
The Microsoft Graph Security API add-on for Splunk is now supported on Splunk Cloud, in addition to Splunk Enterprise, and includes support for Python 3.0. The support is enabled as an enhancement to the Microsoft Graph Security API add-on for Splunk released last year. Refer to the Microsoft Graph Security API add-on for Splunk announcement blogpost for further details. This add-on enables customers to easily integrate security alerts and insights from their security products, services, and partners in Splunk. The Splunk add-on is built by Microsoft, certified by Splunk, and is available on Splunkbase at no additional cost.
This add-on, powered by the Microsoft Graph Security API, supports streaming of alerts from different Microsoft solutions like Microsoft Defender ATP, Azure Sentinel, Azure Security Center, and more into Splunk using a single add-on and common schema, enabling easier correlation of data across these products.
Note: If you have an earlier version of the Microsoft Graph Security API add-on installed on Splunk Enterprise, and upgrade to this version, please follow the upgrade guidance to reconfigure your inputs.
Getting Started
Choose one of these options depending on your scenario.
Scenario: New Installations on Splunk Cloud or Splunk Enterprise
Follow these steps to install and configure this app as a first-time add-on user. Refer to the documentation for more details.
- Register your application for this Splunk add-on on Azure portal.
- Configure permissions and be sure to add the SecurityEvents.Read.All permission to your application. Get your Azure AD tenant administrator to grant tenant administrator consent to your application. This is a one-time activity unless permissions change for the application.
- Copy and save your registered Application ID and Directory ID from the Overview page. You will need them later to complete the add-on configuration process.
- Generate an application secret by going to Certificates & secrets Save the generated secret as well for add-on configuration purposes.
- In Splunk, click on Find More Apps to browse more apps.
- Search for Microsoft Graph Security as shown below (the picture below is on Splunk Cloud).
 Find the add-on
Find the add-on
- Installation of the add-on
- For Splunk Enterprise – Install Microsoft Graph Security API add-on for Splunk. Restart, if prompted to do so.
- For Splunk Cloud – This add-on requires an Inputs Data Manager (IDM) on Splunk Cloud. Contact Splunk Cloud support per the Splunk Cloud IDM installation guidance.
- Verify that the add-on appears in the list of apps and add-ons as shown in the diagram below.
 Add-on installed
Add-on installed
- Set up a new account in the Account tab in the Configuration page. Then click Add to create an account.
- Enter a unique Account Name, the Application ID and Client Secret registered in abovementioned steps 1 through 4 as shown in the diagram below.
 Add account
Add account
- Configure Microsoft Graph Security data inputs illustrated in the diagram below as per the detailed guidance in the section Configuring Microsoft Graph Security data input. This add-on provides the capability to pre-filter your data by specific alert providers or by alert category or severity, etc. by specifying the OData Filter field as shown in the diagram below.
 Add input
Add input
- Now you can use your Microsoft Graph Security alerts for further processing in Splunk, in dashboards, etc.
If you have Splunk and relevant add-ons running behind a proxy server, follow the additional steps for Splunk behind a Proxy Server in the installation documentation for this add-on. For specific guidance on distributed set up, follow the steps in Where to Install the add-on in the installation documentation for this add-on
Scenario: Upgrade on Splunk Enterprise
If you have an existing version of the add-on installed on Splunk Enterprise that is lower than this version (1.1.0), the best practice recommended is to remove your older version of the Microsoft Graph Security API add-on for Splunk before re-installing version 1.1.0 of the Microsoft Graph Security API add-on for Splunk per abovementioned guidelines.
If you are upgrading on Splunk Enterprise, follow these steps.
- Disable all your inputs before you upgrade the add-on. Otherwise you may see errors in the log files which may result data loss against your already configured inputs.
- On the app list, navigate to the Microsoft Graph Security add-on for Splunk, to see an option to upgrade the app. Click on Update button.
- A new screen appears with the standard Splunk Terms to upgrade an app. Click Accept and Continue.
 Splunk terms
Splunk terms
-
Enter your username and password to log in the app. Click Login and Continue.  Login and continue
Login and continue
- After login, an Overview page appears, and the Update button disappears. Follow the instructions in the Configuring Microsoft Graph Security data inputs section in the installation documentation for this add-on to get alerts from Microsoft Graph Security API using the new configuration experience
Closing
We would love your continued feedback on this add-on. Please share your feedback by filing a GitHub issue.
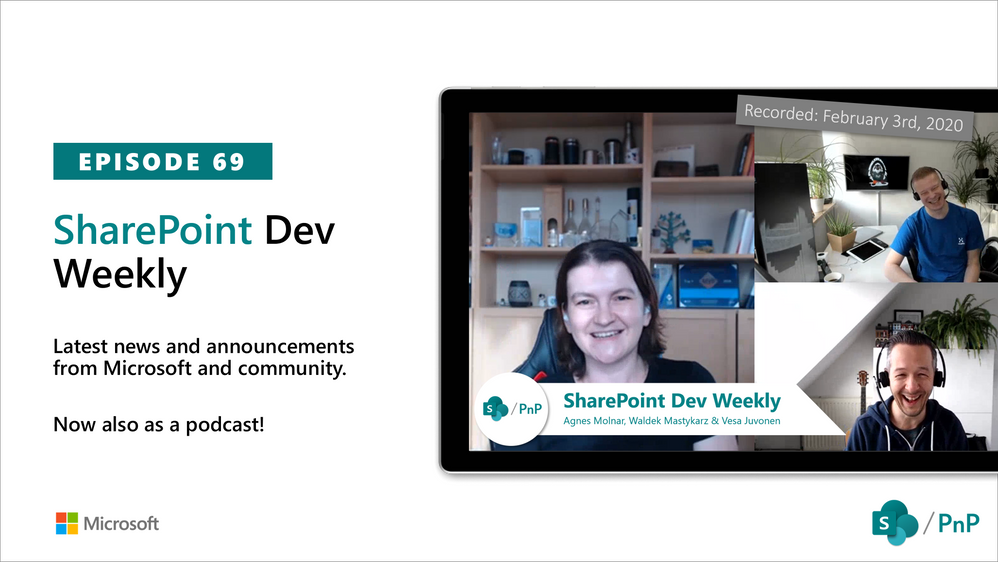

