The following is provided from Microsoft Security and Compliance blogs at TechCommunity:
I spent several years in the Microsoft internal digital security and risk organization helping to develop various programs to identify insider risks, threats and code of conduct policy violations in collaboration with our human resources (HR) and legal teams. The ability to identify these risks and policy violations and then take action to minimize the negative impact is a priority for organizations worldwide.
Modern workplaces offer innovative technology that employees love, empowering them to communicate, collaborate, and produce with agility. Trusting your employees is the key to creating a dynamic, inclusive workplace and increasing productivity. But, with trust also comes risk. In fact,
a survey by Crowd Research Partners indicated that 90% of organizations feel vulnerable to insider risks and 53% confirmed insider risks against their organization in the previous 12 months.
We know from our own experience that it’s hard to maintain trust without the right visibility, processes and control. However, the effort required to identify these risks and violations is not trivial. Think about the number of people accessing resources and communicating with each other, as well as the natural cycle of people entering and leaving the company. How do you quickly determine what is an intentional risk vs. an unintentional one at scale? And how do you achieve this level of visibility, while aligning to the cultural, legal and privacy requirements in which you operate? For example, truly malicious insiders do things such as intentionally stealing your intellectual property, turning off security controls or harassing others at work. But there are many more situations in which an insider might not even know they are causing a risk to the organization or violating your policies, like when they’re excited about something new they’re working on and send files or photos to tell others about it.
Ultimately, it’s important to see the activities and communications that occurred in the context of intent, in order to take the right course of action. The only way to do this efficiently and at scale is by leveraging intelligence and machine learning, as human driven processes can’t keep up and aren’t always that accurate. Furthermore, a holistic solution to this problem requires effective collaboration across security, HR and legal, as well as a balanced approach across privacy and risk management.
Today I am excited to announce two new Microsoft 365 solutions, Insider Risk Management and Communication Compliance. These solutions can help you and your organization to leverage intelligence to identify and remediate insider risks and code of conduct policy violations, while meeting regulatory requirements.
Insider Risk Management
Insider Risk Management leverages the Microsoft Graph, security services and connectors to human resources (HR) systems like SAP, to obtain real-time native signals such as file activity, communications sentiment, abnormal user behaviors and resignation date.
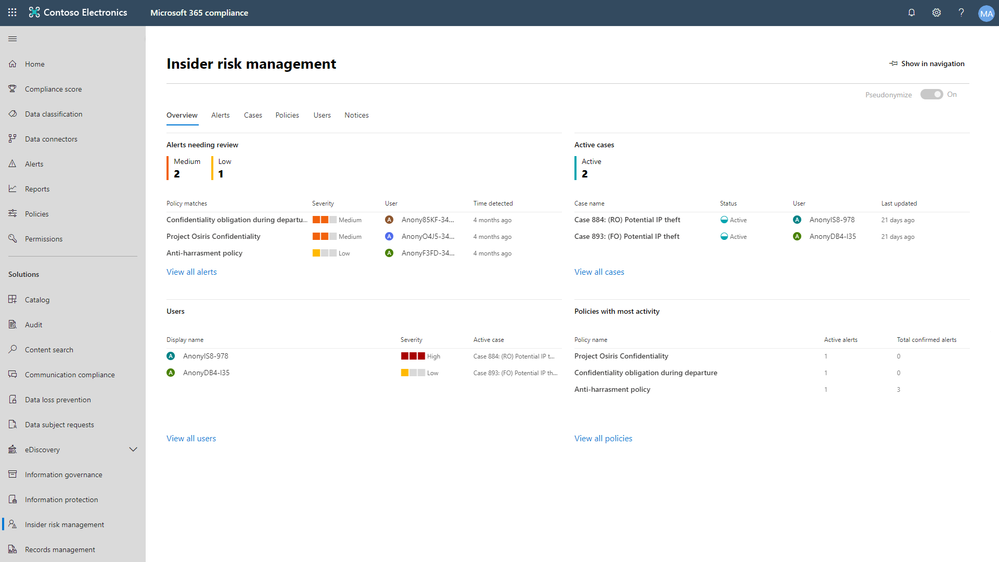
A set of configurable playbooks tailored specifically for risks – such as digital IP theft, confidentiality breach, and HR violations – use machine learning and intelligence to correlate these signals to identify hidden patterns and risks that traditional or manual methods might miss. Using intelligence allows the solution to focus on actual suspicious activities, so you don’t get overloaded with alerts. Furthermore, display names for risky users can be pseudonymized by default to maintain privacy and prevent bias.
A comprehensive 360° view provides a curated and easy-to-understand visual summary of individual risks within your organization. This view includes an historical timeline of relevant in-scope activities and trends associated with each identified user. For example, you could see if a user submitted their resignation, downloaded some files and copied some of them to a USB device. The system also evaluates whether any of those files had classification labels on them and whether they contained sensitive information. With the right permission, the files accessed from Microsoft cloud resources like SharePoint Online can also be made available for the investigator to view, which further helps with the risk determination. Having all this information at your fingertips allows you to quickly decide whether this risk is one that warrants further investigation, saving you considerable time.
