PIV (Personal Identity Verification) can be used to ensure secure authentication of clients. However, there are a number of client responsibilities described, including PIV implementation, client side authentication, including PKI and card management. This ITAR supported provision covers Exchange and SharePoint only.
Compliance and Support considerations
Described is the ITAR level plan information concerning compliance with FISMA (Federal Information Security Management Act) covering service hosting, and Microsofts’ plans to to comply with FEDRAMP (Federal Risk and Authorization Management Program). Also, discussed are the security and screening features concerning dedicated hardware, infrastructure location, security access and screening.
Personnel and Background Checks
ITAR ensures that those responsible for supporting Office365 systems on behalf of customers undergo stringent personnel and background checks as follows:
- Employment History Check
- Education Verification
- Social Security Number (SSN) Search
- Criminal History Check
- Office of Foreign Assets Control List (OFAC)
- Bureau of Industry and Security List (BIS)
- Office of Defense Trade Controls Debarred Persons List (DDTC)
- Fingerprinting Check
The article details what kind of checks are carried out and that they are recurring checks. This is applied to Exchange, SharePoint and Lync.
Further Reading
Whilst reading up on ITAR, I found a number of other documents which are extremely useful and I would strongly suggest you check them out:
Federal Information Security Management Act of 2002 – FISMA
Recognises the importance of information security to the economic and national security interests of the United States. The act requires each federal agency to develop, document, and implement an agency-wide program to provide information security for the information and information systems that support the operations and assets of the agency, including those provided or managed by another agency, contractor, or other source.
International Traffic in Arms Regulations – ITAR
Controls the export and import of defense-related articles and services on the United States Munitions List (USML).
Federal Risk and Authorization Management Program – FEDRAMP
For security in Cloud computing, the US Government has compliance audits such as Federal Information Security Management Act of 2002 (FISMA) which cloud providers can go through to meet security standards.
FEDRAMP is a program which develops relationships between Federal agencies and cloud service providers. The program is designed to be compliant with FISMA.
Microsoft Office 365 ITAR-Support Service and Network Descriptions
Documents that support and further describe FISMA and ITAR-Support Solutions Service Description and the Network Service Description for Office 365 ITAR Support Plans
Office 365 Dedicated
Resources covering Office 365 dedicated service descriptions, deployment guidance and dedicated administration.

For anyone working with software systems will know that there is nothing on the planet that is so completely frustrating, as a solution that does not work. Downtime leads to increased overhead costs, lost productivity, lost customer satisfaction and lost revenue. This hits business users of course, but also those who are there to support the business.
Small business users are especially hit by this since they are completely dependent upon the technology. Take into consideration therefore that if businesses do not understand the provisions of support for a cloud service that they will particularly suffer, especially since they will not, in the main have direct access to IT staff to aid them.
Office 365 carries with it solutions (SharePoint, Lync, Mail, Yammer, Office) within a significant number of feature such as Identity, Exchange, Rights Management, etc. Just think of what a small business will need to go through to start to raise a call concerning an issue if there is a problem with one or more of those solutions. And those with internal IT teams to help will fair no better. Having an IT team to turn to, without understanding that self service is available, that tools, troubleshooting techniques, videos, forums that are available, does not warrant a successful support structure. Additionally, the support level in Office 365 needs to marry with expectations from the client. You can only do that by understanding the provision of support provided.
So, here’s a call to action. For those utilising Office 365, or even providing Office365 to clients, I would strongly suggest that the following article is read and understood. And, before you start saying ‘this will not apply to me because I am using SharePoint 2013 on-prem, and I might be using an Office 365 tenant’ – it does!
The article describes:
- Community and self-service support options – describes the various resources that can be used to provide self-help.
- Pre-sales support – describes the various assistance provisions for understanding features, benefits, plan comparisons, pricing, licensing, etc.
- Billing and subscription management support – describes the kind of assistance for signing up, renewing subscriptions, paying bills, etc.
- Technical Support – describes what areas of support will be covered and how.
- Shared Support Responsibilities – very important for those who will need multiple roles in their Office 365 administration and support management scenarios.
- Additional support options – describes three other levels of support like Microsoft Cloud Vantage, Premier and Professional Direct Support, including partners, developers and volume licensing.
- Features – describes the support options, like phone support, technical, billing, pre-sales, etc. against the differing licencing options available for Office 365.
So check out the article on this link: http://technet.microsoft.com/en-us/library/office-365-support.aspx

