As we announced last month, to reflect the fact that Office 365 Groups power collaboration across Microsoft 365, Office 365 Groups will become Microsoft 365 Groups. These changes will happen over time and will be reflected in all the connected endpoints over the next couple of quarters.
To align the Tech Community with the name change, we are also creating a new Community Hub called Microsoft 365 Groups. This new Hub will replace the existing Office 365 Groups community. Folks who are existing members of the Office 365 Groups Community Hub will be automatically joined as members of the new Hub. In addition, content from the conversation spaces in the Office 365 Groups Community Hub will be migrated to the Microsoft 365 Groups Hub, and the Office 365 Groups Hub will be redirected to the new Microsoft 365 Groups Hub. By migrating membership and content to the new Community Hub, we are making this move seamless and transparent for you, although you will need to update your bookmarks/favorites, as the URL will be changing.
We are making the transition on June 30, 2020, and we wanted to give everyone notice before doing so. The new Microsoft 365 Groups community will be your place to discuss best practices, news, and the latest topics related to Microsoft 365 Groups. It is intended as a place for sharing information and discussions.
Thanks for your help keeping the Office 365 Groups community a vibrant and useful place, and we look forward to seeing you in the new Microsoft 365 Groups community in the future!
–The Microsoft 365 Groups team
During this current COVID-19 crisis, many organizations have had to rapidly implement a work-from-home model for the majority of their users. For many, this means an enormous increase in load to the VPN infrastructure as all traffic is traditionally sent via this path that was invariably not designed for the volume or type of traffic now reliant on it.
To improve performance, and also reduce load on the VPN infrastructure, many customers have achieved significant results by following the Microsoft guidance to implement split tunneling (or forced tunnel exceptions to use the correct technical term) on the Optimize-marked Office 365 endpoints. This traffic is high-volume and latency-sensitive traffic, and thus sending it directly to the service solves the problems outlined above and is also the designed best practice for these endpoints.
Microsoft 365 Live Events (Teams-produced live events and those produced with an external encoder via Teams, Stream, and Yammer) and on-demand Stream traffic are not currently listed within the Optimize category with the endpoints listed in the ‘Default’ category in the Office 365 URL/IP service. The endpoints are located in this category as they are hosted on CDNs that may also be used by other services, and as such customers generally prefer to proxy this type of traffic and apply any security elements normally done on diverse endpoints such as these.
In most organizations the traffic is internally routed via a network path that is designed to cope with the load and provide latency at a level that doesn’t impact service quality. With the switch to large scale remote working, many customers have asked for the information required to connect their users to Stream/Live Events directly from their local internet connection, rather than route the high-volume and latency-sensitive traffic via an overloaded VPN infrastructure. Typically, this is not possible without both dedicated namespaces and accurate IP information for the endpoints, which is not provided for the Default marked Office 365 endpoints.
Microsoft is working to provide more-defined and service-specific URL/IP data to help simplify connectivity to the service for the VPN connection model but as you can imagine for a global SaaS service like Office 365, this is not something which can be achieved overnight. Therefore, in the interim we’ve been working on interim methods to meet customer demand for this information. As a result of some changes we were able to perform relatively quickly, we are able to provide the following steps to allow for direct connectivity for the service from a client using a forced tunnel VPN.
This is slightly more complex than normal to implement (requiring an extra function in the PAC file) but should provide a comprehensive solution to this challenge until such time as we can rearchitect the endpoints so as to simplify connectivity requirements.
To implement the Forced tunnel exception for Teams Live Events and Stream, the following steps should be applied:
1. External DNS resolution.
The client needs external, recursive DNS resolution to be available for the following FQDNs so they can resolve host names to IPs.
- *.streaming.mediaservices.windows.net
- *.azureedge.net
- *.media.azure.net
It is important to note, it is not advised to just use these URLs to configure VPN offload even if technically possible in your VPN solution (eg if it works at the FQDN rather than IP). This is due to the fact some of these endpoints are shared with other elements outside of Stream/Live Events and as such the IPs provided below are not comprehensive for that FQDN, but are for Teams Live Events/Stream.
2. PAC file changes (Where required)
In most organizations, a PAC file will be used in a VPN scenario to configure the client to send traffic either direct, or via the internal proxy server. Normally this is achieved using FQDNs. However, with Stream/Live Events, the namespace provided currently includes wildcards such as *.azureedge.net, which also encompasses other elements for which it is not possible to provide full IP listings. Thus, if the wildcard is sent direct, traffic to these endpoints will be blocked as there is no route via the direct path for it in step 3.
To solve this, we’re able to provide the following IPs and use them in combination with the FQDNs in section 1 for Stream/Live Events in an example PAC file. The PAC file checks if the URL matches those used for Stream/Live Events and then if it does, it then also checks to see if the IP returned from a DNS lookup matches those provided for the service. If both match, then the traffic is routed direct. If either element (FQDN/IP) doesn’t match then the traffic is sent to the proxy. This way we ensure anything which resolves to an IP outside of the scope of Stream/Live Events will traverse the proxy via the VPN as normal.
Table 1: IP addresses for Live Events & Stream
|
IPv4
|
IPv6
|
|
72.21.81.200
|
2606:2800:011F:17A5:191A:18D5:0537:22F9
|
|
152.199.19.161
|
2606:2800:133:206E:1315:22A5:2006:24FD
|
|
117.18.232.200
|
2606:2800:0147:120F:030C:1BA0:0FC6:265A
|
|
192.16.48.200
|
2606:2800:0157:1508:1539:0174:1A75:1191
|
|
93.184.215.201
|
2606:2800:11F:7DE:D31:7DB:168F:1225
|
|
68.232.34.200
|
2606:2800:133:F17:19E8:2356:251B:02A9
|
|
192.229.232.200
|
2606:2800:0147:0FF8:129B:22EB:020B:1347
|
To implement this in a PAC file you can use the following example which sends the Office 365 Optimize traffic direct (which is recommended best practice) via FQDN, and the critical Stream/Live Events traffic direct via a combination of the FQDN and also the returned IP address. Contoso would need to be edited to your specific tenant name where contoso is from contoso.onmicrosoft.com
Example PAC file
function FindProxyForURL(url, host)
{
var direct = “DIRECT”;
var proxyServer = “PROXY 10.1.2.3:8081”;
//Office 365 Optimize endpoints direct
if(shExpMatch(host, “outlook.office.com”)
|| shExpMatch(host, “outlook.office365.com”)
|| shExpMatch(host, “contoso.sharepoint.com”)
|| shExpMatch(host, “contoso-my.sharepoint.com”))
{
return direct;
}
/* Don’t proxy Stream/Live Events traffic*/
if(shExpMatch(host, “*.streaming.mediaservices.windows.net”)
|| shExpMatch(host, “*.azureedge.net”)
|| shExpMatch(host, “*.media.azure.net”))
{
var resolved_ip = dnsResolve(host);
if (isInNet(resolved_ip, ‘72.21.81.200’, ‘255.255.255.255’) ||
isInNet(resolved_ip, ‘152.199.19.161’, ‘255.255.255.255’) ||
isInNet(resolved_ip, ‘117.18.232.200’, ‘255.255.255.255’) ||
isInNet(resolved_ip, ‘192.16.48.200’, ‘255.255.255.255’) ||
isInNet(resolved_ip, ‘93.184.215.201’, ‘255.255.255.255’) ||
isInNet(resolved_ip, ‘68.232.34.200’, ‘255.255.255.255’) ||
isInNet(resolved_ip, ‘192.229.232.200’, ‘255.255.255.255’))
{
return direct;
}
}
// Default Traffic Forwarding.
return proxyServer;
}
It’s worth stressing again, it is not advised to attempt to perform the VPN offload using just the FQDNs, utilizing both the FQDNs and the IPs in the function helps scope the use of this offload to just Stream/Live Events. The way the function is structured means that only if the FQDN matches those listed, do we perform a DNS lookup for it i.e DNS does not have to be performed for all namespaces used by the client.
3. Configure routing on the VPN to enable direct egress
The final element is to add a direct route for the Live Event IPs in Table 1 into the VPN configuration to ensure the traffic is not sent via the forced tunnel into the VPN. Detailed information on how to do this for the Office 365 Optimize endpoints can be found in this article, and the process is exactly the same for the Stream/Live Events IPs listed in this document.
FAQ:
Question: Will this send all my traffic for the service direct?
Answer: No, this will send the latency-sensitive streaming traffic for a Live Event or Stream video direct, any other traffic will continue to use the VPN tunnel if they do not resolve to the IPs published.
Question: Do I need to use the IPv6 Addresses?
Answer: No, the connectivity can be IPv4 only if required.
Question: Why are these IPs not published in the Office 365 URL/IP service?
Answer: Microsoft has strict controls around the format and type of information that is in the service to ensure customers can reliably use the information to implement secure and optimal routing based on endpoint category.
The default endpoint category has no IP information provided for numerous reasons, such as it being outside of the control of Microsoft, is too large, or changes too frequently, or is in blocks shared with other elements. For this reason Default marked endpoints are designed to be sent via FQDN to an inspecting proxy, like normal web traffic.
In this case, the above endpoints are CDNs that may be used by other elements other than Live Events or Stream, and thus sending the traffic direct will also mean anything else which resolves to these IPs will also be sent direct from the client. Due to the unique nature of the current global crisis and to meet the short-term needs of our customers, Microsoft has provided the information above for customers to use as they see fit.
Microsoft is working to reconfigure the Live Events endpoints to allow them to be included in the Allow/Optimize endpoint categories at a later date.
Question: Do I only need to allow access to these IPs?
Answer: No, access to all of the ‘Required’ marked endpoints in the URL/IP service is essential for the service to operate. In addition, any Optional endpoint marked for Stream (ID 41-45) are required.
Question: What scenarios will this advice cover?
Answer:
1. Live events produced within the Teams App
2. Viewing Stream hosted content
3. External device (encoder) produced events
I thought to use rule like following to be able to impact only audio/video streams:
if(shExpMatch(host, "*.streaming.mediaservices.windows.net"))
{
var host_ip = dnsResolve(host);
/* Check if Stream services are targets */
if (isInNet(host_ip, '72.21.81.200', '255.255.255.255') ||
isInNet(host_ip, '152.199.19.161', '255.255.255.255') ||
isInNet(host_ip, '117.18.232.200', '255.255.255.255') ||
isInNet(host_ip, '192.16.48.200', '255.255.255.255') ||
isInNet(host_ip, '93.184.215.201', '255.255.255.255') ||
isInNet(host_ip, '68.232.34.200', '255.255.255.255') ||
isInNet(host_ip, '192.229.232.200', '255.255.255.255'))
{
returndirect;
}
return proxyServer;
}
Then I could minimize the DNS queries. And above code is just a snap, not full .PAC file 🙂
Hi
I just tested this, and it works exactly as you’ve outlined. On my clients Updates Enabled is set to True, so really, I think the only difference in the configuration you provided was the Accept EULA. I didn’t have that in mine, so I guess that’s why it wasn’t working? (I am using the latest ODT client) If the accept EULA is required, can we add that to the channel change example templates? As far as I can tell, that’s what was throwing me off. I appreciate you taking the time to provide detailed responses here. It’s been super helpful.
Have a great day!
, I’m taking the lazy approach. Let the C2R do its job, Microsoft improved a lot here and it is working smoothly. Via collections I’m identifying the amount of clients under each major version and if I see higher amount of clients stuck in older version I’ll dig into it.
We had SCCM management in place where the source was DFS share, not happy with it, always to keep the sources up-to-date. We thought about SCCM/CDN but we asked ourselves why to administrate SCCM to tell C2R what to do as C2R is already grown up and can handle it on its own.
We’re installing all O365 applications, language packs and proofing tools through CDN/DO, why not doping it with the updates, too.
SCCM has of course the monitoring and reporting capabilities, I’m missing those in the cloud but rumors say they are coming at some point.
So far relying on the hardware inventory is ok with me.
I’m interested to hear from your experience with SCCM/DO
I am evaluating Whiteboard, its position in the Office 365 functionality landscape and how viable it is.
The desktop app has some great features (some in preview) while the web version seems a bit basic still.
How active is the development?
Do you know if the roadmap is up-to-date?
I’d e.g. love to see
- a clearer integration to Teams allowing whiteboards to created for a channel and/or be displayed as a tab
- embedding/integrating whiteboard to SharePoint or other webs
- organising whiteboards in some way
I’m ready to be amazed.