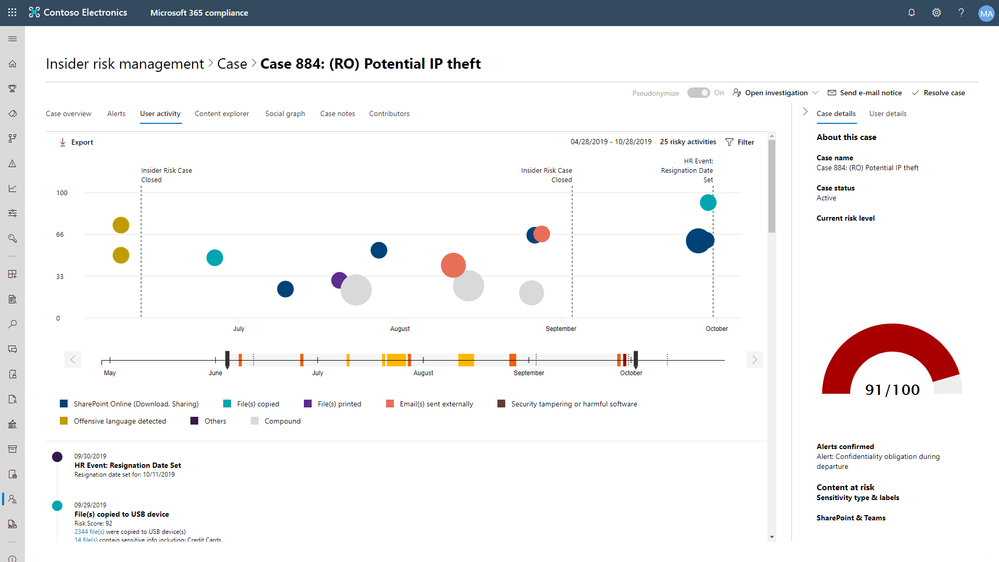
Finally, end-to-end integrated workflows ensure that the right people across security, HR, legal and compliance are involved to quickly investigate and take action once a risk has been identified. For example, if the risk was determined to be unintentional, you could send an email saying this is a violation of company policy with a link to training or the policy handbook. If the risk was determined to be malicious, you could open an investigation that would collate and preserve all the evidence collected, including the documents, and create a case for legal and HR to take appropriate actions.
Insider Risk Management is available as part of the Microsoft 365 E5 suite and is currently in limited private preview. You can sign up for an opportunity to participate
here.
Communication Compliance
Communication Compliance is a brand-new solution that helps all organizations address code-of-conduct policy violations in company communications, while also helping organizations in regulated industries meet specific supervisory compliance requirements. Communication Compliance supports a number of company communications channels, including Exchange email, Teams, Skype for Business Online, Twitter, Facebook and Bloomberg instant messages.
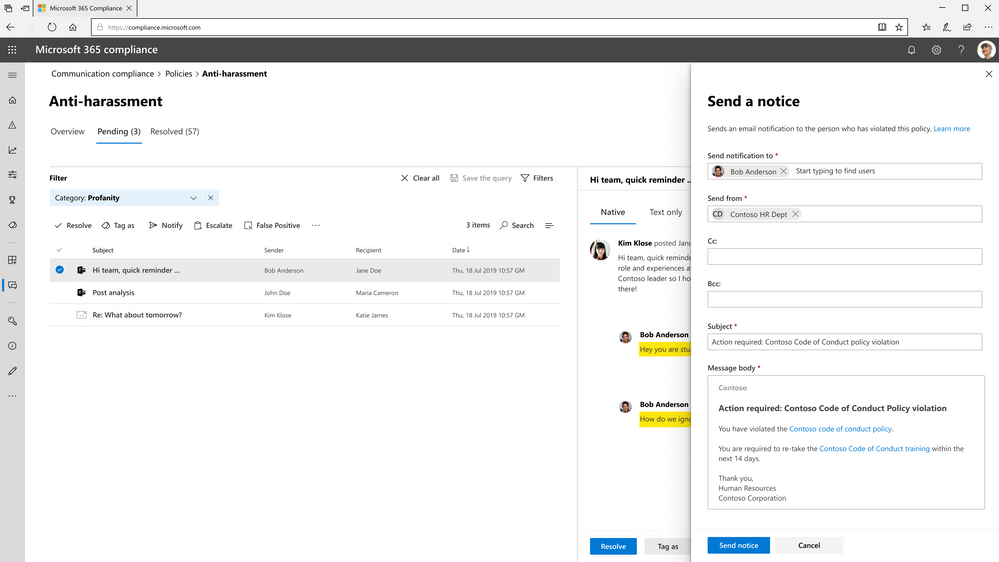
Organizations need the ability to improve investigating potential violations and facilitate taking adequate remediation action based on local regulations. To provide granularity in identifying specific words and phrases, we have three out-of-box machine learning models to identify physical violence, harassment, and profanities. You can also build-your-own trainable classifiers that understand meaning and context that are unique to your organization’s need such as insider trading or unethical practice, freeing you from a sea of false positives.