In this session of SharePoint Dev Weekly, hosts – Vesa Juvonen (Microsoft), Waldek Mastykarz (Rencore), and typically a special guest from the SharePoint PnP Community, discuss the latest news and topics around SharePoint development.
In this episode, Vesa and Waldek are joined by Agnes Molnar, owner of Search Explained based in Budapest, delivering consulting and training services worldwide. In addition to drawing attention to the recent advancements being delivered by the SharePoint Community and Microsoft, Vesa, Waldek and Agnes’ discussion this week centered on why search is again cool.
This episode was recorded on Monday, February 3, 2020.

Office.com is the URL for an experience that we’ve been building for a couple of years. We designed it to be your work hub experience and help you quickly get to the apps, tools, documents, and content you use on a daily basis. We’ve also brought intelligence into the experience that customizes the experience based on your activities.
 Figure 1 – Office.com home page
Figure 1 – Office.com home page
Office.com includes the Office 365 app launcher, which opens when you click the app launcher icon . The app launcher, which in addition to Office.com is also available across the suite, is a menu of your Office 365 apps and services that makes opening and switching between apps easy.
 Figure 2 – Office 365 app launcher
Figure 2 – Office 365 app launcher
We’re rolling out some changes to the way pinned applications work on Office.com and in the app launcher:
- We’ve provided admin controls in the Azure Active Directory portal that enable admins with the Cloud application administrator, Application administrator or Global administrator role to pin up to three apps to Office.com and the app launcher. Any app added by an admin can be unpinned by the user at any time. Office.com and the app launcher are now one experience and will show the same set of apps.
- There’s no need to manually pin apps to the app launcher because the system now automatically pins apps for you based on usage. Any app added automatically can be unpinned at any time.
- In the previous experience, apps were removed after they were unused for a certain period of time. In the updated experience, apps will remain until manually unpinned.
 Figure 3 – Office 365 gallery
Figure 3 – Office 365 gallery
We’re also rolling out a change that provides admins through the Azure Active Directory portal with the ability to group apps and customize the view of the Office 365 gallery. The Office 365 gallery enables you to explore and learn about available applications. This customization can be done via the “collections” blade in the Azure Active Directory admin portal. For more information, see Help your workforce discover and connect to all their apps with the My Apps portal refresh.
Customers will see these changes rolled out soon. We welcome your comments and feedback so be sure to let us know what you think of these changes.
–The Office.com and app launcher team

