 Understand the workflow provisions around SharePoint, Office365, Windows Azure used to improve business process automation, collaboration and productivity.
Understand the workflow provisions around SharePoint, Office365, Windows Azure used to improve business process automation, collaboration and productivity. Read how Service Delivery (automation, data governance, data processing, support), aligns to Information Assurance (IA) and concerns all content management systems.
Read how Service Delivery (automation, data governance, data processing, support), aligns to Information Assurance (IA) and concerns all content management systems. Read how Office365 includes Service Assurance providing resources to carry out risk assessments and audits, and includes a wealth of reports covering security, and the relevant legislation.
Read how Office365 includes Service Assurance providing resources to carry out risk assessments and audits, and includes a wealth of reports covering security, and the relevant legislation. Read how Web Analytics improves the usability of the SharePoint solution, drives collaboration, boosts ROI (Return On Investment); and thus enhances the overall productivity of SharePoint users
Read how Web Analytics improves the usability of the SharePoint solution, drives collaboration, boosts ROI (Return On Investment); and thus enhances the overall productivity of SharePoint users Read how a usable SharePoint solution needs to take into consideration the service standards applicable like design, development, commonality, consistency, tools and cross platform standards.
Read how a usable SharePoint solution needs to take into consideration the service standards applicable like design, development, commonality, consistency, tools and cross platform standards.  Read how automation of an enterprise solution including Maintainability, Availability, Resiliency and Supportability using multiple technologies requires an adoption of an suite that allows you flexibility.
Read how automation of an enterprise solution including Maintainability, Availability, Resiliency and Supportability using multiple technologies requires an adoption of an suite that allows you flexibility.
Microsoft Ignite Pre-Day Workshop: Understanding, optimizing, and troubleshooting Office 365 network
Traditional enterprise network architecture revolves around the pre-cloud world. A world where data, services and applications generally live within the corporate walled garden and thus connectivity is simply from the user locations to where the...
Managing changes in Office 365: An overview of resources
Office 365 gives you the latest updates and features as early as possible so you can continue doing your job productively. For Office 365 services, updates are run in the background as soon as they become available, instead of bundled updates scheduled months apart....
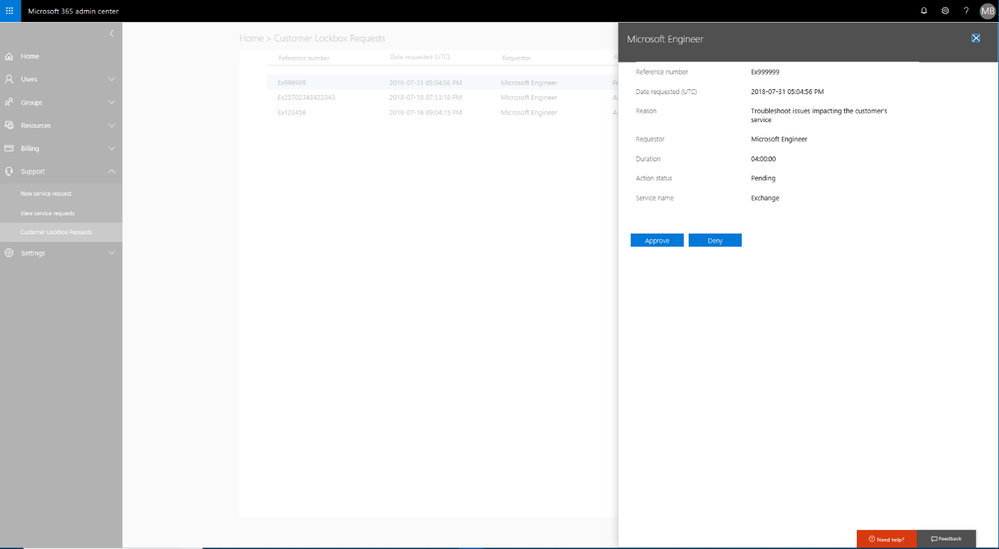
Customer Lockbox Approver Role Now Available
We are excited to share a new capability in Customer Lockbox that can provide more flexibility in who can approve Customer Lockbox requests. Read further to learn more. First, what is Customer Lockbox? Many customers, and in particular regulated...