Many of you have been looking for ways to bring the latest capabilities to your users to stay the most productive and secure. Customers who have switched to a faster update cadence, tell us about higher end-user satisfaction as they benefit from many capabilities and improvements as soon as they are available. The current worldwide environment has triggered an unprecedented acceleration in digital transformation, prompting IT to support companywide transitions to remote work without affecting productivity. Recent enhancements to popular collaboration capabilities such as Comments, While you were away, and @mentions have proven particularly useful, as the demand for real-time collaboration grows. To help you bring the latest capabilities like these and others to your users faster, we recommend customers choose Current Channel as their update cadence for servicing Microsoft 365 Apps for enterprise.*
We recognize that to manage more complex environments, you need extra tools and more time to validate new features without additional burden on IT. To support these requirements, we are releasing a whole new set of capabilities throughout the year. Based on a modern management approach, we’re focusing this wave of innovation on delivering servicing predictability, additional tools to manage the health of your environments, and a more efficient issue resolution process.** Today, we start by announcing the general availability of the new Monthly Enterprise Channel and a few other changes that modernize the way you service Microsoft 365 Apps, as you deliver the latest productivity value to your businesses.
New Monthly Enterprise Channel
As an IT admin, you can control how often the users in your organization get new Microsoft 365 Apps features by specifying the update channel. Before today, some of our customers have opted for less frequent updates due to the unpredictable nature and network stress of a faster cadence. The new Monthly Enterprise Channel is designed to alleviate many of those concerns and reduce the burden on IT. Choosing this update channel will allow you to offer your company the latest productivity features, like real-time collaboration, the latest reliability and performance improvements, and security updates on a predictable, once-a-month cadence. All updates will be delivered as one package on the second Tuesday of each month, which we call “Patch Tuesday.”
Because all Monthly Enterprise Channel updates are shipped once a month, you will benefit from both low interruption and the ability to optimize network utilization for your enterprise. Capabilities like Delivery Optimization are already available to help you optimize bandwidth when downloading new bits, as well as regular updates.
To help you better manage changes while moving to a faster cadence, Monthly Enterprise Channel will be offering additional capabilities to advance the health of your environment and a more transparent and faster issue resolution process. To learn more about the new update channel and how it is different from other existing update channels, read this article.
 Microsoft 365 admin center experience for setting up Monthly Enterprise Channel (new channel names will appear on June 9th).
Microsoft 365 admin center experience for setting up Monthly Enterprise Channel (new channel names will appear on June 9th).
Streamlining names for existing channels for Microsoft 365 Apps
As we introduce the new channel and our servicing model keeps evolving, we are renaming the existing update channels (Insider, Monthly, and Semi-Annual) to help you make better decisions about the servicing strategy for your organization. This change only applies to those of you running Microsoft 365 Apps on Windows devices. You will have an option to choose among Current, Monthly, or Semi-Annual channels. Testing channels will now be called Preview, instead of Targeted. While the Insider program remains, we will use Beta Channel as the new name for the channel designed for our early adopter/insider audience. Learn more about new update channel names in this article.
|
New names
|
Recommended use
|
|
Beta Channel
|
For early adopters, IT Pros, and developers who join the Insider community to get access to the earliest build
|
|
Current Channel (Preview)
|
For enterprises to have early access to the upcoming Current Channel release and for fans or early adopters who want early access but also more stability
|
|
Current Channel
|
To provide your end users with the most current Office features and latest security value as soon as they are ready
|
|
Monthly Enterprise Channel
|
For customers who need the latest features on a predictable monthly cadence
|
|
Semi-Annual Enterprise Channel (Preview)
|
For enterprises to preview the experience for the upcoming Semi-Annual Enterprise Channel release
|
|
Semi-Annual Enterprise Channel
|
For select devices in your organization where extensive testing is needed before rolling out new Office features (e.g., to comply with regulatory, governmental, or other organizational requirements)
|
Changing default update channel setting for new tenants to Current Channel
Along with the new capabilities to help you better service Microsoft 365 Apps, new tenants installing Microsoft 365 Apps will be defaulted to Current Channel. This update channel delivers feature updates as soon as they are production-ready and is fully compliant and supported. Feature updates, additional security updates, quality updates, and bug fixes are delivered about two or three times a month. This update channel is recommended for broad deployment across organizations of any size, including educational institutions. This change will start rolling out on June 9, 2020. There is no change to the default update channel setting for existing tenants.
Regardless of where you are in your cloud journey, your company looks to you for guidance on how to stay streamlined, cost-effective, and secure. This is only the beginning of the innovation wave offering you modern options to manage client app software, as you make your business competitive and productive.
Join us on May 27 at 9 AM PT for a live Ask Microsoft Anything session. We’d love to answer any questions you have about deploying Microsoft 365 Apps.
Thank you for your continuous feedback. Visit UserVoice to send us your ideas.
Ask us questions in our dedicated Tech Community space,*** watch new episodes on our Deployment Insider channel to learn more and explore the Office Insider program to give your users access to early features before deploying more broadly.
*Previously known as Office 365 ProPlus.
**Additional capabilities are shipping later this year.
***Previously known as the Office 365 ProPlus community space.
Agree with – I actually want to pin apps I use less frequently, because the ones I use regularly are actually pretty easy to find without being in the O365 app launcher. For example, what’s the point of having Excel, Word and PowerPoint pinned – I’m in and out of these types of documents all day, and if I’m in my OneDrive and want to make a new Word document I go New +Word document. On the other hand, I might need to use one of my organisation’s apps that we’ve included in the app catalogue once in a blue moon. I don’t want to have to mess around scrolling through the list of apps to find it – I want to pin my preferred apps so that they are there when I want them.
Please reinstate the ability for users to self-select which apps they have pinned in the launcher.
Further, it would be good if ‘Admin selected apps’ – the organisations own apps – were available from the Office 365 All apps page. At the moment these are only visible in the app launcher.
Today we’re updating Microsoft 365 IT Admins on availability of the Microsoft Search in Bing browser extension for Chrome. Based on customer feedback, this capability will be opt-in and for AD-joined devices only. As we’ve stated previously, unless an admin chooses to install the extension it will not be deployed. Once deployed by opting in through Microsoft 365 Admin Center, the user remains in control and can revert to their original search engine settings at any time. With Version 2005 of Office, we are starting to roll out the admin capability to easily deploy this extension to Insider builds through Microsoft 365 Apps for enterprise on Windows devices.
Thank you to our customers who have given us valuable feedback about the process for rolling out this extension as well as the capabilities it enables. We’re glad to serve you and your organizations, as we are delivering Microsoft Search in Bing at this time to enable a simple, powerful search experience for information both inside an organization and across the web.
With many of your employees using AD-joined devices at home to work remotely, connecting people with the right information quickly is essential to sustaining everyday productivity. Microsoft Search helps employees to find the right people in a dispersed organization, relevant documents as collaborators may not be online at the same time, and critical internal sites for latest information from IT, benefits, and HR. The Bing extension makes it possible to access work and web content from the Chrome address bar if an IT admin decides to deploy it.
We understand IT admins are dealing with challenging environments now that more people are using their own devices at home while working remotely. As previously communicated, the extension will only be available to AD-joined devices at this time and the improved admin experience for managing this feature now includes a check box in the Microsoft 365 admin center.
For more detailed information about deploying the Microsoft Search in Bing browser extension for Chrome through Microsoft 365 Apps for enterprise and the timing of availability (based on your channel) please refer to this support article. Thank you for your ongoing feedback. Please continue to share with us through UserVoice.
*formerly known as Office 365 ProPlus
Thanks for your feedback. My team is actually working on a comprehensive guide for install options and which network optimization technologies can be used when. On your ask: You can employ Delivery Optimization for Office in combination with Connected Cache to reduce the load on your corp internet circuits. We save tremendous saving when the combination of the two technologies is leveraged. For completeness, we could also use Configuration Manager Client Peer Cache, but this would only cache the setup.exe and configuration file included in the deployment package.
Thanks again for the feedback, I will add this to the blog post later.

