The following is provided from Microsoft Security and Compliance blogs at TechCommunity:
Today, I’m thrilled to announce the general availability of two extremely popular and valuable features in the Office 365 Advanced Threat Protection offering: Campaign Views and Advanced Compromised user detection and response. These features together greatly amplify the protection of organizations by helping security teams detect compromised users sooner, identify configuration weaknesses faster and improve security posture. And they also help reduce the scope of impact of breaches by giving security teams the tools to respond quickly.
Campaign views:
When we released Campaign Views into public preview a few months ago, we already knew it was an extremely popular and useful capability for security teams, based on the overwhelmingly positive feedback from our close design customer partners. Campaign views offer security teams the full story of how attackers targeted the organization and its users and how their defenses held up (or not).
Security teams can quickly:
- See summary details about the campaign, including when the campaign started, the sending pattern and timeline, how big the campaign was and how many users fell prey to it.
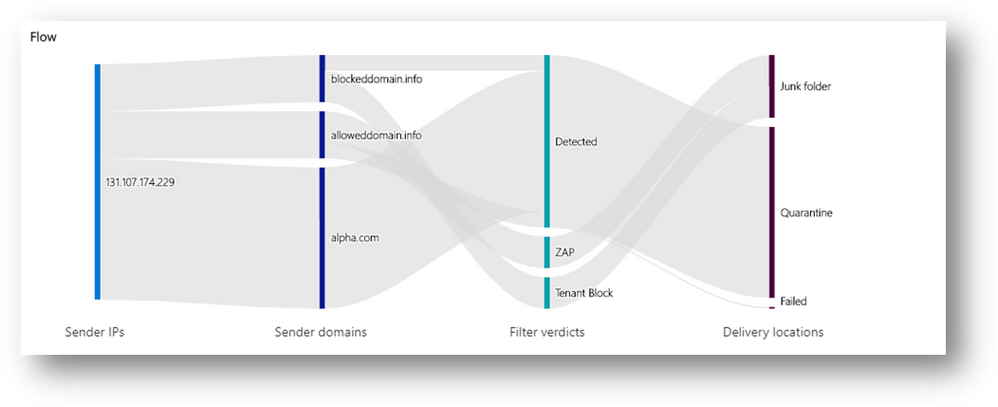
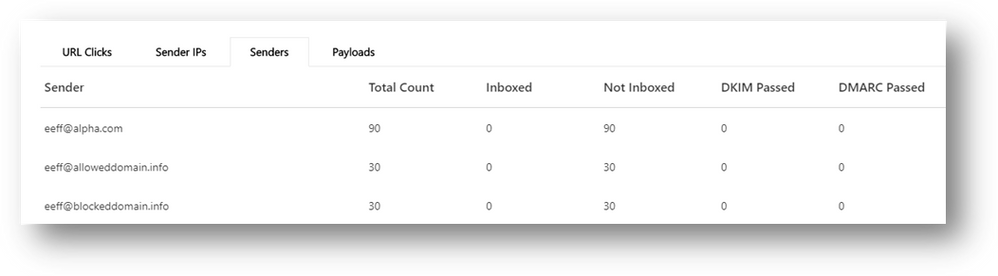
- See the list of IP addresses and senders used to orchestrate the attack.
- Assess which messages were blocked, ZAPped, delivered to junk or quarantine, or allowed into the inbox.
- See all the URLs that were manifested in the attack
- Learn if there are users that have fallen prey to any attacks and clicked on the phish URL.
Armed with the information above security teams can more effectively and efficiently:
- Remediate compromised/vulnerable users
- Improving security posture by eliminating configuration flaws seen
- Investigate related campaigns that use the same indicators of compromise
- Hunt and track threats that use the same indicators of compromise
Amazing feedback:
Over the past few months, in public preview we’ve had extremely positive feedback on the feature.
“Being able to piece together the big picture of phishing attacks spread out over multiple days and with subtle changes in tactics of the campaigns, is extremely powerful”
“I’ve now started using this as one of the starting points for my hunting and investigation. And I keep coming back every few days to see what’s new and what I need to focus on”
Comments like the above are music to our ears and we’ve been hearing it from many customers that have been using Campaign Views in preview.
Tangible value:
It is no wonder that customers love this feature. Just consider the following stories.
For one large customer, visibility into the complexity of a small number of recurring, detected campaigns helped them identify and understand a set of persistent, targeted attacks against a specific R&D department.