The Cloud Security Alliance published the Cloud Control Matrix, to support consumers in the evaluation of cloud services and to identify questions prudent to have answered before moving to cloud services. In response to this publication, Microsoft has created this document to outline how we meet the suggested principals and mapped them to the International Standards Organization (ISO) 27001:2005 and ISO 27002. With this standardized response we would like to empower customers with in-depth information to evaluate different offerings in the market place today.
Standard Response to Request For Information-O365-Security-Privacy_v2.docx
Standard Response to Request For Information-O365-Security-Privacy_v2.pdf
Microsoft has today released the Office 365 for business public roadmap. The Office 365 for business public roadmap provides customers with a way to learn more about upcoming change and updates before the change impacts their service.
Go here to see the Office365 for Business Public Roadmap
The public roadmap will be closely coupled with the larger Office 365 Change Management strategy, including integration with Message Centre and the Office 365 direct to admin communication channel.
This is an extremely important and very useful service delivery mechanism to ensure you know what services will affect Office 365 customers – the roadmap page is split into sections allowing you to see what features are launched, rolling out, in development and cancelled.
Another very important read is the Improving visibility to service updates blog which gives more information concerning the concepts behind the Office 365 for business public roadmap.
So what is the public roadmap?
The Office 365 for business public roadmap is a web page on Office.com that provides customers with a list of new and updated features being released to the Office 365 service. The website will list recently launched features, features still rolling out, and features that are still in development. The website will launch with a monthly update cadence.
Note that the public roadmap does NOT commit Microsoft to specific timelines for delivering service updates. It follows a set of policies for what should and should not be included based on when an update is expected to being rolling out and previous disclosure of a particular update. The content goes through a quality assurance pass bi-monthly as part of previous NDA roadmap activities.
Why is the public view of the Office 365 roadmap being created?
As both engineering and marketing move to a services operating model, Microsoft are changing the way they approach customer communications. Part of this transformation is going directly to customers and scaling communications to every Office 365 customer from the individual business owner with 1 employee to the largest enterprise or governmental organization with hundreds of thousands of users.
From examining customer data it has been seen that customers expect a “service” to behave like other services in their life, such as cable or mobile phone subscriptions. They expect notification and communication about any changes to their service. PSAT data, focus groups, and OneList items all show the high cost in the old operating model that erodes customers’ trust and confidence in Office 365.
So what’s next?
Microsoft will be listening closely to customer, partner, and field feedback for improvements that fit within policy guidelines. Improvements currently being evaluated include localization into tier 1 languages, notification or tracking capabilities for the site change log, and expanding to include out-of-scope Office 365 instances. They will continue to refine the update tracking process and use the Office Release Roadmap as the single source for data related to service updates.

Am checking up on a friend who is using Office 365 within a team of 20 people, mainly for SharePoint 2013, and who relies on SharePoint support provided externally. My friend stated they want to ramp up the usage, but were concerned about service availability, and wanted to know whether it was possible to get a record of service uptime for Office 365. They were particularly interested in SharePoint Online service uptime.
That got me thinking. Not all customers using Office 365 will understand how to read the service status provided in Office 365. Even if they saw that page, without really understanding the meaning will probably gloss over some of the features within the service status offerings on that page. Also, considering the methods by which Office365 tenants are provisioned (off-the-shelf buy, through a re-seller, directly) it could be likely that literally any computer literate person could be drafted in to support the customer who takes on Office 365 who potentially has never worked in customer support!
So, yes, taking some time to understand the service statuses provided within Office 365 is useful. Particularly if you are responsible for managing SharePoint online through Office 365 (plus its other offerings), or if you are considering a move / hybrid approach and need to inform the client of the service expectation and what is used to measure service status in Office 365.
What is the Office 365 Service dashboard? The service dashboard is located in the Office 365 Admin centre, and then by clicking the View Details and History link at the foot of the current health list in the centre of the screen as shown in Figure 1.

Figure 1: The Office 365 Service Dashboard
When View Details and History is clicked, a screen showing the service health of Office 365 is displayed. These Service are Exchange Online, Identity Service, Lync Online, Office 365 Portal, Office Subscription, Rights Management Service and SharePoint Online and all are shown in expanded format showing the sub-services and their statuses. The service status is indicated by an icon which is displayed for each. Figure 2 shows each service icon, its meaning, the definition associated with that icon.