We are excited to announce the availability of Microsoft 365 Multi-Geo in Switzerland, and the reduction of the seat minimum requirement to 250 for Enterprise Agreement customers. These updates will allow more organizations to utilize Microsoft 365 Multi-Geo to address their legal, compliance, industry, or other related data residency requirements.
Please note that this product was previously referred to as ‘Multi-Geo Capabilities for Office 365,’ and will now be named ‘Multi-Geo Capabilities for Microsoft 365,’ consistent with the overall Microsoft 365 announcement on March 30. We previously announced the general availability of Multi-Geo Capabilities, in addition to the workload expansion from Exchange Online and OneDrive to include SharePoint Online.
Microsoft 365 Multi-Geo provides a solution for multi-national businesses seeking a balance between working as a single organization in the Microsoft 365 cloud and addressing global data residency needs. With the reduced seat minimum requirement and coverage across Exchange Online, OneDrive, and SharePoint Online this feature helps bring the full power of Microsoft 365 – the world’s productivity cloud – to organizations at any stage in their digital transformation journey.
Microsoft 365 Multi-Geo enables customers to reduce their on-premises footprint by allocating user data at rest to our available geo locations in the Microsoft 365 cloud, facilitating their ability to meet data residency obligations, all within a single tenant. For in-depth information on how Multi-Geo capabilities work and how to get started, please review the links above.
Available Geos
Microsoft is continuously making new infrastructure investments in response to growing customer demand as more industry leaders choose Microsoft’s cloud services. As a result, Microsoft 365 Multi-Geo is increasing our geo coverage as we expand our datacenter footprint for Microsoft 365. With the latest addition of Switzerland, you can now extend your Microsoft 365 tenant to store your users’ data in one or more of the following geos:
|
Australia
|
Asia Pacific
|
|
Canada
|
European Union
|
|
France
|
India
|
|
Japan
|
Korea
|
|
United Kingdom
|
United States
|
|
United Arab Emirates
|
South Africa
|
|
Switzerland
|
|

Learn about where your Microsoft 365 data is stored at aka.ms/DataMaps
Industry Focus
We see worldwide organizations of all sizes and across all industries currently investing in new ways of empowering their employees with modern tools to enable secure, flexible, and mobile working that fosters collaboration. The ability to configure data residency on a by-user basis helps organizations meet regulatory requirements, which is particularly important and relevant in industries such as healthcare, manufacturing, public sector, and financial services. This latest step enables companies adopting Microsoft 365 to accelerate their digital transformation journey. As a result, we see Microsoft 365 Multi-Geo assisting organizations across the world to enable the scalability required to address critical challenges affecting the global community.

|
“We now have as many people outside the US as in it, and although the GDPR doesn’t mandate a particular Geo for data residency, our clients are hypersensitive about data privacy issues, so we prefer to get in front of it,” Ackermann says. “Our lifeblood includes data which is personal information about people and with Multi-Geo, we’re able to proactively address client concerns about data residency.”
– Bryan Ackermann, Chief Information Officer, Korn Ferry
|
Pricing and Licensing:
Multi-Geo is available as an add-on to the following Microsoft 365 subscription plans for EA customers with a minimum of 250 Microsoft 365 seats in their Microsoft 365 tenant, and a minimum of 5% of the Microsoft 365 seats within a tenant have corresponding Multi-Geo Capabilities for Microsoft 365. Please contact your Microsoft account team for details.
|
Microsoft 365 F1, E1, E3, or E5
|
|
Microsoft 365 F1, E1, E3, or E5
|
|
Exchange Online Plan 1 or Plan 2
|
|
OneDrive for Business Plan 1 or Plan 2
|
|
SharePoint Online Plan 1 or Plan 2
|
Licensing
- USD $2/user/month for users in Satellite Geos
- Resource mailboxes (Rooms/Equipment) and Shared mailboxes need to be licensed
- Microsoft 365 Group Mailboxes moved to Satellite Geos will not need to be licensed for Multi-Geo
How to buy Multi-Geo?
Please talk to your Microsoft representative to buy Multi-Geo Capabilities for Microsoft 365.
Questions?
Please comment on this thread with your questions