Once a violation has been flagged and the designated supervisor is alerted, it is important that the review process enables them to efficiently act on violations. Communication Compliance includes features such as historical user context on past violations, conversation threading and keyword highlighting, which together allow the supervisor to quickly triage the violation and take the appropriate remediation actions.
The interactive dashboard provides an effective way to manage the growing volume of communications risks to ensure violations aren’t missed. Proactive intelligent alerts on policy violations requiring immediate attention allows the supervisor to prioritize and focus on the most critical violations first. In addition, violations, actions and trends by policy provide a quick view on the effectiveness of your program.
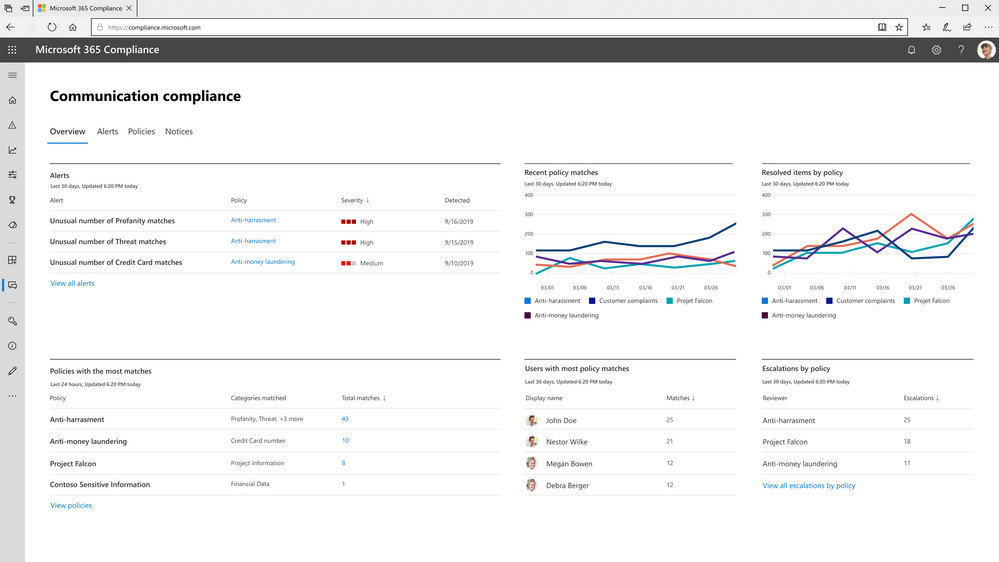
The Financial Industry Regulatory Authority (FINRA) Rule 3110 is a good example of a requirement for regulated organizations to have solutions in place to detect violations in communications. For example, safeguarding against potential money-laundering, insider trading, collusion, or bribery activities between broker-dealers is a critical priority. For organizations in regulated industries, Communication Compliances provides a full audit of review activities and tracking of policy implementation to help you meet the regulatory requirements you may be subject to.
Communication Compliance is available today as part of the Microsoft 365 E5 suite, and you can sign up for a trial or navigate to the Microsoft 365 Compliance Center to get started today.
We encourage customers who are currently using Supervision in Office 365 to use the new Communication Compliance solution to address your regulatory requirements with a much richer set of intelligent capabilities.
Thank you,
Talhah Mir, Principal Program Manager, Microsoft 365 Security and Compliance Engineering
Related Posts
 Security in Office 365 Whitepaper available
Security in Office 365 Whitepaper available SharePoint Site Security – A Best Practice Guide
SharePoint Site Security – A Best Practice Guide Use Supervision to monitor email, Microsoft Teams, manage risk, meet regulatory requirement and more
Use Supervision to monitor email, Microsoft Teams, manage risk, meet regulatory requirement and more Use Supervision to monitor email, Microsoft Teams, manage risk, meet regulatory requirement and more
Use Supervision to monitor email, Microsoft Teams, manage risk, meet regulatory requirement and more Use Supervision to monitor email, Microsoft Teams, manage risk, meet regulatory requirement and more
Use Supervision to monitor email, Microsoft Teams, manage risk, meet regulatory requirement and more Use Supervision to monitor email, Microsoft Teams, manage risk, meet regulatory requirement and more
Use Supervision to monitor email, Microsoft Teams, manage risk, meet regulatory requirement and more
The above was provided from Microsoft Security and Compliance blogs at TechCommunity




