Am a keen follower of Microsoft's SharePoint Blog and proud to provide this direct from the Microsoft Tech Community:

2020 is officially here and we are ready to help you understand and master all the possibilities that are available in the new modern SharePoint. If you haven’t had a chance to sign up for our hands-on Intelligent Intranet Accelerator Workshop yet, now is your chance.
We have a team of enthusiastic SharePoint, One Drive, Yammer and Stream experts traveling the globe in 2020. From half-day workshops to multiple day shows with breakouts and hands on training, the team is ready! No matter where you are in the world, we will be close by to help you discover the art of the possible with Microsoft and SharePoint technologies. Come see the team at an event near you!
February 2020
February 7 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour, Washington DC
As part of Microsoft Ignite The Tour, the Microsoft Intelligent Intranet Accelerator Workshop will bring a deeply technical and immersive hands-on experience where you will build real-world applications to connect, succeed, and engage – faster. You will enjoy a plethora of keynotes, breakout sessions and one-on-one networking opportunities. This free event provides technical training led by Microsoft experts and your community. You’ll learn new ways to build solutions, migrate and manage infrastructure, and connect with local industry leaders and peers.
Register Today!
February 11 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour, Dubai
The Microsoft Intelligent Intranet Accelerator Workshop is a hands-on session within Microsoft Ignite The Tour in this location. By registering, you’ll receive instant access to not only the Microsoft Intelligent Intranet Accelerator Workshop, but also the free 2-day Microsoft Ignite The Tour.
Register Today!
February 12 – The Intelligent Intranet Accelerator Workshop – Hosted at the Microsoft Offices in Sydney, Australia
Get inspired with the art of the possible at the FREE Microsoft Intelligent Intranet Accelerator Workshop. Complete the registration today and reserve your spot in your city. By attending the workshop, you’ll walk away with the tools and capabilities necessary to accelerate your time-to-value.
Register today!
February 18 – The Intelligent Intranet Accelerator Workshop- Featured as part of SPTechCon San Francisco 2020
Featured as a part of SPTechCon San Francisco 2020, the Microsoft Intelligent Intranet Accelerator Workshop will bring a deeply technical and immersive hands-on experience where you will build real-world applications to connect, succeed, and engage – faster.
Register today!
February 21 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour Singapore
The Microsoft Intelligent Intranet Accelerator Workshop is a hands-on session within Microsoft Ignite The Tour in this location. By registering today, you’ll receive instant access to not only the Microsoft Intelligent Intranet Accelerator Workshop, but also the free 2-day Microsoft Ignite The Tour. You will enjoy a plethora of keynotes, breakout sessions and one-on-one networking opportunities. This free tour provides technical training led by Microsoft experts and your community. You’ll learn new ways to build solutions, migrate and manage infrastructure, and connect with local industry leaders and peers.
Register today!
February 28 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour, Copenhagen
As part of Microsoft Ignite The Tour, the Microsoft Intelligent Intranet Accelerator Workshop will bring a deeply technical and immersive hands-on experience where you will build real-world applications to connect, succeed, and engage – faster. You’ll learn new ways to build solutions, migrate and manage infrastructure, and connect with local industry leaders and peers.
Register today!
March 2020
March 10 – The Intelligent Intranet Accelerator Workshop – Hosted at the Microsoft Offices in Amsterdam
Get inspired with the art of the possible at the FREE Microsoft Intelligent Intranet Accelerator Workshop. Complete the registration today and reserve your spot in your city. By attending the workshop, you’ll walk away with the tools and capabilities necessary to accelerate your time-to-value.
Register today!
March 25 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour Hong Kong
The Microsoft Intelligent Intranet Accelerator Workshop is a hands-on session within Microsoft Ignite The Tour in this location. By registering below, you’ll receive instant access to not only the Microsoft Intelligent Intranet Accelerator Workshop, but also the free 2-day Microsoft Ignite The Tour.
Register today!
April 2020
April 16 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour Chicago
The Microsoft Intelligent Intranet Accelerator Workshop is a hands-on session within Microsoft Ignite The Tour in this location. By registering below, you’ll receive instant access to not only the Microsoft Intelligent Intranet Accelerator Workshop, but also the free 2-day Microsoft Ignite The Tour. You will enjoy a plethora of keynotes, breakout sessions and one-on-one networking opportunities. This free tour provides technical training led by Microsoft experts and your community. You’ll learn new ways to build solutions, migrate and manage infrastructure, and connect with local industry leaders and peers.
Register today!
April 28 – The Intelligent Intranet Accelerator Workshop- Hosted at the Microsoft Offices in Berlin, Germany
Get inspired with the art of the possible at the FREE Microsoft Intelligent Intranet Accelerator Workshop. Complete the registration today and reserve your spot in your city. By attending the workshop, you’ll walk away with the tools and capabilities necessary to accelerate your time-to-value.
Register today!
May 2020
May 5 – The Intelligent Intranet Accelerator Workshop- Featured as part of Microsoft Ignite The Tour Stockholm
As part of Microsoft Ignite The Tour, the Microsoft Intelligent Intranet Accelerator Workshop will bring a deeply technical and immersive hands-on experience where you will build real-world applications to connect, succeed, and engage – faster. You will enjoy a plethora of keynotes, breakout sessions and one-on-one networking opportunities. This free tour provides technical training led by Microsoft experts and your community. You’ll learn new ways to build solutions, migrate and manage infrastructure, and connect with local industry leaders and peers.
Register today!
We hope we will see you on the road!
Register today for a city near you for our Intelligent Intranet Accelerator Workshop!
The above is kindly provided by the Microsoft Tech Community!
Am a keen follower of Microsoft's SharePoint Blog and proud to provide this direct from the Microsoft Tech Community:

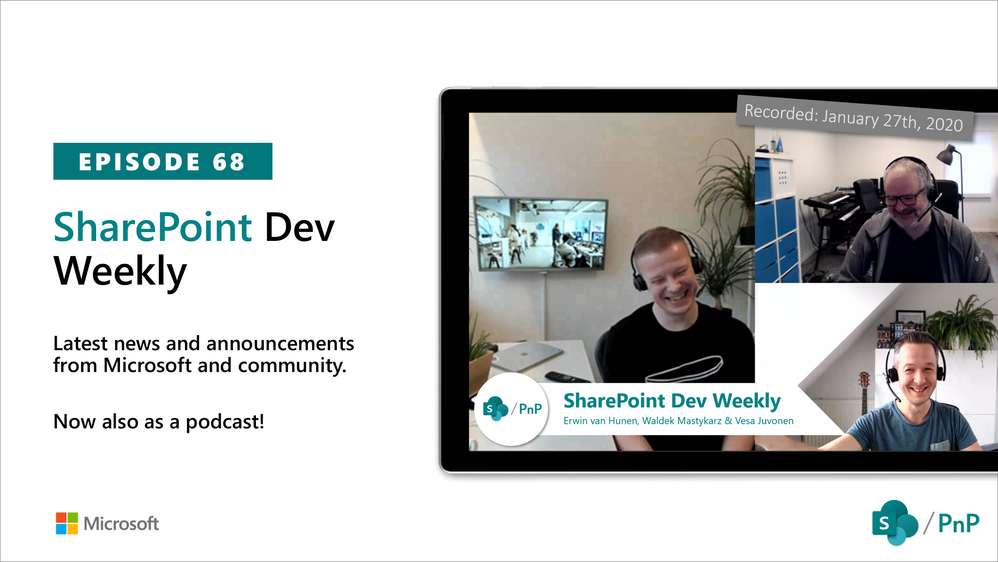
In this session of SharePoint Dev Weekly, hosts – Vesa Juvonen (Microsoft), Waldek Mastykarz (Rencore), and typically a special guest from the SharePoint PnP Community, discuss the latest news and topics around SharePoint development.
In this episode, Vesa and Waldek are joined by Erwin van Hunen – Lead architect at Valo Intranet. In addition to drawing attention to the recent advancements being delivered by the SharePoint Community and Microsoft, Vesa, Waldek and Erwin’s discussion this week focused on Erwin’s pioneering work on and evolution of PnP Provisioning and PnP PowerShell, the shaping of a tenant templating engine (support for Azure, Teams, OneDrive, SharePoint) – PnP .Net Core SDK, .NET frameworks, and tools – CLI and PowerShell.
This episode was recorded on Monday, January 27, 2020.
The above is kindly provided by the Microsoft Tech Community!

Early last year, we launched the Microsoft 365 compliance center for Microsoft 365 E3 and E5 customers. Since then we’ve been hard at work making it a unified and comprehensive compliance administration console for all our customers. Today, we are excited to announce that we’ve shipped several new enhancements to the portal, and are making it available to all customers with Microsoft 365, Office 365, Enterprise Mobility + Security (EMS), and Windows 10 Enterprise plans.