With more and more users working from home, organizations are facing new security and privacy challenges. One of them might be, that users are working on unmanaged, maybe personal devices accessing corporate data. Classic technologies like Active Directory Group Policy Management do not help in such scenarios, as these do not apply to unmanaged devices.
This blog post will provide guidance on how to leverage the Office cloud policy service (OCPS) to address those scenarios. OCPS allows an admin to target a user with policies which follow them across all devices, regardless of the way the devices are managed (if at all). We will also share some recommended security settings which might be worth considering.
Step 1 – Enable OCPS
The Office cloud policy service (OCPS) is a cloud-based service that enables you to apply policy settings for Microsoft 365 Apps for enterprise (formally known as Office 365 ProPlus) on a user’s device. The policy settings roam to whichever device the user signs into and uses Microsoft 365 Apps for enterprise. This applies whether the device is managed through on-premises domain devices, as a Azure AD registered, Azure AD Joined, or Hybrid Azure AD joined device.
You should start by verifying the requirements:
- Supported version of Microsoft 365 Apps for enterprise deployed
- Licensed for Microsoft 365 Apps for enterprise
- At least one Azure AD group which contains the users you’re targeting.
- An admin user with at least the Office Apps Admin role assigned
Sign in on https://config.office.com and accept the EULA for OCPS. That’s it. No more prep work needed.

Step 2 – Create a policy configuration and assign to users
Now you should create your first policy configuration and assign it to a group of users:
- Expand the Customization node and select Policy Management
- On the Policy configurations page, choose Create and provide a name and a description (optional)
- In assignments, choose whether this policy applies to all users of Microsoft 365 Apps for enterprise, or just to users who anonymously access documents using Office for the web.
- Select the AAD-based security group that is assigned to the policy configuration. Each policy configuration can only be assigned to one group, and each group can only be assigned one policy configuration.

We also have a video ready for you which walks you through these steps.
Step 3 – Set policies
After clicking on Configure policies you can start to search for and configure policies. Please note that most policies are only applicable to Office on Windows, but some are applicable cross-platform as noted in the platform column in the policy list.
As a starting point, you can filter the Recommendation column to view the recommended Microsoft Security baseline policies. Click on each policy name to view the description and decide if you want to keep the baseline’s recommended value or manually configure it. The reviewed items will switch the Status to Configured when applied.

Especially for the scenario of remote workers, here are some policies you might want to have a closer look at:
| Policy Name |
Comment |
| Block signing into Office |
Can be used to prevent users from being signed in with a corporate and personal account at the same time in order to prevent data leakage to e.g. a personal OneDrive. |
| Hide file locations when opening or saving files |
Setting to “Hide local PC” will discourage users from saving corporate data to the maybe non-corporate device. |
| Disable VBA for Office applications |
VBA/macros are powerful tools and can help automate data processing or entry. But it is also used for malicious attacks and might be better prevented to run on non-managed/remote devices. |
| Do not open files from the Internet zone in Protected View |
If set to “Disabled”, Office files downloaded from the internet will always be opened in Protected View first. |
| Set document behavior if file validation fails |
Admins can enforce Protected View for files which failed validation. Those files could e.g. try to exploit Office through malformed documents. |
| Allow the use of connected experiences in Office, et al. |
Admins can control if Office is allowed to leverage cloud services for downloading and analyzing content. Review documentation for available controls. |
| Force Runtime AV Scan |
If enabled, all files opened by Office will be passed to the installed AV engine for scanning. |
| Use Cached Exchange Mode for new and existing Outlook profiles |
You can use this policy to enforce Online Mode for Exchange in order to prevent users from syncing down their inbox content to a maybe insecure device. Note that this setting will apply to all devices the user is signing into. |
| Block all unmanaged add-ins |
This setting allows you to block all add-ins from being loaded by Office. |
Step 4 – Additional considerations
As policies configured through OCPS are following the user across all devices, it is not limited to remote workers or users on un-managed devices. You should consider folding your on-prem policies into OCPS policies and go forward with a single solution for both on-prem as well as off-prem users.
Once you have deployed OCPS policies, you can also enable the Security Policy Advisor to get further insights into high impactful these changes are for your users. Maybe there are opportunities to further tightening it up without impacting users.
Overview of blog post series
This post is part of a series which is covering different stages and phases in the Office lifecycle in remote worker/work from home scenarios. The others are:
We hope this will help you to minimize the impact of deploying, servicing and managing Microsoft 365 Apps for enterprise on your own network and your user’s VPN connections.
FAQ
Q: Am I secure after enabling OCPS and setting the Microsoft recommended policies?
A: “Being secure” is a relative state where you can try to achieve a high bar, but basically never be 100% secure. Using OCPS is one building block in a broader strategy to secure remote workers. In addition make sure to review Azure Multi-Factor Authentication, Azure Conditional Access and the user’s sign-in risk assessment to further protect the user’s identity. For guidance on protecting your corporate data, please review Azure Information Protection.
Q: I’ve got issues with OCPS, how can I troubleshoot the service?
A: We got you covered, please review Troubleshooting OCPS on Windows.
Q: Can I fully secure a device not owned by my organization?
A: There are limits on how secure a device that you don’t own or manage can be. Each employed security technology raises the bar for an attack/exploit on the device/user/data successfully, but unless you fully manage the device there is a risk to your data. Security is sometimes not about secure/not secure, but more about the right level of security for a given scenario. You can use Intune to manage devices that you don’t own.
Q: Can I also secure and control Office on iOS or Android using OCPS?
A: While some policies also apply to Office on Android or iOS, there are more advanced controls available through Intune Application policies. These allow you to e.g. enforce a PIN, local data encryption of cloud-only storage of data for the Office apps on mobile devices.
Q: We’re an Intune shop, can I also use Intune to manage OCPS policies?
A: Sure thing. You can manage the Policies for Office apps from the Intune portal as well.
Q: Can we use OCPS to block syncing OneDrive for Business content on devices which aren’t managed?
A: No. However, we can address this concern by having your Office 365 tenant administrator running Set-SPOTenantSyncClientRestriction cmdlet. This permits adding restrictions on whether users can sync items to non-domain joined machines.
The Authors
This blog post is brought to you by the Microsoft 365 Apps for enterprise Ranger Team at Microsoft. Feel free to share your questions and feedback in the comments below.

This blog post will address the enterprise IT admin’s challenge on how to deploy Office 365 ProPlus to remote workers without saturating the company’s VPN connections. It will show you how to implement a tactical approach which allows an IT admin to stay in control and quickly relief the pain of VPN congestion by offloading content distribution to the Microsoft Content Delivery Network (CDN). Maybe you are in the process of moving off legacy versions of Office and want to keep the pace with e.g. the Office 2010 end-of-support approaching fast. There are multiple strategic solutions available (e.g. Intune and Windows Autopilot), but for now we focus on a quick fix.
Overview of blog post series
This blog post is part of a three-part series, which is brought to you by the ProPlus Rangers at Microsoft, a group of most senior deployment experts. The series provides guidance on how to offload content distribution to the Microsoft CDN across the lifecycle of an Office 365 ProPlus installation:
We hope this will help you to minimize the impact of deploying, servicing and managing Office 365 ProPlus on your own network and your user’s VPN connections.
The Concept
With the approach described below, we want to achieve two things:
- Keep IT admins in control what happens when by continue using your enterprise management solution like Microsoft Endpoint Configuration Manager (formally known as System Center Configuration Manager (SCCM))
- Offloading the content distribution to Microsoft’s CDN to allow remote user to leverage their local internet connection instead of pulling large source files from your ConfigMgr Distribution Points over VPN connections
We will walk you through the process on how to adjust an existing Office 365 ProPlus deployment package for a hybrid approach, update your sources and ensure that the source file download will bypass your VPN.
Step 1 – Adjust your deployment package
To allow remote users to leverage their local internet connection for source file access, we have to remove the source files from the Configuration Manager application. Navigate to the folder which is holding your software sources, locate the “office” folder and delete it:

In the above example, 11 Language Packs were included in the deployment package, bumping the size up to 6+ gigabytes. Keep the setup.exe as well as any configuration files located in the folder. This reduces the size of your deployment package to less than 10 megabyte. That’s a huge saving on your VPN connections.
In case you don’t have an Office 365 ProPlus installation package yet, you can use the built-in wizard to create one. Maybe you want to adjust the handling of languages, instead of hard-coding those you might want to use MatchOS or MatchPreviousMSI. After that, apply the steps above.
Step 2 – Update the content sources
If your application was already synced to Distribution Points, those still have the larger package cached. Navigate to Software Library > Application Management > Applications, select your application, switch to the Deployment Types Tab, right-click the appropriate entry and click Update Content.