Figure 2: Office 365 Service Status icons, description and Definitions
Most of the above are self-explanatory, and for each service listed if there is any status reported other than ‘Normal service availability’ there is a link which is provided which when clicked allows the individual to get more information about the service issue.
An interesting one above is ‘False Positive’. For those working in email land you may have heard of this term before. A False Positive is essentially a message which is legitimate but marked as spam, which is then rejected or returned to the sender. So, what that means is that a report is provided that indicates a problem but does not provide clear proof. It is very important that these are noted, because if that’s not done, it will result in False Negative.
Without going into False Negatives (which I will write about in a companion article), let’s take a look at a False Positive example starring on-Premise SharePoint. Assume that a SharePoint 2013 on premise platform has a third party app deployed on it and a monitoring service carrying out remote scans of all apps and services on that platform. Note that it does not matter what the third party app does. The app identifies itself as version “1.6.11”. A remote scan provided on the platform identifies the app to be a vulnerable version (could be due to security, compatibility or other issues). The remote scan does not have further knowledge of the app, however, the scanner has reason to believe that a vulnerability exists and includes this in its reports. However, the SharePoint administrator (a human!) of the target system may know that this app has already been security-fixed to “1.6.11-1”, however, the app still identifies itself as version 1.6.11. Hence, this is a False Positive because the platform is deemed healthy.
I would suggest that False Positives are useful when identified, and should be recorded – so it has good reason to be there listed as a service status. One thing I should point out, however, is that the problem with tools to remote scan is that if they are configured strongly enough to be effective, there’s a significant chance of receiving false positives. If too many false positives are received, the monitoring becomes less proactive to the point were real issues are ignored, because of the volume of false positives and the assumption therefore that a human already ‘understands’ that there is no issue (when there is!).
Going back to getting more information concerning the service status. Figure 3 shows a list of the current health against each service in Office 365, and for any there there are issues links are provided for more information. SharePoint shows as being in extended recovery in the screenshot. You can click the View details link to get more information concerning the issue. In the figure, I have deliberately scored over the date…

Figure 3. Example of the Current health of services section in the Service Overview page
When clicking on the view details against a particular service status (not normal service status), another page is displayed giving further information concerning the issue covering issue, resolution action and date of next update. Figure 4 shows the page displayed when the view details link is clicked (again I have deliberately scored over the date).

Figure 4. The details page regarding the relevant incident when clicking the view details link at the foot of any service which has an issue on the service overview page
So, the service overview page is a good resource for identifying how the products provided in a Office 365 tenant are performing. However, without understanding the lifecycle of a service incident, it will be problematic in identifying whether a service incident is being fixed, has been fixed, is still under investigation and so on. What is the lifecycle concerning a service incident and how is that reflected on the service health dashboard? Here is an outline of that process:
- The incident occurs
- The service health dashboard is updated to ‘investigating’
- The incident status is posted to the service health dashboard
- The incident is resolved
- The closure summary is posted to the service health dashboard
- The post incident review is posted to the service health dashboard
I think this lifecycle is important to describe to your customer, as well as your service desk team (if for example you have an internal support team). When explaining the lifecycle of a service incident to a new customer, do this as part of providing Office 365 in the first place. If this is not done, there will be an assumption from the customer that they have a direct line to Microsoft Support. They will assume that they can quite literally pick up the phone, report a user challenge which they think is resolved using the product, and expect it be resolved immediately and that the resolution meets their exact requirements. Besides which, even understanding the sheer wealth of information provided on the service dashboard will overwhelm the customer, particularly if the customer has not been taken to identify, using the Service Level Agreement, the products listed of the service dashboard which will be of applicable to the them. That’s not to say the support you provide does not monitor the other services, it is just that in terms of priority that there is information going back to the customer that clearly identifies what is supported.
Conclusion.
Understanding the service dashboard is only a part of the picture in providing a successful support service for an Office 365 customer. In order for it to be effective and measurable, the results being displayed on the dashboard needs to be made meaningful and each service status to be relayed to the relevant customer in a way that makes it useful to them. So, to effectively support Office 365 and to manage customer expectation, you should define a Service Level Agreement which maps onto exactly what will be supported, since that is the key that will help you and the customer able to map the service status provided by the Office 365 service, give that meaning and provides a useful resource which can be measured.
I repeat, the principle here is a matter of what is supported. Your job as SharePoint support is to support the information worker, and in that sense, you support the usage of SharePoint. Your job is intertwined with how SharePoint is exploited to the benefit of the business. Your job is user support. However, Microsoft will see things from an entirely different perspective. Their job is product support. Microsoft cannot be expect to support your users, and certainly cannot be expected to precisely understand how your business applies to their products. So, when your query goes to Microsoft Office365 support, that query will be of several to do with the products provided within Office 365 of which SharePoint is one. That support will answer the question from a product perspective point of view. Your job, is to translate that inherently generic information into the specific information your end user needs. That means that the service status messages that are provided within the dashboard are not specific to your users concerning their use of the product, and instead the service status of the entire product provided to all customers. You must therefore take the information provided by the service status messages and relay that to the customer in a way they understand using the Service Level Agreement.
The Service Level Agreement is vital, for in the end, the only support service truly qualified to support your users is your own. The service dashboard is a resource, for that is the best it can be. If you depend 100% on Microsoft Office 365 support, the best you can hope for is an accidental or actual coincidence of purpose. I believe that is a foolish prospect, whereby one would hope or even attempt to engineer that the two widely differing set of goals (those of Microsoft and your end users) coincide somewhere, so that your company can extract some real benefit from ‘supplier’ support. I would not put all my eggs in relying on complete Microsoft support. You will still need to provide real user support and that means building a proper support model which exposes the service status. The alternative (getting the supplier to provide end user support) will simply not happen in the way the customer will expect or fully understand.
References:
SharePoint Service Level Agreement Guide
SharePoint Service Delivery
Book – SharePoint 2013 Adoption and Governance Guide