Another tenant prioritized a full review of their decade-old configuration settings after they saw a campaign that completely bypassed filtering and allowed message delivery into their organization. It turns out that the campaign was allowed by a previously unknown and unrecognized Exchange mail flow rule (also known as a transport rule or ETR).
As we engage with customers, we continue to hear stories like this that make using campaign views as part of the SecOps workflows extremely compelling.
Additional improvements:
As part of the GA release we’ve also made additional improvements to Campaign views.
Improved discoverability: Campaign views are a separate node in the left navigation panel of the O365 Security and Compliance portal under ‘Threat Management’.
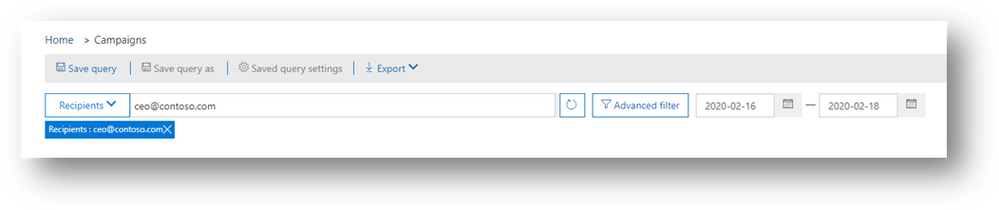
Expanded search and investigation capabilities: We’ve made it easier to search across campaigns. For example, you can search for all campaigns that targeted a specific recipient (for example, your company’s CEO) or campaigns related to a particular email (search for subject keywords or the specific messageID).
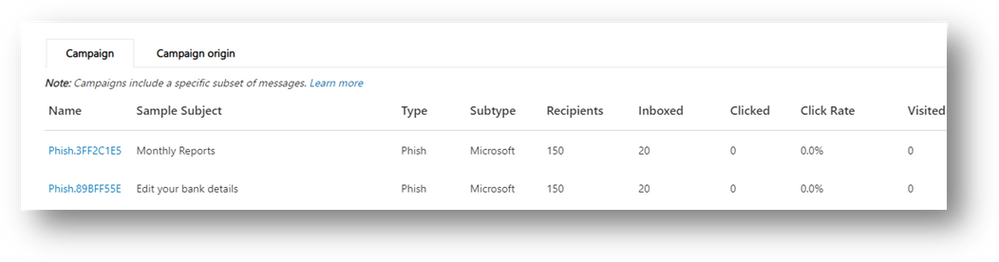
More campaign details: For each campaign, more included more information is presented.
- Click-rate: As a way to measure the effectiveness of the campaign (from an attackers perspective), or in other words the impact of the campaign on the organization, we now show off a click-rate. Click-rate shows the percentage of Inbox’ed messages (messages delivered to the Inbox) that received a click from the recipient. This is an indirect measurement how effective and convincing the social engineering aspect of the campaign was.
- Authentication details: Within the Campaign view, we show expanded authentication details: all email authentication protocols (SPF for sending IPs, DKIM and DMARC for senders). Authentication failures identify attackers that are spoofing senders. Passing these authentication checks indicates a legitimate email sending infrastructure is being used for these attacks (for example, compromise or abusive activities that would require different action plans).
Campaign Views is GA!
Campaign Views will be immediately available to all customers with Office 365 ATP P2 and Office 365 E5 subscriptions. We encourage you to start using this powerful new set of capabilities to understand, mitigate and remediate phishing attacks. To learn more, see Campaign Views in Office 365 ATP.
Advanced Compromised user detection and response:
User accounts continue to have immense value for attackers. By compromising an account the attacker gains a foothold into the organization, using which they look to proliferate the attack, build avenues for the delivery of additional spam and phish campaigns, target additional users within the organization, steal sensitive data, or hold the organization to ransom.
This is why organizations need a sound protection strategy that focuses not only on prevention, but also early detection and response of account compromise and breaches.