This will re-sync any changes to your Distribution Points, so those will now also have the smaller deployment package ready to sync to devices.
Step 3 – Verify VPN configuration and deploy
Once a client has received the smaller deployment package through ConfigMgr and kicks off the installation, it will download the source files directly from the Microsoft CDN. It is important to ensure that your devices can actually reach out to those endpoints directly and don’t backhaul through the VPN tunnel. We published guidance on how to enable so-called VPN split-tunneling, the endpoints relevant for Office 365 ProPlus source file download are listed at Office 365 URLs and IP address ranges as entry #92.
If you already have an active deployment of the newly-updated package, clients will start receiving it after the Distribution Points have finished syncing the changes. If you want to start with a fresh deployment, just follow the regular guidelines in your organization.
FAQ
Q: We usually controlled which build is installed by embedding the matching source files. How can I control this now?
A: By default, setup will fetch the latest build available for the specified update channel. You can use the version attribute in the configuration file to specify a build. This might be important if your organization is wants to deploy the older SAC feature release.
The Authors
This blog post is brought to you by from the Office 365 ProPlus Ranger Team at Microsoft. Feel free to share your questions and feedback in the comments below.

Over the past few weeks, Microsoft, and more specifically the Office 365 Network team have seen a large influx of questions from customers around how best to optimize their Office 365 connectivity as they work diligently to plan for a large amount of their userbase suddenly working from home. We’ve also seen similar queries from customers looking for best practice whilst rapidly enabling their Office 365 benefits, Free Teams plans or free 6 month E1 trial recently announced to rapidly roll out Teams to allow their business to continue to function and allow users to collaborate effectively without being in the Office.
The recent COVID-19/Coronavirus outbreak has caused many customers to rapidly enable, or proactively plan for the bulk of their employees working from home. This sudden switch of connectivity model for the majority of users typically has a significant impact on the corporate network infrastructure which may have been scaled and designed before any major cloud service was rolled out and in some cases, not designed for a situation when it is required simultaneously by all users.
Network elements such as VPN concentrators, central network egress equipment such as proxies, DLP etc, central internet bandwidth, backhaul MPLS circuits, NAT capability and so on are suddenly put under enormous strain due to the load of the entire business using them, with the end result being poor performance and productivity coupled with a poor user experience for those users forced to adapt to working from home.
A simple diagram of a traditional network model can be seen below, where remote user’s connectivity is forced in and back out of the corporate network to reach critical resources as well as branch offices using MPLS circuits to reach the services offered at head office. It is an incredibly common network model for businesses around the world, but it was designed to be effective for a pre-cloud world.
 A traditional enterprise network, which does not work well in a cloud first world
A traditional enterprise network, which does not work well in a cloud first world
This model made perfect sense and worked very well when the bulk of applications, data and services resided within the corporate network (the dotted line in the diagram), but as enterprises shift to the cloud, it rapidly becomes a cumbersome environment which doesn’t scale well or provide the organization with any agility to react to situations such as that we face today. Many customers report to Microsoft that they have seen a very rapid shift of network traffic which used to be contained within the corpnet now almost exclusively connecting to some external cloud-based source.
Fortunately, Microsoft has been working closely with customers and the wider industry for many years to provide effective, modern solutions to these problems from within our own services, and also aligned to industry best practice. Solutions that apply very simply and effectively to remote workers as much as they do to branch offices. Microsoft has designed the connectivity requirements for the Office 365 service to work efficiently for remote users whilst still allowing an organization to maintain security and control over their connectivity.
Below we will outline the simple steps an organization can take to drastically reduce the impact Office 365 traffic has on the traditional corporate infrastructure when we have a large percentage of users working remotely all at once. The solution will also have a significant impact on user performance and also provide the benefit of freeing up the corporate resources for elements which still have to rely on it.
Most remote users who are not using a virtualized desktop will use a VPN solution of some sort to route all connectivity back into the corporate environment where it is then routed out to Office 365, often through an on premises security stack which is generally designed for web browsing.
The key to this solution is separating out the critical Office 365 traffic which is both latency sensitive and that which also puts enormous load on the traditional network architecture. We then treat this traffic differently and use the user’s local internet connection to route the connectivity directly to the service. To do this we need to follow a simple set of actions:
1. Identify the endpoints we need to Optimize
Microsoft has already identified these endpoints and marks them very clearly for reference. In the URL/IP list for the service these endpoints are marked as “Optimize”. There are just four URLS which need to be optimized and nineteen IP subnets. In just this small group of endpoints we can account for around 80% of the volume of traffic to the service and it also includes the latency sensitive endpoints such as those for Teams media. Essentially this is the traffic that we need to take special care of and is also the traffic which will put incredible pressure on traditional network paths.
URLs in this category have the following characteristics:
- Are Microsoft owned and managed endpoints hosted on Microsoft infrastructure.
- Have IPs provided
- Low rate of change to URLs/IPs compare to other two categories
- Expected to remain low in number of URLs
- Are High volume and/or latency sensitive
You can also query the REST API Web Service for this information, and a PowerShell example script which does this and outputs the URLs/IPs/Ports for all three endpoint categories can be found using the link above.
|
Endpoint to Optimize
|
Port/s
|
Use
|
|
https://outlook.office365.com
|
TCP 443
|
This is one of the Core URLs Outlook uses to connect to its Exchange Online server and has high volume of bandwidth usage and connection count. Low network latency is required for online features including: Instant search, Other mailbox calendars, Free / busy lookup, manage rules & alerts, Exchange online archive, Emails departing the outbox.
|
|
https://outlook.office.com
|
TCP 443
|
This is use for Outlook Online web access to connect to its Exchange Online server and network latency. Connectivity is particularly required for large file upload and download with SharePoint Online.
|
|
https://.sharepoint.com
|
TCP 443
|
This is the primary URL for SharePoint Online and has high volume of bandwidth usage.
|
|
https://-my.sharepoint.com
|
TCP 443
|
This is the primary URL for OneDrive for Business and has high volume of bandwidth and possibly high connection count from the OneDrive for Business Sync tool.
|
|
Teams Media IPs (no URL)
|
UDP 3478, 3479, 3480, and 3481
|
Relay Discovery allocation and real time traffic (3478), Audio (3479), Video (3480), and Video Screen Sharing (3481). These are the endpoints used for Skype for Business and Microsoft Teams Media traffic (Calls, meetings etc). Most endpoints are provided when the Microsoft Teams client establishes a call (and are contained within the required IPs listed for the service).
UDP is required for optimal media quality.
|
should be replaced with your Office 365 tenant name. For example contoso.onmicrosoft.com would use contoso.sharepoint.com and constoso-my.sharepoint.com
At the time of writing the IP ranges which these endpoints correspond to are as follows. It is strongly advised you use the script referenced previously or the URL/IP page to check for any updates when applying the policy, and do so on a regular basis.
104.146.128.0/17
13.107.128.0/22
13.107.136.0/22
13.107.18.10/31
13.107.6.152/31
13.107.64.0/18
131.253.33.215/32
132.245.0.0/16
150.171.32.0/22
150.171.40.0/22
191.234.140.0/22
204.79.197.215/32
23.103.160.0/20
40.104.0.0/15
40.108.128.0/17
40.96.0.0/13
52.104.0.0/14
52.112.0.0/14
52.96.0.0/14
52.120.0.0/14