Customer Lockbox Approver Role Now Available
We are excited to share a new capability in Customer Lockbox that can provide more flexibility in who can approve Customer Lockbox requests. Read further to learn more. First, what is Customer Lockbox? Many customers, and in particular regulated...

Customer Lockbox Approver Role Now Available
We are excited to share a new capability in Customer Lockbox that can provide more flexibility in who can approve Customer Lockbox requests. Read further to learn more. First, what is Customer Lockbox? Many customers, and in particular regulated...

Customer Lockbox Approver Role Now Available
We are excited to share a new capability in Customer Lockbox that can provide more flexibility in who can approve Customer Lockbox requests. Read further to learn more. First, what is Customer Lockbox? Many customers, and in particular regulated...

Customer Lockbox Approver Role Now Available
We are excited to share a new capability in Customer Lockbox that can provide more flexibility in who can approve Customer Lockbox requests. Read further to learn more. First, what is Customer Lockbox? Many customers, and in particular regulated...
2018 Global Office 365 Developer Bootcamp
Following the success of last year, Global Office 365 Developer Bootcamp now becomes an annual event. It is a free, one-day, hands-on training event led by Microsoft MVPs with support from Microsoft and local community leaders. Developers worldwide are invited...
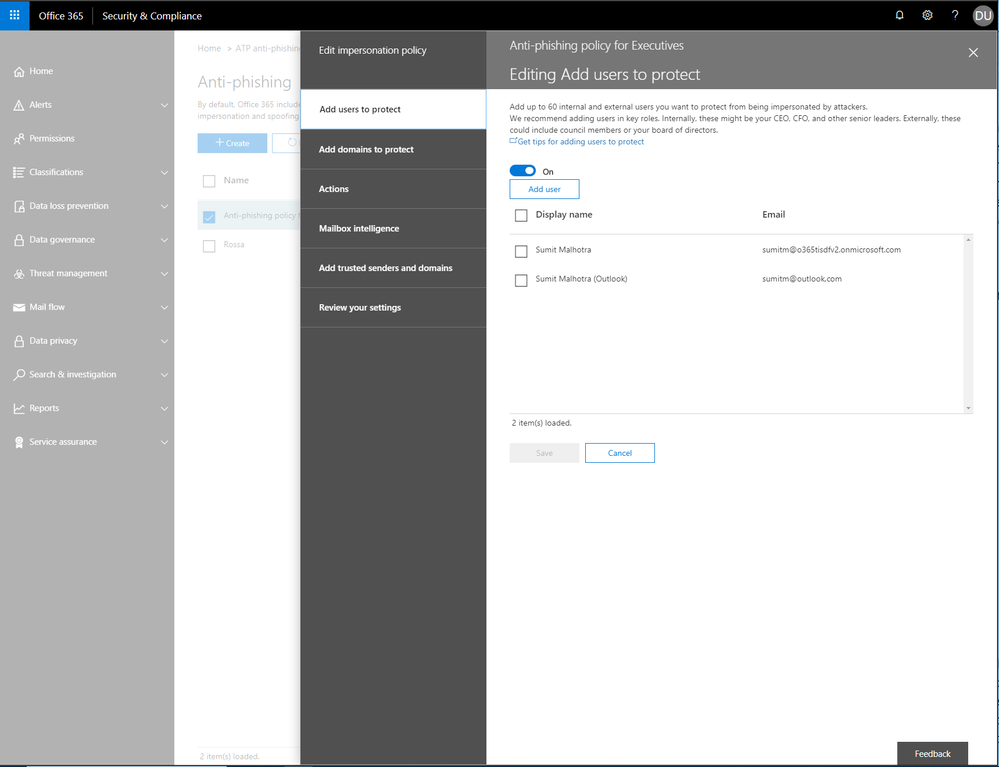
Enhancements to the Office 365 ATP admin experience
Over the last several months, we have made many advancements to Office 365 Advanced Threat Protection (ATP). Due to our impressive malware catch effectiveness, threat actors have altered attack methods to bypass security capabilities leading to an increase in...

Enhancements to the Office 365 ATP admin experience
Over the last several months, we have made many advancements to Office 365 Advanced Threat Protection (ATP). Due to our impressive malware catch effectiveness, threat actors have altered attack methods to bypass security capabilities leading to an increase in...










