The following is provided from Microsoft Security and Compliance blogs at TechCommunity:
Overview
Attack Surface Analyzer has been a valuable asset to software developers and IT security personnel for years in helping detect key system changes that may occur from software installations. We’re pleased to announce the release of Attack Surface Analyzer 2.0 earlier this month, which is a new .NET Core and Electron rewrite of the classic 2012 version of the tool, and is one of several tools recommended from Microsoft SDL Practices which can help improve customer trust in software.
Attack Surface Analyzer 2.0 helps identify potential security risks introduced by new or untrusted software by detecting changes to key areas of the system security configuration including:
- File System
- User Accounts
- System Services
- Network Ports (listeners)
- System Certificate Store
- Windows Registry
It includes static change detection between snapshots of these key areas and a real-time file change monitoring option as well as an export feature of analysis data which is stored in a local SQLite database file. Additional collection types and improvements are planned to be released later this year.
It also includes both a scriptable command line interface (CLI) and an Electron option and even allows for your own custom front end to call the underlying core components programmatically to create an entirely different or white label client experience. The entire codebase has been released as an Open Source project on GitHub allowing developers to further extend the tool features themselves and contribute them to the community. A key improvement over the classic version is the application now comes with cross-platform support for Windows, Linux and macOS.
Usage
Attack Surface Analyzer allows you to create “snapshots” before and after you install the target software under consideration. A clean initial system with minimal additional software is ideal, but not required though it does require administrator user privileges to use fully .
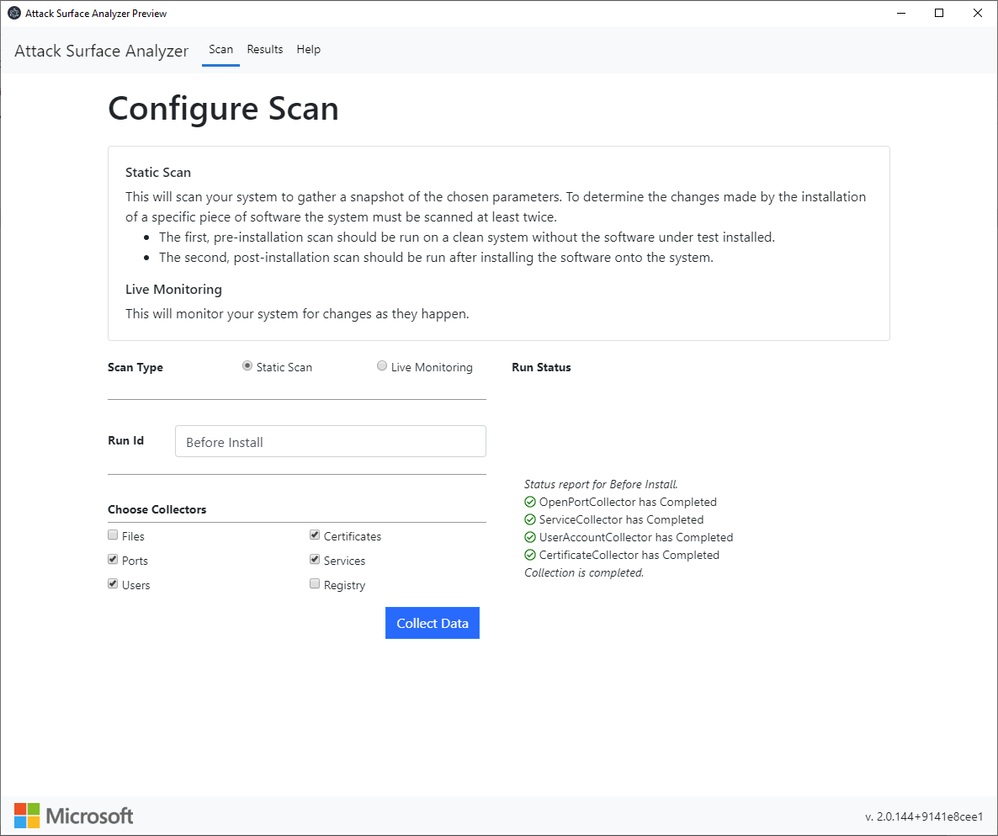
Let’s say you want to detect system changes made from the installation of a software application e.g. Firefox. After downloading Attack Surface Analyzer, you can use the Electron GUI option and select Start or Scan to create a baseline initial snapshot labeling it “Before Install” or “Clean System” for example and allowing the scan to complete.
Next, install your software and run a new scan labeling it “After Install” for example and selecting the same collector types used in the initial scan.
Note: you can also run additional scans to capture changes made while using the software beyond just the installation.