- TCP ports 80/443
- UDP ports 3478, 3479, 3480, 3481
IPV6 endpoints can be ignored if not currently required, i.e. the service will currently operate successfully on IPV4 only (but not the other way round). This will likely change in future but IPV4 only is possible for the time being.
2. Optimize access to these endpoints via the VPN
Now that we have identified these critical endpoints, we need to divert them away from the VPN tunnel and allow them to use the user’s internet connection to connect directly to the service. The vast majority of VPN solutions allow split tunnelling, where identified traffic is not sent down the VPN tunnel to the corporate network but rather sent direct out the user’s local internet connection. The VPN client should be configured so that traffic to the above, Optimize marked URLs/IPs/Ports are routed in this way. This allows the traffic to utilize local Microsoft resources such as Office 365 Service Front Doors such as AFD as one example, which deliver Office 365 services & connectivity points as close to your users as possible. This allows us to deliver extremely high performance levels to users wherever they are in the world. There is also Microsoft’s world class global network which is very likely within a small number of milliseconds of your users direct egress, and is designed to take your traffic securely to Microsoft resources wherever they may be in the world, as efficiently as possible.
The solution would look something like that below.
 A client’s VPN connection with split tunneling enabled
A client’s VPN connection with split tunneling enabled
Sounds simple? It is in most cases, but for an enterprise, this shift in connectivity invariably raises questions about security. In the traditional network approach security is often applied inline to network traffic as it egresses to the internet. Proxies and firewalls perform inspection on the traffic to check for data exfiltration, viruses and so on. By bypassing this we are removing this layer of protection we have come to rely on when connecting to the internet. The good news is, for the highlighted endpoints above, Microsoft has numerous features in place which means your security with the modern approach may well be higher than available previously. We will run through some of the common solutions below, not all will be relevant or necessary to all customers, but we will cover the majority of common concerns that come up when implementing modern network connectivity.
3. Common questions when implementing local breakout and split tunnelling for Office 365
It should be noted that the two steps above are all that is necessary to solve the performance/scalability issues if you need to move very quickly given the current situation. The elements below can be added as needed and as time allows or you may have them in place already.
Q1. How do I stop users accessing other tenants I do not trust where they could exfiltrate data?
A: The answer is a feature called tenant restrictions. Authentication traffic is not high volume nor especially latency sensitive so can be sent through the VPN solution to the on-premises proxy where the feature is applied. An allow list of trusted tenants is maintained here and if the client attempts to obtain a token to a tenant which is not trusted, the proxy simply denies the request. If the tenant is trusted, then a token is accessible if the user has the right credentials and rights.
So even though a user can make a TCP/UDP connection to the Optimize marked endpoints above, without a valid token to access the tenant in question, they simply cannot login and access/move any data.
Q2. Does this model allow access to consumer services such as personal OneDrive accounts?
A: No, it does not, the Office 365 endpoints are not the same as the consumer services (Onedrive.live.com as an example) so the split tunnel will not allow a user to directly access consumer services. Traffic to consumer endpoints will continue to use the VPN tunnel and existing policies will continue to apply.
Q3. How do I apply DLP and protect my sensitive data when the traffic no longer flows through my on-premises solution?
A: If required, endpoints can be protected with Office DLP if required and it’s much more efficient to provide this feature in the service itself rather than try and do it in line at the network edge. Azure Information protection can also be used to provide a high level of information protection if required.
Q4. How do I evaluate and maintain control of the user’s authentication when they are connecting directly?
A: In addition to the tenant restrictions feature noted in Q1, conditional access policies can be applied to dynamically assess the risk of an authentication request and react appropriately. Microsoft recommends the Zero Trust model is implemented over time and we can use Azure AD conditional access policies to maintain control in a mobile & cloud first world. Conditional access policies can be used to make a real-time decision on whether an authentication request is successful based on numerous factors such as:
- Device, is the device known/trusted/Domain joined?
- IP – is the authentication request coming from a known corporate IP address? Or from a country we do not trust?
- Application – Is the user authorized to use this application?
We can then trigger policy such as approve, trigger MFA or block authentication based on these policies.
Q5. How do I protect against viruses and malware?
A: Again, Office 365 provides protection for the Optimize marked endpoints in various layers in the service itself, outlined in this document. As noted, it is vastly more efficient to provide these security elements in the service itself rather than try and do it in line with devices which may not fully understand the protocols/traffic.
For the Exchange endpoints listed above, Exchange Online Protection and Office 365 Advanced Threat Protection do an excellent job of providing security of the traffic to the service.
Q6. Can I send more than just the Optimize traffic direct?
A. Priority should be given to the Optimize marked endpoints as these will give maximum benefit for a low level of work. However, if you wish, the Allow marked endpoints are required for the service to work and have IPs provided for the endpoints which can be used if required.
There are also various vendors who offer cloud based proxy/security solutions called secure web gateways which provide central security, control and corporate policy application for general web browsing. These solutions can work well in a cloud first world, if highly available, performant, and provisioned close to your users by allowing secure internet access to be delivered from a cloud based location close to the user. This removes the need for a hairpin through the VPN/corporate network for general browsing traffic, whilst still allowing central security control.
Even with these solutions in place however, Microsoft still strongly recommends the Optimize marked Office 365 traffic is sent direct to the service.
Q7. Why is port 80 required? Is traffic sent in the clear?
A. Port 80 is only used for things like redirect to a port 443 session, no customer data is sent or is accessible over port 80. This article outlines encryption for data in transit, and at rest for Office 365 and this article outlines how we use SRTP to protect Teams media traffic.
Q8. Does this advice apply to users in China using a worldwide instance of Office 365?
A. No it does not. The one caveat to the above advice is users in the PRC who are connecting to a worldwide instance of Office 365. Due to the common occurrence of cross border network congestion in the region, direct internet egress performance can be variable. Most customers in the region operate using a VPN to bring the traffic into the corporate network and utilize their authorized MPLS circuit or similar to egress outside the country via an optimized path. This is outlined further in this article https://docs.microsoft.com/en-us/office365/enterprise/office-365-networking-china
Finally, please ask any questions you may have in the comments section below and we will do our best to answer as quickly as possible.
4. Further reading
General best practice for Office 365 connectivity:
http://aka.ms/pnc
https://docs.microsoft.com/en-us/archive/blogs/onthewire/__guidance
Recorded Ignite sessions
https://myignite.techcommunity.microsoft.com/sessions/81561?source=sessions
https://myignite.techcommunity.microsoft.com/videos/64276
https://myignite.techcommunity.microsoft.com/videos/64275
Office 365 Partner Program
https://resources.techcommunity.microsoft.com/networking/
Current partners are Citrix, Netfoundry, NTT, SilverPeak and Zscaler
Network Connectivity performance testing
https://connectivity.office.com/
This tool runs some tests against Office 365 endpoints including the Optimize marked ones and give you some clear feedback around how connectivity looks for those endpoints and anything you can do to improve the connectivity.
Bandwidth planning
https://aka.ms/bandwidth/
This tool is one mechanism you can use to monitor user’s Office 365 network traffic volumes to get a clear figure for bandwidth requirements for the wider business.