In this release we’ve focused on three areas: integrated management, easier on-boarding, and improved controls.
Integrated management
Microsoft 365 compliance center is now truly a one-stop compliance destination. We’ve converged disparate admin experiences into one console, and we’ve built integrations with third-party data as well, giving you a single pane of glass to manage your entire compliance posture
- Converged console
Microsoft 365 compliance center is now truly a single destination to manage your compliance posture. Admins no longer need to go to the Office 365 Security & Compliance Center for compliance administration. Existing compliance capabilities within the Office 365 Security & Compliance Center are now available in the Microsoft 365 compliance center. Any data and policies authored in the Office 365 portal will automatically carry over to the Microsoft 365 one, since they share the same data back-end.
Additionally, we’ve introduced several exciting features and capabilities on the Microsoft 365 compliance center. Some of them are highlighted in this post, but you can see the full list here.
While you can choose to continue using Office 365 Security & Compliance Center by visiting protection.office.com, we encourage you to move your admin experience to the Microsoft 365 compliance center, since all the new capabilities will be available only in the new center.
2. Data connectors
You can now easily import and archive your business data from third-party social media platforms, instant messaging platforms, and document collaboration platforms. After this data is imported, you can apply Microsoft 365 compliance features—such as Litigation Hold, eDiscovery, In-Place Archiving, Auditing, Communication compliance, and retention policies—to this data. Examples of supported sources are Bloomberg, LinkedIn, Facebook, and Twitter. Learn more
 Easier onboarding
Easier onboarding
A recurring theme of feedback from you, our customers, has been that compliance is complex and it’s hard to get started. We looked at ways to make this easier and have introduced three key capabilities towards this goal.
- Microsoft Compliance Score helps you simplify compliance and reduce risks and gives you simple, actionable recommendations to improve your compliance posture.
- Solution catalog: We’ve organized our compliance capabilities into integrated solutions that help you manage an end-to-end compliance scenario. A solution’s capabilities might include a combination of policies, alerts, reports, end-user facing experiences, and more. The solution catalog is your one-stop-shop for discovering, learning about, and quickly getting started with our compliance and risk management solutions. It provides information about the benefits and target use cases for a solution, and how to get started with it. Solutions in the catalog are organized into three compliance categories: Information protection & governance, Insider risk management, and Discovery & response.

 3. Insights: To make it easier to get started with compliance, we’ve provided out-of-the-box insights into the sensitive data across various locations in your organization: Exchange, SharePoint, OneDrive for Business, and endpoints. You can easily determine the right retention and DLP policies to apply based on these insights. This feature is in public preview.
3. Insights: To make it easier to get started with compliance, we’ve provided out-of-the-box insights into the sensitive data across various locations in your organization: Exchange, SharePoint, OneDrive for Business, and endpoints. You can easily determine the right retention and DLP policies to apply based on these insights. This feature is in public preview.


Improved administrative controls
We’ve invested in more administrative flexibility by adding new roles and enabling more customizable experiences.
- Support for new roles
We’ve added support for the much-requested Global Reader and Compliance Data Admin roles. Learn more about these roles. These new roles allow you to delegate administration tasks and reduce the number of Global administrators in your directory.
The Global Reader role can view everything a Global administrator can view without the ability to edit or change. The Compliance Data Admin role can create and manage compliance data policies and alerts.
2. Customizable experience
Every admin has different priorities when it comes to compliance. The Microsoft 365 compliance center allows you to customize your experience to suit your needs. You can customize the homepage dashboard by selecting from a catalog of cards.

You can also customize the left navigation bar by selecting and pinning the solutions that you use most frequently.

If you’re ready to try the new center out, be sure to visit the Microsoft 365 compliance center at compliance.microsoft.com today. You can learn more about the new center in this supporting documentation.