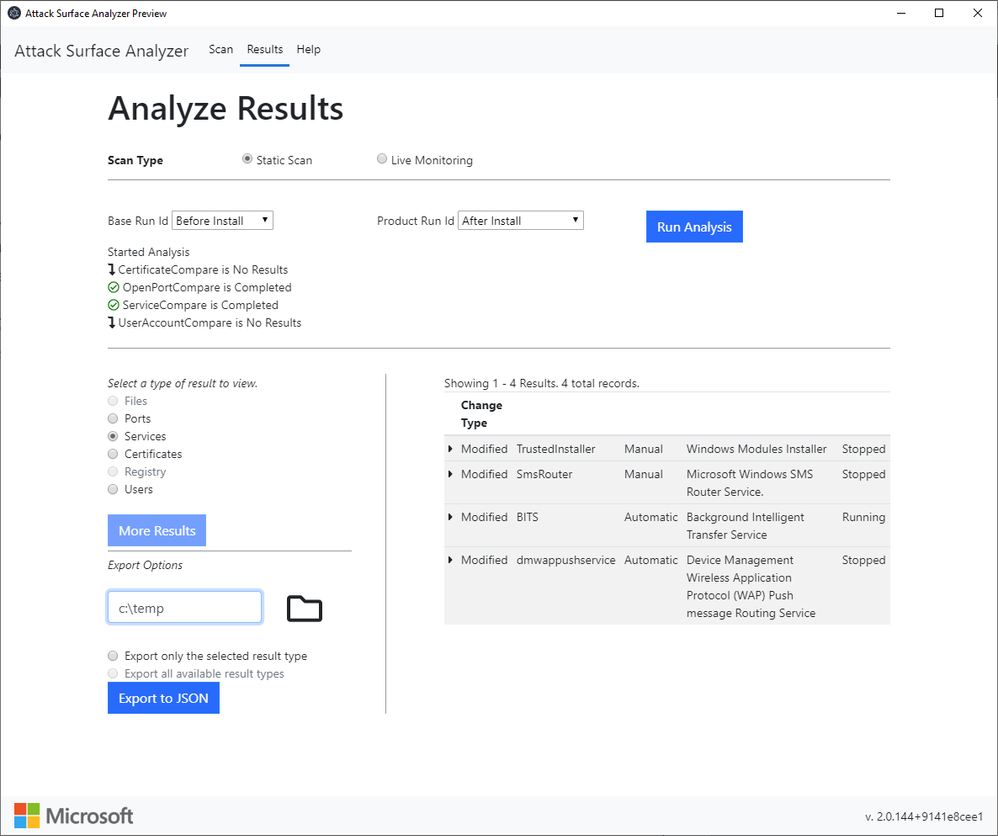
Then use the Analyze Results feature selecting both the initial and post install scans that were previously saved to analyze for changes or selecting any two scans for comparison. Finally, choose a desired filter to view any unexpected and potentially security impactful changes that were made.
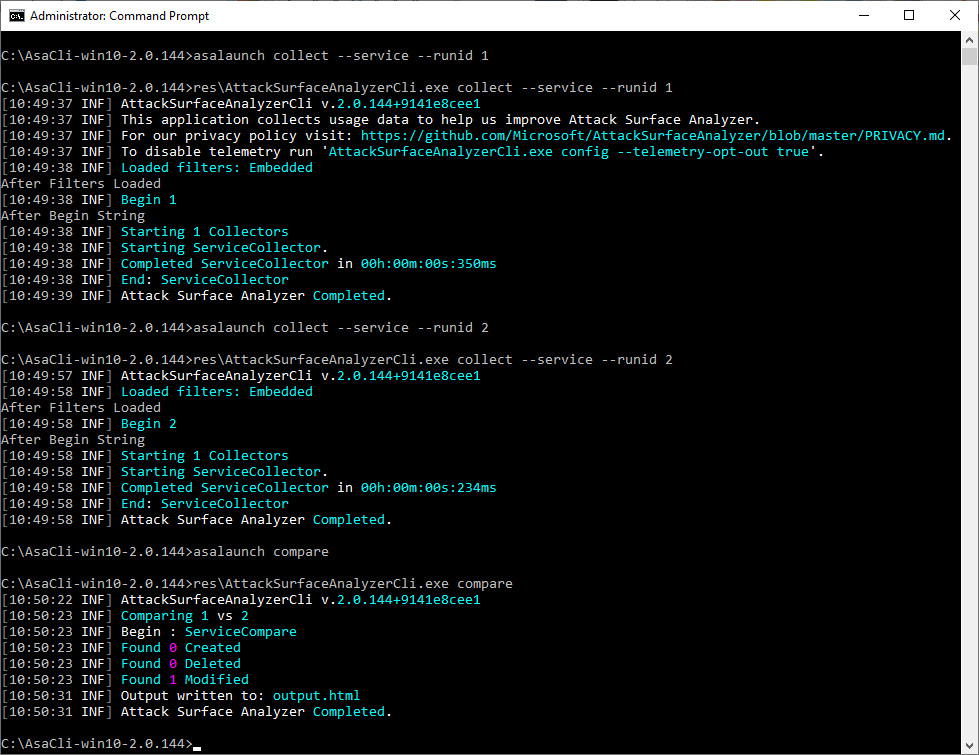
Alternatively, use the CLI interface which comes with command line help and the same level of functionality or greater in some cases, and which can be scripted into your build or other processes.
Software Development Lifecycle Role
Attack Surface Analyzer contributes as an important software development best practice helping ensure the use of least privilege in your own software products for minimizing unwanted attack surface changes to your customers systems. The output options can provide evidence for release management and security auditors that your product does only what it claims in addition to scanning for 3rd party software installation changes to your system.
As maintaining customer trust is key, including Attack Surface Analyzer 2.0 in your development processes or toolchain is a great idea. Future releases of the tool will also include security guidance help for identified changes that may warrant additional scrutiny.
Getting Started
To get started, visit the project site on Github at https://github.com/Microsoft/AttackSurfaceAnalyzer and download the latest release. We value your feedback, bug reports, and ideas and are excited by the release of this valuable tool for contributing to security compliance needs.
Related Posts
The above was provided from Microsoft Security and Compliance blogs at TechCommunity




![[UPDATED] Introducing remote deployment guidance for Microsoft Defender ATP and Office 365 ATP](/wp-content/plugins/related-posts/static/thumbs/27.jpg)