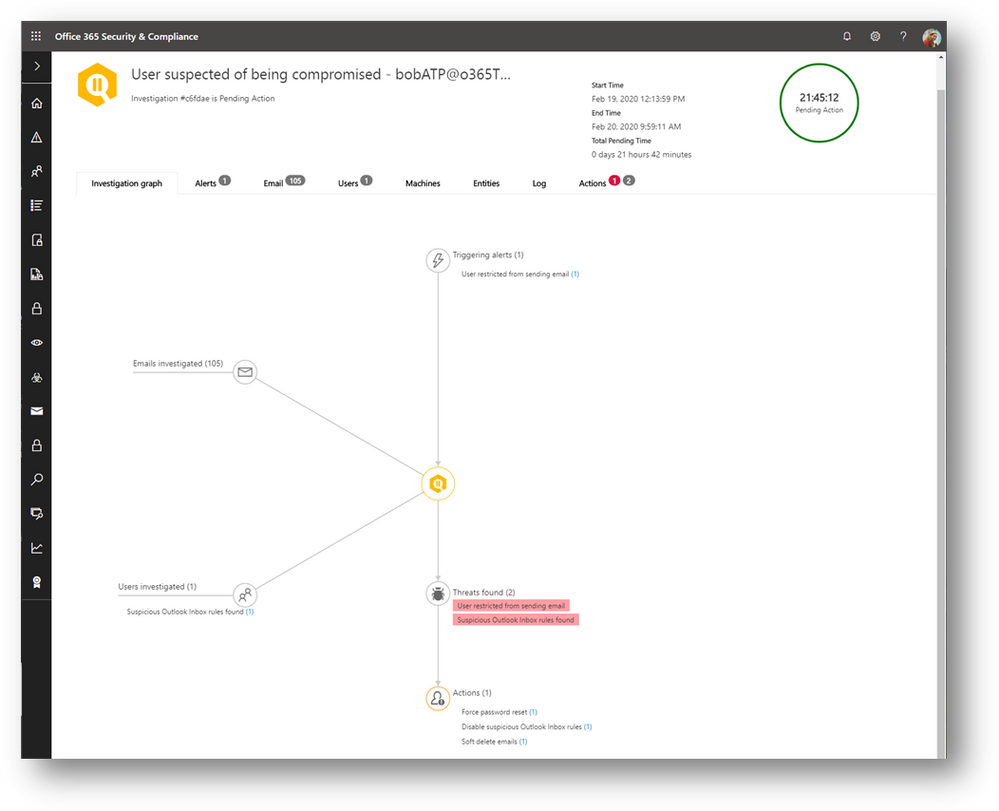
The attacker’s activities when using a compromised account are often atypical or anomalous relative to the user’s regular behavior. For instance, there is no good reason for trusted users to be sending any phish or spam emails to other recipients. Being able to detect anomalies in user activity is therefore a key signal source for detection.
A few months ago, we released several features to detect anomalies in user activity to expand on our detection of user compromise. And we also released into preview a compelling automated playbook to automatically investigate such threats to help security teams more effectively and comprehensively detect the source and impact of the compromise and take remediation actions.
Amazing impact:
The power of these new capabilities has been immediately apparent. In the past few months, we’ve seen a 5x increase in the number of user compromises detected and responded to by customers using this feature.
If you consider the average cost of a data breach to organizations (~$4M globally, per some studies), with estimates being higher in certain geographies (some estimates reaching as high as $10M in regions like the US), any time security teams can detect and respond to compromised users faster and prevent costly data-breaches, is a critical win for the organization, their employees, their partners and customers.
Continuous stream of improvements:
As a lead up to GA, we’ve also been working to continually expand and tun our detections to more accurately detect compromise, highlight exfiltration of data and improve the efficiency of SecOps teams. While this GA announcement marks a compelling checkpoint to leverage this feature more confidently, we’ll continue to expand on the types of detections and SecOps capabilities we’ll introduce into this feature.
Compromise user detection and response is GA!
The compromise detections and alerts are available to all customers. The advanced automated playbooks for automatic investigation and response of compromised users for a more effective and efficient analysis of the cause and impact of the compromise is generally available today to all customers with Office365 ATP P2 and Office365 E5 subscriptions. We encourage you to start using this powerful new set of capabilities to stop attack kill-chains early and reduce the impact and scope of breaches. To learn more, see the documentation related to compromised user response
Try it for yourself!
If you’ve not checked out these capabilities yet, I strongly encourage you to do so. The combination of campaign views and compromise user detection and response helps reduce the scope of impact of breaches by giving security teams the tools to detect compromised users sooner, identify configuration weaknesses easily, respond faster and more effectively and improve security posture. Go on, give it a try. We’d love to hear what you think.
Related Posts
The above was provided from Microsoft Security and Compliance blogs at TechCommunity


![[UPDATED] Introducing remote deployment guidance for Microsoft Defender ATP and Office 365 ATP](/wp-content/plugins/related-posts/static/thumbs/27.jpg)