The Office cloud policy service (OCPS) is a cloud-based service that enables you to apply policy settings for Office 365 ProPlus on a user’s device. The policy settings roam to whichever device the user signs into and uses Office 365 ProPlus. As end users become increasingly mobile, IT Pros need a single approach to secure Office 365 ProPlus for traditional on-premises domain devices, Azure AD registered devices, Azure AD Joined, and Hybrid Azure AD joined devices. OCPS applies to all scenarios above without the need to download and replicate any content such as Administrative Template files (ADMX/ADML) on-premises. The goal of this blog is to provide some transparency of how the service works to help IT Pros during their validation phase and to encourage transition from classic domain-based policy to OCPS service for Office 365 ProPlus.
Requirements of OCPS
1. At least Version 1808 (August 2018) of Office 365 ProPlus
2. User accounts created in or synchronized to Azure Active Directory (AAD). The user must be signed into Office 365 ProPlus with an AAD based account.
3. Security groups created in or synchronized to Azure Active Directory (AAD), with the appropriate users added to those groups.
4. To create a policy configuration, you must be assigned one of the following roles in Azure Active Directory (AAD): Global Administrator, Security Administrator, or Office Apps Admin.
5. Connectivity to addresses below. Microsoft recommends proxy bypasswhitelist for these URLs
*.manage.microsoft.com, *.officeconfig.msocdn.com, config.office.com over 443
Steps to perform proof of concept and validation
1. Create a test user, ours will be “Kasper Graf”, kgraf@contoso.com.
2. Create security group “OCPS Service Validation” and add user to group within Active Directory Users and Computers.
3. Allow AAD Connect to synchronize user and group to Azure AD. (lunch break 🙂 or force synchronization via commands below)
(optional) From AAD Connect Server and elevated PowerShell, run the following commands:
PS C:WINDOWSsystem32>import-module adsync
PS C:WINDOWSsystem32>Set-ADSyncScheduler -NextSyncCyclePolicyType Delta
PS C:WINDOWSsystem32>Start-ADSyncSyncCycle
Browse Azure AD portal and explore Users – All Users, select Kasper Graf and then Groups. Verify that group “OCPS Service Validation” has been assigned and source says, “Windows Server AD”. This confirms user and group were synced into Azure AD successfully and we can proceed to next steps.
4. Create your first OCPS policy and select “Create” button:

5. Complete input fields, when selecting assigned security group input “OCPS” and service should filter results to “OCPS Service Validation” group. Next, define a policy. For the demo, I chose policy “VBA Macro Notification Settings”, “Enabled” where VBA Macro Notification Settings are set to “Disable all with notification”. Once selections have been made “Create” or “Save”.


6. From Policy Management, we can now see our policy exists.

So, we’ve got a policy, we’ve assigned it to a security group containing our test user, our next step is to validate. My test machine happens to be classic on-premises domain joined machine. My user, Kasper Graf, is signed in with his normal Active Directory credentials which is displayed in upper right hand corner of Word.

Traditional Group Policy uses Client-Side Extensions in Windows to apply policy every 90 minutes. IT Pros can force policy by using command line “gpupdate /force” and inspectverify registry as well as application behavior prior to broad deployment. OCPS checks for policy upon initial Office application launch, calls into cloud service endpoints listed above, determines policy applicability based on group membership and priority assignment and registry keys are populated.
Specifically, there are two locations of interest in registry.
1. HKEY_CURRENT_USERSoftwareMicrosoftOffice16.0CommonCloudPolicy
This will contain information about FetchInterval, 90 minutes is default, as well as record of Last Fetch Time and Last Payload Hash.
2. HKEY_CURRENT_USERSoftwarePoliciesMicrosoftCloud. This key will contain path to registry keys representing the policy assignment. For example, ours will be HKEY_CURRENT_USERSoftwarePoliciesMicrosoftCloudOffice16.0wordsecurity
Vbawarnings = 2 (DWORD)
IT Pros can achieve the same behavior of gpupdate by simply deleting the key HKEY_CURRENT_USERSoftwareMicrosoftOffice16.0CommonCloudPolicy, close Office application and relaunch to fetch policy. I typically use tools like Process Monitor to help trustverify operations of this type with filters such as “Path” contains “CloudPolicy” or where Operation is “RegSetValue” etc. Opening a Word document containing a Macro displaying warning with notification as expected.