Due to the dynamic situation with COVID-19 many IT pros are being challenged to assess ways to configure Office 365 Client to update directly from Microsoft CDN. Today, the majority of customers I engage with manage updates using Configuration Manager (ConfigMgr), predominately on-premises. The objective of this posting is how to minimize internet egress through customer VPN network for Office updates.
Network considerations
There are an infinite number of ways customers configure network access, no two customers are identical in configuration. Speaking generally, the VPN client needs to support split tunneling or be configured so network traffic destined for Office 365 are directed to internet and are not required to pass through VPN Server. Microsoft provides a list of all Office 365 URLs and IP address ranges in the following document. Some customers have VPN clients dynamically aware of Office 365 Services using Microsoft Graph API, some support URLs and others only support IP exclusions. You’ll notice item(s) 90 and 92 which provide specific URLs used by the Office 365 Client to perform updates.
|
90
|
Default
Required
|
mrodevicemgr.officeapps.live.com (Description: Device Management Service (DMS) is used to advertise the C2R builds to the machines which are non-admin managed based on the meta data passed by the machine.)
|
TCP: 443
|
|
92
|
Default
Required
|
officecdn.microsoft.com, officecdn.microsoft.com.edgesuite.net (Description: Office CDN where content is downloaded)
|
TCP: 443, 80
|
Tip: Please review blog posting How to quickly optimize Office 365 traffic for remote staff & reduce the load on your infrastructure
Tip: Please review blog posting Managing remote machines with cloud management gateway in Microsoft Endpoint Configuration Manager
Background on how Office 365 Client works by default
Office 365 ProPlus is designed by default to update from CDN. A scheduled task called “Office Automatic Updates 2.0” uses a trigger to routinely check for updates as advertised by DMS service. The Office client will always move to the latest versionbuild available by assigned channel documented here. Documentation around what to expect from a user experience when updates are delivered from CDN can be found here. If ConfigMgr Office 365 Client Management integration is enabled by Configuration.xml during initial installation, ConfigMgr Client settings, or Domain Policy, the scheduled task will continue to execute but will only perform software updates from ConfigMgr.
Options available to update from CDN
Option 1: Cloud managed
Steps:
- Disable OfficeMgmtCOM (required if previously ConfigMgr managed)
- On the next restart of Microsoft Office Click-to-Run Service, Office COM application will de-registered. Allows Office Client to do its thing and get updates from the CDN.
- This can be done by changing client settings in ConfigMgr or by Group Policy.
- Set UpdatesEnabled GPO to True (optional)
- Allows the client to resume normal update checks from the CDN
- UpdateDeadline GPO as an integer (optional) in days (ex. 12) to ensure the client is updated to ensure compliance. Using an integer value allows the admin to not have to continually change the date to a future date/time for every update.
Option 2: SCCM managed but offload content distribution
Use normal deploy software updates wizard within ConfigMgr console selecting deploy option. When completing deployment package screen, it is important to select option “No deployment package”. In this way, clients will download content directly from CDN but keep existing controls and user experience during software update workflow.
Steps:


FAQ:
How can I verify ConfigMgr integration is disabled?
Start -> Run ->dcomcnfg.exe and look for presence of OfficeC2Rcom application.


Where in the Office logs can I confirm Office updates are coming from CDN?
Use http://aka.ms/office365logcollector to collect Office logs or search for files in C:windowstemp which have your NetBIOS name like MININT-314VFT4-20200318-0857.log. (There will be a bunch of them). Use your favorite text editor to search for strings like ‘officecdn.microsoft.com’ or the build number you deployed.
Starting with version 1902, ‘Prefer cloud based sources over on-premise sources’ allows IT Pro to prioritize Cloud content. Does this feature extendsupport Office 365 Client updates?
No, this appear to be a bug which is under investigation. Workaround is to ensure Distribution Points used by VPN clients do not host Office 365 Client updates resulting in error 404. If the software deployment has selection ‘If software updates are not available on distribution point in current, neighbor or site boundary groups, download content from Microsoft Updates’, this should allow new location of CDN fallback to be used. I will update this item with updates when available.
The Authors
This blog post is brought to you by Dave Guenthner and Martin Nothnagel, two ProPlus Rangers at Microsoft. We’re looking forward to your questions and feedback in the comments below.

When installing Office 365 ProPlus using the Office Deployment Tool (ODT), the standard configuration includes the entire suite of applications by default. In some cases, IT Pros need to exclude one or more of the apps or add back previously excluded ones. The article will go over the various scenarios and provide guidance on how to implement them. These scenarios include:
- Exclude apps during initial install
- Remove specific apps after initial install
- Re-including apps that were previously removed
- Adding Visio and/or Project after initial ProPlus installation
So, let’s look at each of these scenarios:
Exclude apps during initial install
There are two main ways how admins can control which apps are excluded at the initial install of Office 365 ProPlus. First, using the Office Customization Tool (OCT) at https://config.office.com, admins can simply toggle the buttons for the apps they wish to exclude from the initial install:

This will craft the configuration file with the necessary exclusions for you. You can either export and save the file locally or to the cloud and reference this file during setup.
A second way that admins can control which apps are installed at the initial install of Office 365 ProPlus is to leverage the attribute in the ODT configuration file directly. The names of all the app values are as follows:
- ID=”Access”
- ID=”Excel”
- ID=”Groove” (This is the old sync client for on-Premises SharePoint)
- ID=”Lync” (Skype for Business)
- ID=”OneDrive”
- ID=”OneNote” (OneNote 2016, Win32 app. NOT the UWP Windows 10 app)
- ID=”Outlook”
- ID=”PowerPoint”
- ID=”Publisher”
- ID=”Teams”
- ID=”Word”
A sample configuration file with Groove and OneNote excluded from the install would look like this:
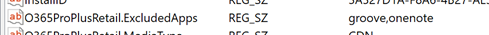
With either method at install time, Office 365 ProPlus will be installed with the selected apps excluded. You can verify by looking at this registry key:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftOfficeClickToRunConfiguration
O365ProPlusRetail.ExcludedApps
Or simply by checking the start menu and noticing those applications are not present.
Remove specific apps after initial install
If Office 365 ProPlus is already installed on a device or devices and you need to remove one or more of the apps, you can use the same method as above. However, there are a couple things to keep in mind.
- You can use Version=”MatchInstalled” to eliminate the need to keep track of the Architecture and Servicing Channel as this attribute will read the existing values and honor them. This can cut down on the number of configuration files needed in environments with multiple Office 365 ProPlus configurations.
- Setup.exe and the configuration file will need access to the Office source files. Either from the Microsoft CDN (Recommended) or internally by including them in a Configuration Manager application. Click-to-Run Office does not cache source files like the MSI version did in the MSOCache location.

If you had previously excluded an app or apps at initial install time, and wish to keep them excluded, you must continue to exclude them via the section of the new configuration file you create along with whichever app or apps you now also want to exclude. Failure to do so will result in those applications being present and usable by your users.
The below example configuration file, leveraging “MatchInstalled” would remove Access from the device after initial install:
Like the warning pointed out, running the above configuration will result in Access excluded and ONLY ACCESS EXCLUDED. If you had previously excluded apps such as Groove or OneNote 2016 from your initial install and now wish to exclude Access while keeping Groove and OneNote 2016 also excluded, you must have all three applications called out like in this example:
Re-including apps that were previously removed
This is very similar to the above scenario. Since Office 365 ProPlus does not include or exclude applications in the traditional sense, but rather asks “what do you want the suite to look like after this configuration?” So therefore If you excluded an app at initial install or post install and now wish to add it back in, you will use a similar configuration to the above example leaving any other apps still excluded you want to remain that way.
Consider this scenario: The IT Pro excluded Access, Groove and OneNote 2016 at initial install and now wishes to add OneNote 2016 back into the suite but leave Access and Groove still excluded. The example configurations would look like this:
Initial install Configuration:
Second install Configuration:
Adding Visio and/or Project after initial ProPlus installation
Visio and Project operate in a different manner as they are different Product ID’s. These products cannot be added or excluded with the attribute. They can be added after the initial install by using a configuration file with Visio and/or Project as the value. You must match the servicing channel and version of Click to Run architecture (64/32-bit) to prevent making unwanted changes. Better yet, you can leverage the power of the CDN and the new attribute to do the heavy lifting here. Deploying Visio and/or Project from the Microsoft CDN after installing Office 365 ProPlus is very bandwidth friendly as most of the shared files are already installed.
Here is an example configuration of adding Visio and Project to device after Office 365 ProPlus has already been deployed:

Notice in the above example I have excluded Groove from both Product sections. Groove, OneDrive and Teams operate slightly different at install time and if not excluded from each product they will get installed along with Office 365 ProPlus, Visio and Project Click-to-Run.
The Author
This blog post is brought to you by Eric Wayne, a Sr. Office Deployment expert and ProPlus Ranger at Microsoft. Feel free to share your questions and feedback in the comments below.