I’ve been getting quite a few calls from customers who are in the process of taking SharePoint 2013, who are currently SharePoint 2010 users and quite rightly concerned about what functionality is not available in SharePoint 2013.
(more…)

Got a great read today I thought I should share with you all. Got to read a thought leadership piece from Forrester focusing on Cloud Change Agents. This report is the result of a study Microsoft commissioned with Forrester to explore the status of cloud as a business transformation driver among a selection of UK businesses.
The Cloud Change Agents report is a new study conducted by Forrester Consulting and commissioned by Microsoft Ltd to show how cloud computing is acting as a ‘big switch’ to drive transformation in businesses. The study shows how a certain set of individuals in UK businesses – change agents – working with IT leaders are leading the way, seizing on the cloud to accelerate projects with minimal risk, low cost, little administration overhead and providing the ability to trial and then quickly scale up.
The research shows that these change agents are coming from everywhere in the business. They spot business opportunities and then team up with IT and use the cloud to make their visions reality. Often they might not even be aware that their new project sits ‘in the cloud’, only that they have discovered a fast, convenient way of working.
Of course, change agents have always existed but the cloud provides a way of delivering IT services that suits them very well, enabling new dimensions and the chance to change radically the way businesses operate, add new services, open additional sales channels, market in new ways and provide greater transparency all round. For people with the vision, strength of conviction, passion and drive to lead change, the cloud is a gift.
Read the foreword from Rob Fraser, Cloud Services CTO, Microsoft Ltd here and to download a copy of the report go here.

Office is definitely the topic of the moment and below is some information about this great new release along with details about the consumer and community support offerings now available.
Yesterday Microsoft reached another very exciting milestone on our journey to a devices and services company, with the launch of the new Office to consumers.
This is the biggest and most ambitious release of Office yet, and builds on a fantastic launch year for the company. Steve Ballmer made a blog post detailing four important announcements:

Additional Information:
Office 365 Home Premium
Also, Office 365 Home Premium is a great new option for consumers and the benefits include:
- All the Office Professional applications
- A household license for up to 5 PCs/Macs/mobile devices
- An extra 20GB of SkyDrive Storage
- 60 minutes of Skype calling each month
- A service that is always up to date.

User Adoption of SharePoint is based on meeting the goals and requirements of the business sponsor. To do that, there is an importance in ensuring that the correct features are applied to the relevant solutions to meet their goals. Platform Governance is key; since there would need to be knowledge of the relevant features and an understanding therefore in how they would be implemented, supported, maintained in an evolving SharePoint landscape. This is particularly important in deciding on the migration path of SharePoint 2010 to 2013, since quite a few features have been enhanced.
(more…)

A major important milestone in the step to get information workers creditations in the use of Office products. Just last year I completed the SharePoint Study guide for Microsoft Office, and now in not the too distant future (in fact in late August to be precise), Office 365 will get an exam study guide. In fact, the author happens to be my co-author for the brilliant study guide for Office 2010 (including SharePoint of course!).
This is I think a major move on the part of Microsoft who are keen to ensure that educational establishments, armed with the free offer of Office 365 will now also be able to offer courses, examinations and creditations for information workers to place on their CVs, and shout to the world they are proficient in the use of Office 365! (more…)





