FAQ:
How does conflict resolution work if the same policy is set via traditional domain-based policy as well as OCPS?
OCPS takes priority if there are any conflicts with traditional domain-based policies.
Currently policies are limited to user settings. Are there plans on adding machine settings?
Yes. This has been accepted and currently is in our backlog. We hope to have this available next year.
Group Policy provides a view of all policies on the device or for the specified user. Does OCPS support this?
Currently OCPS does not provide a list of all Office policies applied to a specific user or device. This is on our backlog and we hope to have this available next year.
Will OCPS support other platforms such as MacOS, Android and iOS?
Yes, OCPS in the future will also support additional platforms such as MacOS, Android and iOS. We will create additional blog postings per platform once features are generally available.
Are there any environments where OCPS is not available?
The Office cloud policy service isn’t available to customers who have the following plans: Office 365 operated by 21Vianet, Office 365 Germany, Office 365 GCC, or Office 365 GCC High and DoD.
The Author
This blog post is brought to you by Dave Guenthner, a Senior Premier Field Engineer and “ProPlus Ranger” at Microsoft. Feel free to share your questions and feedback in the comments below.

Customers tell us they want easier ways to manage their environments while delivering more productivity value to their employees. This includes helping people quickly find the information they need, a potentially frustrating prospect given the sheer and constantly growing volume of content within an organization. To help IT solve this — and to do so in a way that is easy for you to manage — we are offering the Microsoft Search in Bing extension to Office 365 ProPlus customers starting at the end of February.1,2 To help you prepare, we want to share guidance on how you can configure Office 365 ProPlus updates to best meet your organization’s search needs.
Microsoft Search in Bing
Bing is a gateway to Microsoft Search, a unified enterprise search solution that provides contextual work-related information using data sources in Office 365 including SharePoint, Microsoft OneDrive for Business, and Exchange. Microsoft Search delivers personalized results surfaced by the Microsoft Graph to make search in your organization more effective, increase productivity, and save everyone time.
Employees can search for colleagues by typing the title, team name, or even office location into the address bar. They can also search for office location and get answers that show floor plans for directions. They can even get definitions for company acronyms.
As part of Microsoft 365, Microsoft Search is on by default for all Microsoft apps that support it. This update is designed to enable an accessible and familiar entry point for your users: a search engine.
Deploy Microsoft Search through Office 365 ProPlus
You have told us that you want a single tool to deploy all desktop components of Office 365. To simplify the process of deploying Microsoft Search, we’re making the Microsoft Search in Bing extension available through Office 365 ProPlus with version 2002, alongside Word, Excel, PowerPoint, Outlook, OneDrive, and Teams. This extension will be installed with new installations of Office 365 ProPlus and when existing installations are updated. If Bing is already the default search engine, the extension will not get installed.
If you don’t want to deploy the extension to your users, you can exclude it by using the Office Deployment Tool or Group Policy. There are also ways to exclude it if you’re using Microsoft Endpoint Configuration Manager (current branch) or Microsoft Intune. For more information about how to manage the extension, read this article.
Honor your users’ search preferences
Even if you deploy the Microsoft Search in Bing extension with Office 365 ProPlus, users will still have an opportunity to choose their search engine. The first time your users open Google Chrome after the extension for Microsoft Search in Bing is installed, they will have an option to change back their search preferences by taking a few simple steps.
 Mockup of the search toggle in Chrome browsers (subject to change).
Mockup of the search toggle in Chrome browsers (subject to change).
Learn more about the user benefits of this change by downloading the Microsoft Search in Bing Adoption Kit (zip file) and this user adoption guide. As always, please visit our Tech Community page to learn more about Office 365 ProPlus, and share your feedback and insights.
Footnotes
- This change is enabled for new and existing Office 365 ProPlus installations in Australia, Canada, France, Germany, India, the United Kingdom, and the United States. As we add locations, we will notify admins through the Message Center.
- The extension will be released to the Monthly Channel in late February 2020. Release for the Semi-Annual Channel (Targeted) and Semi-Annual Channel are coming soon.
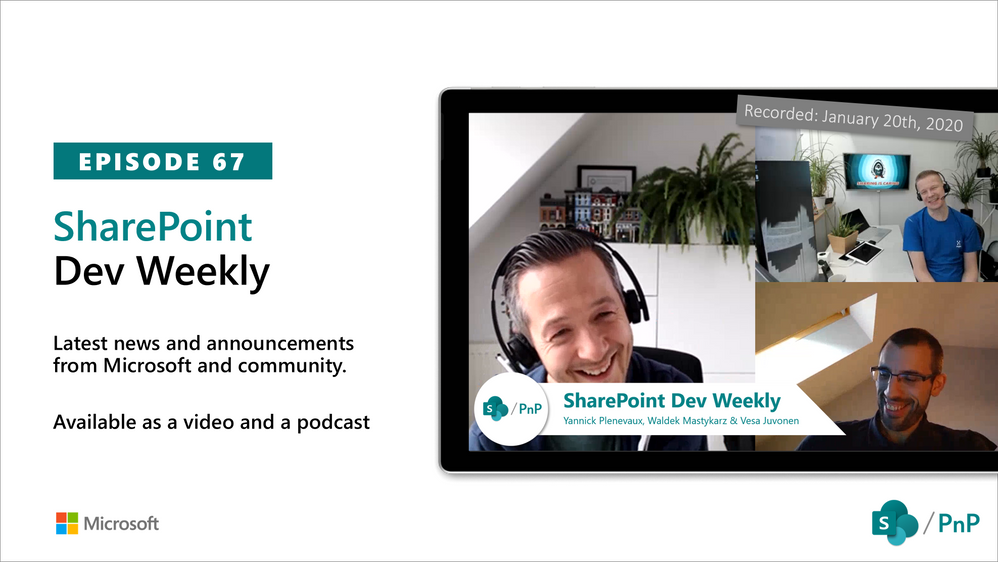
Am a keen follower of Microsoft's SharePoint Blog and proud to provide this direct from the Microsoft Tech Community:

In this session of SharePoint Dev Weekly, hosts – Vesa Juvonen (Microsoft), Waldek Mastykarz (Rencore), and typically a special guest from the SharePoint PnP Community, discuss the latest news and topics around SharePoint development.
In this episode Vesa and Waldek are joined by Yannick Plenevaux – Microsoft 365 Solutions Architect, new MVP and owner of PVX Solutions, Belgium.
This episode was recorded on Monday, January 20, 2020.
The above is kindly provided by the Microsoft Tech Community!

Security research shows most successful enumeration and brute force attacks use either NTLM or Kerberos authentication protocols for entry. In fact, they’re the most popular discovery-phase attacks Azure ATP observed in the past 12 months.
Why does account enumeration matter?
In an account enumeration attack, the malicious actor attempts to use different usernames to access a server, with the goal of discovering which users exist within the organization. Once an attacker identifies these users, a brute force attacks begins to get their credentials and move laterally within the organization toward higher-profile assets.
What is NTLM and how does it work?
The NTLM protocol authenticates users and computers, using a challenge/response mechanism designed to prove to a server or domain controller that the user knows the password associated with the account they’re trying to access. Whenever a new access token is needed for domain accounts, a resource server must contact the domain controller to verify the identity of a computer or user.
Standard NTLM authentication flow includes 2 major steps:
- The user tries to access a resource server.
- The resource server validates the user with a domain controller.

How does Azure ATP provide visibility into NTLM authentications?
Network traffic and Windows Events 4776 and 8004 capture NTLM data. In turn, Azure ATP parses the NTLM traffic and events from your domain controllers.
NTLM 8004 events provide full information on your NTLM authentications, including:
- Source account
- Source device
- Accessed resource server
- Domain controller that is doing the account validation
Why do some devices show up as “unknown” in Azure ATP alerts?
The source device in Azure ATP account enumeration and brute force detection alerts can be marked as coming from “unknown” devices, such as Workstation, MSTSC, or Unknown. This happens because the source device name field is occasionally overwritten when the attacker is already inside your organization, or when they try to enumerate accounts from the internet. This is common when the accessed server is opened to the internet and used by adversaries to enumerate users from outside the organization.
With enhanced support for Windows event 8004, Azure ATP now determines which servers were attacked and how the attacks happened.
How can Azure ATP detect the actual server accessed inside the network?
Azure ATP sensors parse Windows event 8004 for NTLM authentications. When NTLM auditing is enabled and Windows event 8004 is logged, Azure ATP sensors automatically read the event and enrich your NTLM authentications with the accessed server data.

In addition, Azure ATP now provides Resource Access over NTLM activity, showing the source user, source device, and accessed resource server:

Example of enhanced NTLM activity details
Use the following links to learn more about enabling NTLM auditing when working with Azure ATP to detect, protect, and remediate NTLM and brute force attacks:
Get Started Today
Just starting your Azure ATP journey? Begin a trial of Microsoft Threat Protection to leverage integrated defenses and unparalleled intelligence across the threat landscape to defend the modern workplace.
Find the add-on
Add-on installed
Add account
Add input
Splunk terms
Login and continue