I’d like to give you an early heads up on a visual design update that is coming to the Office 365 sign-in experience. These are the screens used to sign in to Microsoft’s apps and services, including Office 365, Azure and Dynamics.
We’re updating the default background image on our sign-in screens to something that’s fresher and more performant. The new image is just 1% the size of the previous one, which reduces bandwidth requirements and improves perceived page load times, especially on slower networks.
 Sign-in screen with old vs new background images
Sign-in screen with old vs new background images
This is solely a visual user interface (UI) change with no changes to functionality. There is no change to your users if you have configured a custom background image in Company Branding for your tenant. This change will only affect screens where the default background image (screenshot on the left above) shows up today.
We plan on rolling this out globally in early-April. If this change affects your users, we recommend updating any documentation that contains screenshots and to give your help desk a heads up.
Writing code for calendaring features is hard. Some of you might say writing any kind of code is hard, and you might have a point, but calendaring is particularly tricky. Why’s that? Well, consider time zones for a start – a meeting you set up isn’t necessarily in the same time as it is for me, and then you also invited people, from a whole bunch of other time zones (did you know some time zones are 30 mins off, not a full hour?), and then you made the meeting recurring, not every week, but every third Monday, except for next month, when it’s on Tuesday… and so on and so forth. But you got a meeting set up, all good.
And then one of the attendees happens to live in a country that decided to implement Daylight Saving Time (DST) and change the local time by an hour. Just in that country.
And we have an good example, as Brazil changed their DST rules in 2019 to eliminate DST and those changes are coming up very soon and they might impact users even with the latest OS updates applied. Users may see various issues with “off by an hour” calendar items when using the Brasilia time zone.
Sometimes we get caught out by a DST change made by a country, or a particular change needs us to code something new to account for it, and for the most part we make it so you don’t notice. But despite our best efforts sometimes users notice meetings are off by an hour. Then the users call you, their IT Pro to complain.
What do you do? There are a number of things we recommend, and so we wanted to share some simple advice on what to do, if it happens.
The “off by one hour” issue can vary widely in terms of scope and symptom, although it is typically limited to recurring appointments and meetings. For example, a user might report:
- Every single recurring meeting is off by an hour, but only in Outlook on the Web (OWA). The meetings render correctly in Outlook for Windows.
- Only a few meetings are off by an hour, but they show incorrectly in both OWA and in Outlook for Windows.
- Only exceptions to a recurring meeting are off by an hour, and only for attendees, not for the organizer.
- Only existing meetings that were created BEFORE the Windows Operating System DST patches were applied are off by an hour.
- Some other possible variation of meeting creation, attendee vs organizer, all vs some, OWA or Outlook desktop, etc.
The #1 best thing you can do to avoid seeing these issues in the first place is to keep your client software and operating system up to date. Sorry if that’s obvious to you, but the OS is the master time source for the client (in OWA’s case that means Exchange Online), and sometimes these DST patches require an update to Windows/Mac/Linux – so keep them patched. Sometimes we need to patch Outlook for Windows, Mac, iOS or Android, and so keeping the client up to date can prevent these issues from showing up. There’s a strong case to be made here for switching to Office 365 ProPlus and having updates regularly applied.
These DST issues can also require server-side changes. Exchange Online does all that for you, of course. In an on-premises world you need to update your servers, so make sure you keep up to date on Cumulative Updates (CU’s) for Exchange and OS updates.
Assuming you’ve done all that, your clients and servers/services are up to date – what then?
You need to figure out how large the scope of this issue is for your users. Is it every user? Is it Outlook for Windows only? What about OWA, does that work? Because the easiest thing might be to have the user switch to another client app until you figure it out.
If it’s only a subset of users (as you only have a small number of users in that geography where DST changed the time) perhaps you decide to manually ‘fix’ the meetings. If so, here’s what we suggest;
- Make sure the DST patches/updates are in place.
- Make sure you note any existing meeting exceptions that might exist if the problem meeting is recurring.
- Have the organizer cancel the meeting that is problematic.
- Have the organizer create and send a new meeting so that the start time correctly takes into account the new DST rules.
- Recreate the needed exceptional instances.
We also see cases where users ‘fixed’ their meetings ahead of a patch/update by just dragging them to the ‘correct’ start time, which then results in them breaking again when updates are installed (and their automatic changes come into effect) – that’s confusing but it’s all the same issue.
We realize re-creating the meeting series is a bit inconvenient, but that’s because time zone rule information is stored on the meeting itself and re-creating it on a patched machine will ensure the correct rules are being used for that series. And it’s often the quickest solution. But what if the impact is too large to handle that way, and you’ve made sure your clients are patched – then you should call into support and get some advice.
On multiple occasions we have made service side changes in Exchange Online to ‘fix’ it there. Those changes do make it to on-prem, but not until the next CU typically.
We give you a lot of flexibility in how you can create meetings (and we are not done improving meetings by a long shot) but it sometimes feels like it’s something of a minor miracle any of us ever get to meet and talk to each other at all, it really is. We celebrate people meeting every day, and we work really hard on this stuff, all the time, to make sure changes such as DST are accounted for.
We’re working on the Brazilian DST issue very hard right now, but we want to call it out so admins with users in that timezone are aware, and have a chance to make sure patches are applied, users are aware and so on. We’ll get things patched and fixed in time, no doubt, but we thought this a good time to broadly discuss DST, what it means, what you can do, and why writing code for calendaring can sometimes be a bit hard.
The Office 365 Calendaring Team
On January 22, 2020 we announced in advance that the Microsoft Search in Bing browser extension would be made available through Office 365 ProPlus on Windows devices starting at the end of February. Since then, we’ve heard from many customers who are excited about the value Microsoft Search provides through Bing and the simplicity of deploying that value through Office 365 ProPlus. With Microsoft Search integrated, Bing becomes a single search engine for users to find what they need – both from inside their organization and the public web.
But we’ve also heard concerns about the way we were planning to roll this value out. Most importantly, we heard that customers don’t want Office 365 ProPlus to change search defaults without an opt-in, and they need a way to govern these changes on unmanaged devices.
Based on your feedback, we are making a few changes to our plan:
- The Microsoft Search in Bing browser extension will not be automatically deployed with Office 365 ProPlus.
- Through a new toggle in Microsoft 365 admin center, administrators will be able to opt in to deploy the browser extension to their organization through Office 365 ProPlus.
- In the near term, Office 365 ProPlus will only deploy the browser extension to AD-joined devices, even within organizations that have opted in. In the future we will add specific settings to govern the deployment of the extension to unmanaged devices.
- We will continue to provide end users who receive the extension with control over their search engine preference.
Due to these changes, the Microsoft Search in Bing extension will not ship with Version 2002 of Office 365 ProPlus. We will provide an updated timeline for this rollout over the next few weeks. For more detailed information about deploying Microsoft Search in Bing through Office 365 ProPlus, please refer to this support article. Learn more about rolling out Microsoft Search in Bing to your organization by reading this user adoption guide.
Thank you for your ongoing feedback. Please continue to share with us through UserVoice.

Office.com is the URL for an experience that we’ve been building for a couple of years. We designed it to be your work hub experience and help you quickly get to the apps, tools, documents, and content you use on a daily basis. We’ve also brought intelligence into the experience that customizes the experience based on your activities.
 Figure 1 – Office.com home page
Figure 1 – Office.com home page
Office.com includes the Office 365 app launcher, which opens when you click the app launcher icon . The app launcher, which in addition to Office.com is also available across the suite, is a menu of your Office 365 apps and services that makes opening and switching between apps easy.
 Figure 2 – Office 365 app launcher
Figure 2 – Office 365 app launcher
We’re rolling out some changes to the way pinned applications work on Office.com and in the app launcher:
- We’ve provided admin controls in the Azure Active Directory portal that enable admins with the Cloud application administrator, Application administrator or Global administrator role to pin up to three apps to Office.com and the app launcher. Any app added by an admin can be unpinned by the user at any time. Office.com and the app launcher are now one experience and will show the same set of apps.
- There’s no need to manually pin apps to the app launcher because the system now automatically pins apps for you based on usage. Any app added automatically can be unpinned at any time.
- In the previous experience, apps were removed after they were unused for a certain period of time. In the updated experience, apps will remain until manually unpinned.
 Figure 3 – Office 365 gallery
Figure 3 – Office 365 gallery
We’re also rolling out a change that provides admins through the Azure Active Directory portal with the ability to group apps and customize the view of the Office 365 gallery. The Office 365 gallery enables you to explore and learn about available applications. This customization can be done via the “collections” blade in the Azure Active Directory admin portal. For more information, see Help your workforce discover and connect to all their apps with the My Apps portal refresh.
Customers will see these changes rolled out soon. We welcome your comments and feedback so be sure to let us know what you think of these changes.
–The Office.com and app launcher team













